KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







This week, it has been busy with attacks worldwide and one of the largest ransomware operations officially shutting down.
The week started with the official announcement from the infamous Maze operation that they were shutting down. BleepingComputer has learned that many of the affiliates are now moving over to a newer ransomware operation called Egregor.
We also learned of a new ransomware called RegretLocker that uses the Windows Virtual Storage APIs to mount virtual machine hard disks (VHDs) to encrypt each file contained in them individually.
Finally, we saw attacks on game developer Capcom, liquor make Campari, and a wide-scale assault on the Brazilian government networks.
Contributors and those who provided new ransomware information and stories this week include: @fwosar, @Ionut_Ilascu, @VK_Intel, @demonslay335, @PolarToffee, @BleepinComputer, @DanielGallagher, @Seifreed, @LawrenceAbrams, @serghei, @malwrhunterteam, @FourOctets, @struppigel, @malwareforme, @jorntvdw, @_CPResearch_, @pancak3lullz, @Securelist, @BitMateus, @coveware, @smelly__vx, @campuscodi, @MarceloRivero, @M_Shahpasandi, @Amigo_A_, and @Kangxiaopao.
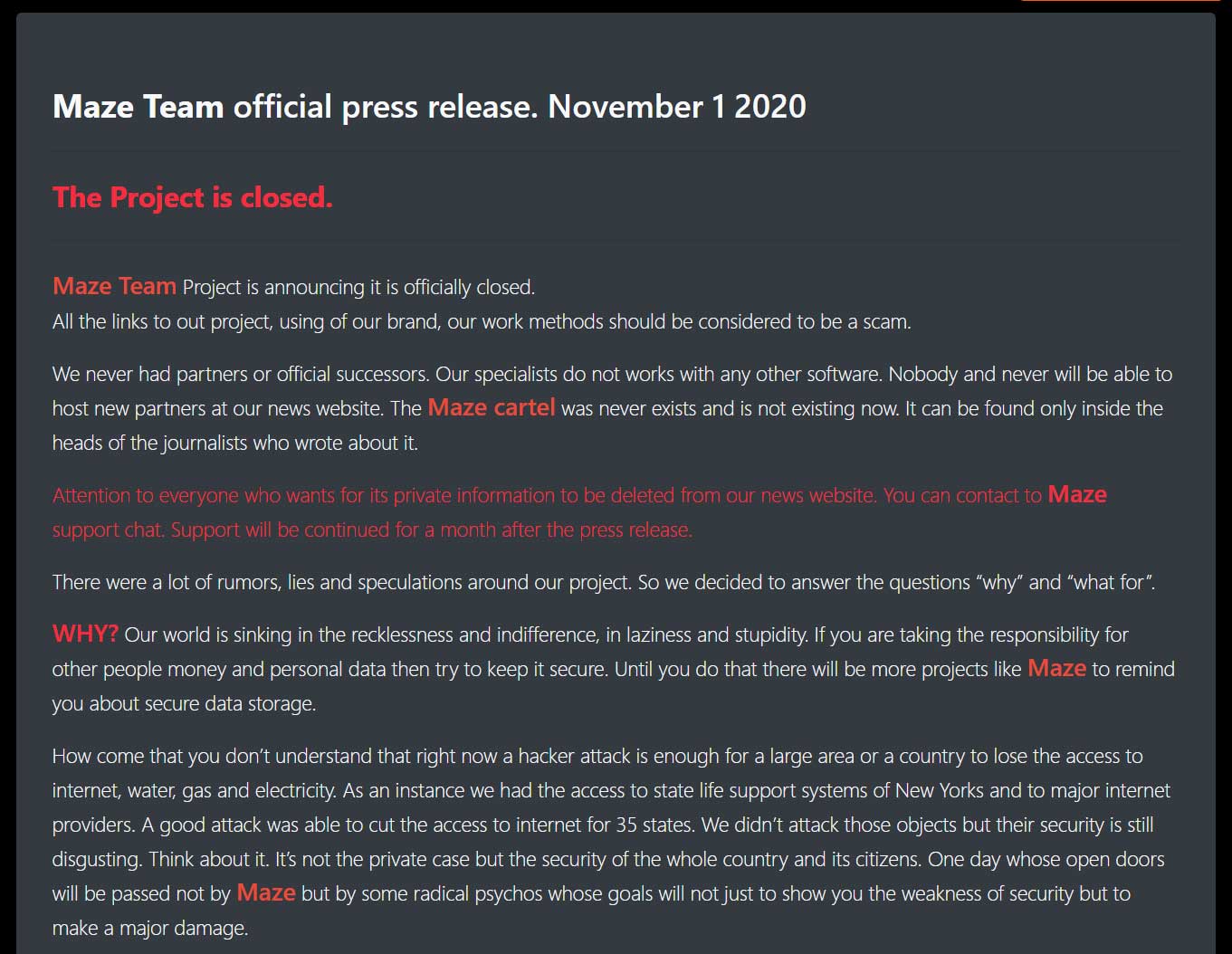
The infamous Maze ransomware gang announced today that they have officially closed down their ransomware operation and will no longer be leaking new companies’ data on their site.
