KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





New research released today provides greater insight into the Emotet module created by law enforcement that will uninstall the malware from infected devices in April.
On January 27th, Europol announced that a joint operation between law enforcement agencies from Netherlands, Germany, the United States, the United Kingdom, France, Lithuania, Canada, and Ukraine took control of the Emotet botnet’s servers and disrupted the malware’s operation.
After the takedown, researchers noticed that the Emotet botnet began to push down a module to infected devices that would uninstall the malware on April 25th, 2021, at 12:00 and later.
On the 28th, it was confirmed in a US Department of Just press release that “foreign law enforcement” created this module.
“Foreign law enforcement, working in collaboration with the FBI, replaced Emotet malware on servers located in their jurisdiction with a file created by law enforcement, according to the affidavit. This was done with the intent that computers in the United States and elsewhere that were infected by the Emotet malware would download the law enforcement file during an already-programmed Emotet update,” states a Department of Justice press release.
In a conversation with Europol and later emails with Germany’s Bundeskriminalamt (BKA) federal policy agency, we learned that the BKA was responsible for the module.
“Within the framework of the criminal procedural measures carried out at international level, the Bundeskriminalamt has arranged for the malware Emotet to be quarantined in the computer systems affected. An identification of the systems affected is necessary in order to seize evidence and to enable the users concerned to carry out a complete system clean-up to prevent further offences. For this purpose, the communication parameters of the software have been adjusted in a way that the victim systems no longer communicate with the infrastructure of the offenders but with an infrastructure created for the seizure of evidence.” – German Bundeskriminalamt
Also Read: A Look at the Risk Assessment Form Singapore Government Requires
While we now knew that the moduled pushed down to infected devices was created by law enforcement to uninstall the malware, there were still some questions unanswered.
For example, why was the uninstall occurring two months away, and what happens before the April 25th, 2021 uninstall date?
Today, a new analysis by Jérôme Segura and hasherezade of Malwarebytes answers some of these questions.
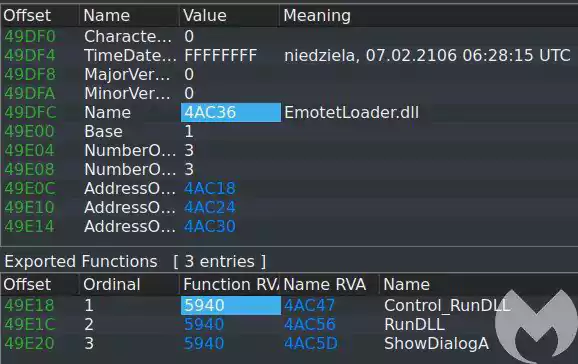
The new Emotet module distributed by German law enforcement is a 32-bit DLL named ‘EmotetLoader.dll.’
Below you can see the routine that checks for the date, and if it’s April 25th or later, removes Emotet. For more information about the deadline variable, you can reference this Microsoft documentation.
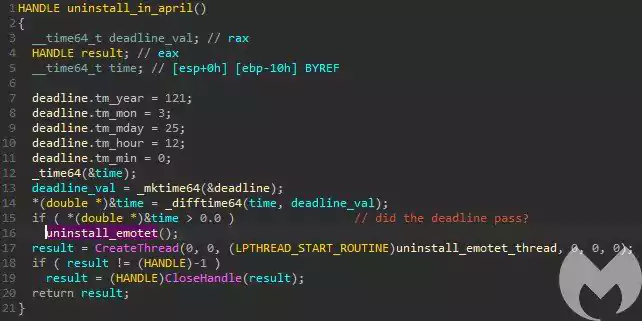
When removing Emotet, Malwarebytes states the uninstaller deletes only the associated Windows services, deletes its autorun Registry key, and then exits the process.
On the other hand, prior to April 25th, 2021, the module allows Emotet to be installed on the device.
However, the difference is that the Emotet command and control server is now configured to use law enforcement servers located in Germany. As law enforcement controls the botnet, Emotet will not download further modules to the infected PC to perform malicious activity.
“Well, it still loads Emotet but with a big difference. It swaps the C2s for those controlled by LE. So your machine, while it waits for the cleanup to activate, will ping LE servers.” Segura told BleepingComputer.
Malwarebytes states that this new module will be pushed down to all infected devices, effectively replacing the malicious Emotet installs already infecting their computers.
“For victims with an existing Emotet infection, the new version will come as an update, replacing the former one. This is how it will be aware of its installation paths and able to clean itself once the deadline has passed,” explains Malwarebytes.
What is still not answered is why wait two months to uninstall the malware rather than doing it immediately?
Based on the BKA’s statement, it is likely being done to allow law enforcement to gather further evidence, such as the number of infected devices infected and what countries these devices are located. It could also be used to identify corporate victims to warn them of further pontential compromises of their networks.
BleepingComputer’s attempts to get official answer to this question has been unsuccessful.
Also Read: How to Send Mass Email Without Showing Addresses: 2 Great Workarounds
“Please understand that we cannot provide any further information as the investigations are still ongoing,” the German BKA told BleepingComputer in response for more information.