KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Researchers can now find the developer of a specific Windows exploit using a new “fingerprinting” technique specifically devised to keep track of exploit developers’ activity.
More to the point, Check Point security researchers Itay Cohen and Eyal Itkin were able to track 16 Windows Kernel Local Privilege Escalation (LPE) exploits to two different exploit developers known as Volodya (or BuggiCorp) and PlayBit (or luxor2008).
15 of the exploits Check Point successfully matched to a known exploit dev were created between 2015 and 2019, potentially making up a notable share of the overall Windows LPE exploitation market at the time.
Their method involves looking for uncommon source code identifiers that can be associated with a specific exploit writer such as unique artifacts (such as strings, hardcoded values, and PDB paths), coding habits and techniques, code snippets, and framework info.
“Assuming that exploit authors work independently, and only distribute their code/binary module to the malware authors, we decided to focus on them for a change,” Check Point says in a report shared earlier this week with BleepingComputer.
“By analyzing the exploits embedded in malware samples, we can learn more about the exploit authors, hopefully distinguishing between them by studying their coding habits and other fingerprints left as clues on their identity, when distributing their products to their malware writing counterparts.”

Using hunting rules based on a few never before seen exploit functions extracted from a single malware sample, Check Point was able to quickly track down dozens of other samples containing code written by the same developer.
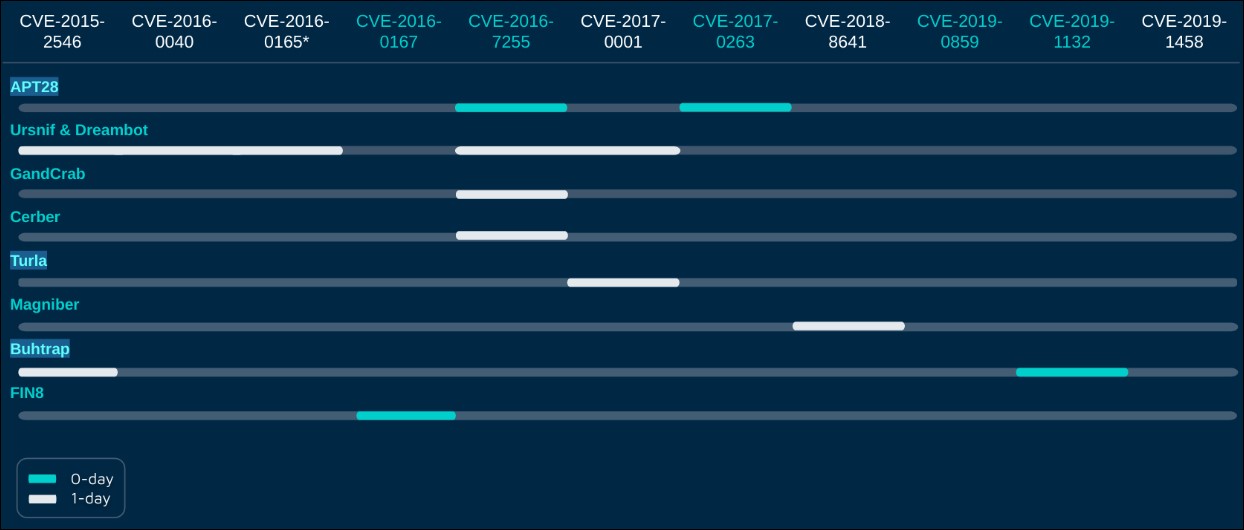
By matching samples to the vulnerabilities they exploited, the researchers were able to track the author of 10 different 0-day and 1-day Windows LPE exploits, later exposed by public reports [1, 2] as Volodya, an exploit developer known for selling 0-days to cybercrime and Russian APT groups.
“The list of Volodya’s clients is diverse and includes banker trojan authors such as Ursnif, ransomware authors such as GandCrab, Cerber and Magniber, and APT groups such as Turla, APT28 and Buhtrap (which started from cyber-crime and later shifted to cyber-espionage),” the reports reads.
“Interestingly, we can see that Volodya’s 0-days are more likely to be sold to APT groups while 1-days are purchased by multiple crimeware groups.”
Also Read: The Importance Of Knowing Personal Data Protection Regulations
Volodya’s customers (Check Point)
The same discovery technique allowed them to track down 5 Windows LPE 1-Day exploits as being developed by PlayBit after starting from a single malware sample used by REvil ransomware to compromise systems vulnerable to CVE-2018-8453.
PlayBit sold the exploits Check Point spotted to the REvil and Maze ransomware gangs, two infamous ransomware groups known for extorting their victims out of millions of dollars.
Check Point researchers’ exploit “fingerprinting” technique can be used for other goals besides identifying an exploit’s developer.
By pinpointing an exploit’s author using a technique similar to that used when tracking APT groups and malware devs, researchers can also:
“This research provides rare insight into how the ‘black exploit market’ works,” Check Point malware researcher Itay Cohen said.
“Based on these two successful test cases, we believe that this research methodology can be used to identify additional exploit writers.
“We recommend other researchers try our suggested technique and adopt it as an additional tool in their arsenal,” he added.
More information the methodology used as part of this research and full technical details can be found within Check Point’s report.
The research will also be presented today at the Virus BulletinVB2020 localhost virtual conference as part of the “Graphology of an exploit – hunting for exploits by looking for the author’s fingerprints” presentation.
Also Read: 13 Special Skills To Become A Front End Developer Singapore