Also Read: Data Centre Regulations Singapore: Does It Help To Progress?
MalwareHunterTeam found a new Jigsaw Ransomware variant that appends the .evil extension.
Toy industry giant Mattel disclosed that they suffered a ransomware attack in July that impacted some of its business functions but did not lead to data theft.
A new ransomware called RegretLocker uses a variety of advanced features that allows it to encrypt virtual hard drives and close open files for encryption.
Leading cloud software provider Blackbaud has been sued in 23 proposed consumer class action cases in the U.S. and Canada related to the ransomware attack that the company suffered in May 2020.
Also Read: What Is A Governance Framework? The Importance And How It Works
Ransomware gangs are increasingly failing to keep their promise to delete stolen data after a victim pays a ransom.
The Coveware Quarterly Ransomware Report describes ransomware incident response trends during Q3 of 2020. Ransomware groups continue to leverage data exfiltration as a tactic, though trust that stolen data will be deleted is eroding as defaults become more frequent when exfiltrated data is made public despite the victim paying. In Q3, Coveware saw the Maze group sunset their operations as the active affiliates migrated to Egregor (a fork of Maze). We also saw the return of the original Ryuk group, which has been dormant since the end of Q1.
Ransomware gang who claims to have earned $100 million buys the source code of the KPOT information stealer trojan for $6,500.
Michael Gillespie found a new variant of the STOP ransomware that appends the .vpsh extension to encrypted files.
Toffee discovered that Lock2Bits is rebranding as LuckyDay. The ransomware uses the .luckyday extension and a ransom note named File Recovery.txt.
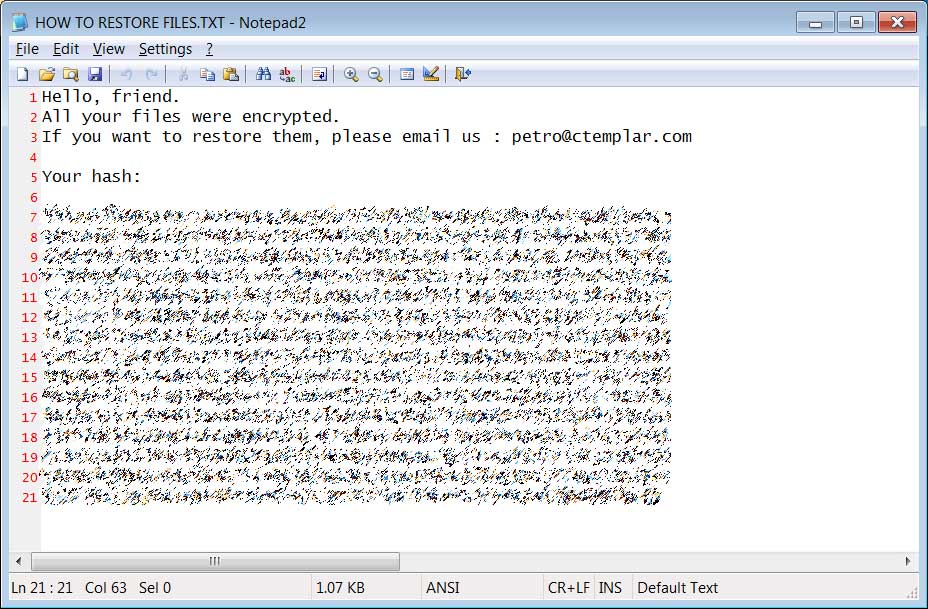
Michael Gillespie found a new variant of the DCRTR ransomware that appends the .termit extension to encrypted files.
M. Shahpasandi found a GlobeImposter 2 variant that appends the .CC4H extension.
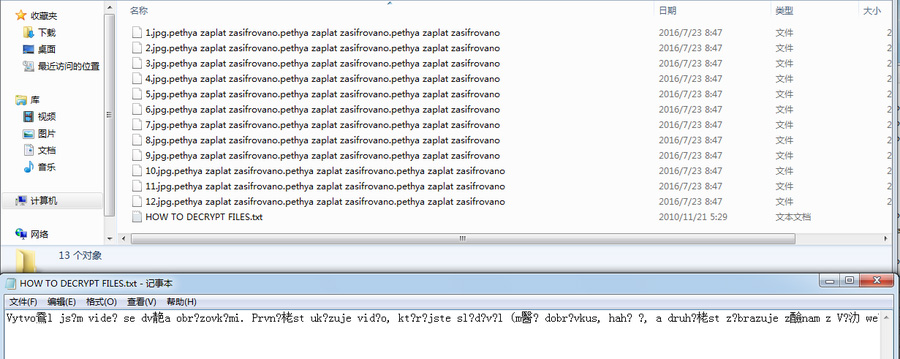
xiaopao found a new ransomware that appends the strange extension of .pethya zaplat zasifrovano.pethya zaplat zasifrovano.pethya zaplat zasifrovano.
Japanese game developer Capcom has suffered a ransomware attack where threat actors claim to have stolen 1TB of sensitive data from their corporate networks in the US, Japan, and Canada.
Italian liquor company Campari Group was hit by a Ragnar Locker ransomware attack, where 2 TB of unencrypted files was allegedly stolen. To recover their files, Ragnar Locker is demanding $15 million.
Brazil’s Superior Court of Justice was hit by a ransomware attack on Tuesday during judgment sessions that were taking place over video conference.
Babax not only changes its name but also adds a Ring 3 rootkit and lateral spreading capabilities. Furthermore it has a ransomware component called OsnoLocker. Is this combination as dangerous as it sounds?
Michael Gillespie found a new ransomware called Tripoli that appends the .crypted extension and drops a HOW_FIX_FILES.htm ransom note.
Marcelo Rivero found a new ransomware called LockDown that appends the .sext and drops a ransom note named HELP_DECRYPT_YOUR_FILES.txt.
xiaopao found a new Vaca ransomware variant that appends the .locked3dllkierff extension.
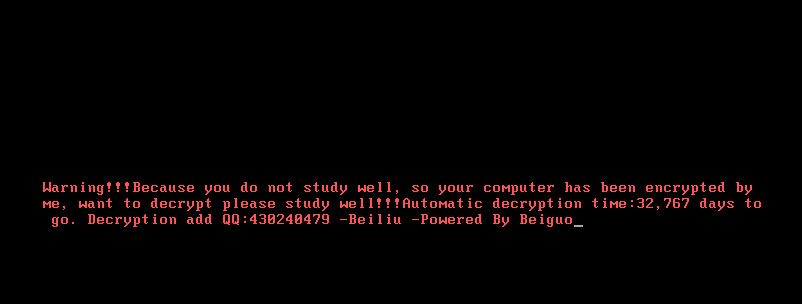
xiaopao found a new MBRLocker that is “Powered by Beiguo.”
A new ransomware called Pay2Key has been targeting organizations from Israel and Brazil, encrypting their networks within an hour in targeted attacks still under investigation.
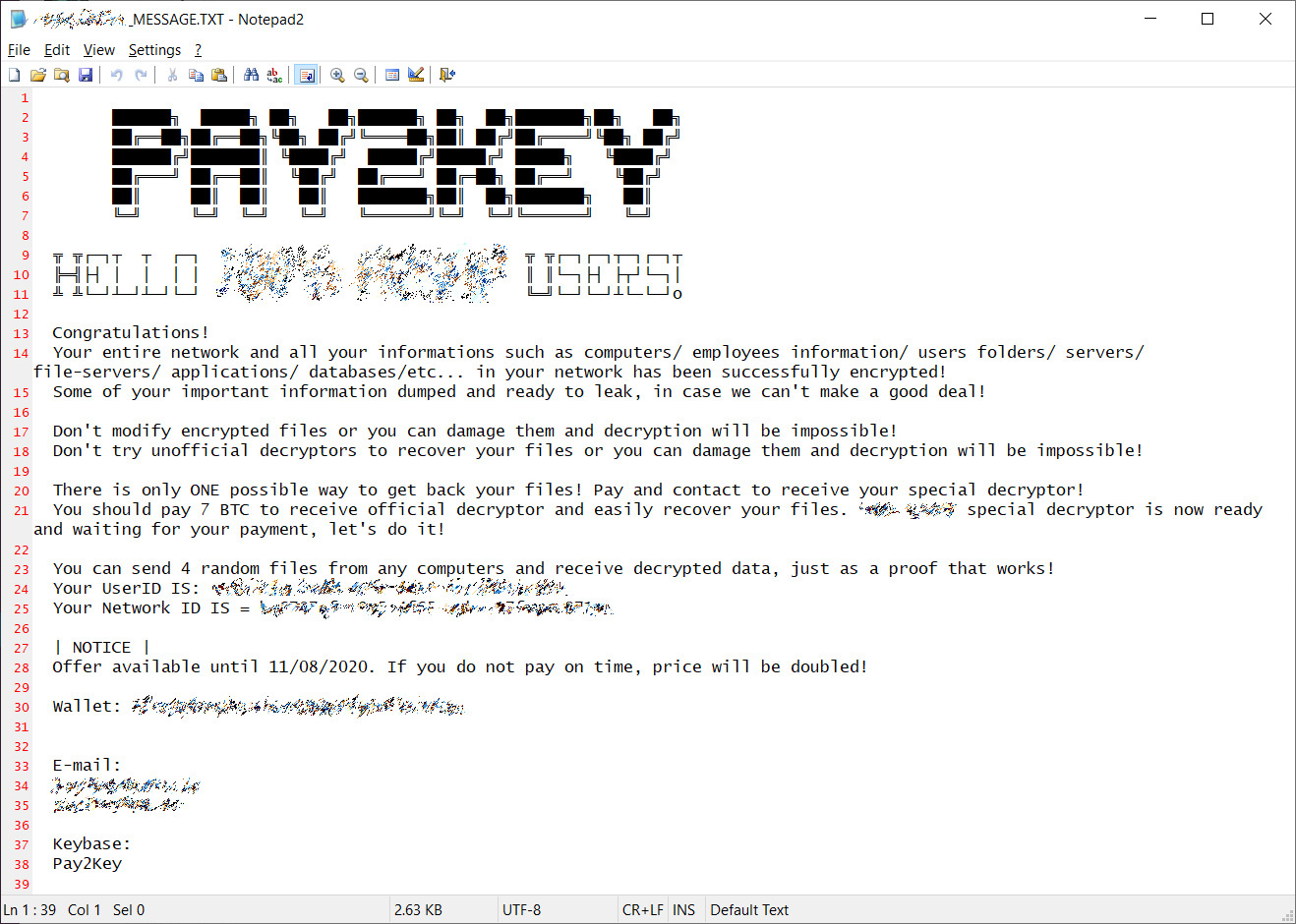
With companies commonly using a mixed environment of Windows and Linux servers, ransomware operations have increasingly started to create Linux versions of their malware to ensure they encrypt all critical data.
Michael Gillespie found a new Dharma ransomware variant that appends the .zimba extension to encrypted files.
Michael Gillespie found a new ransomware called RexCrypt that appends the .RexCrypt extension and drops a ransom note named How-To-Decrypt-My-Files.hta.
Michael Gillespie found a new Nefilim ransomware variant that appends the .FUSION extension and drops a ransom note named FUSION-README.txt.