KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







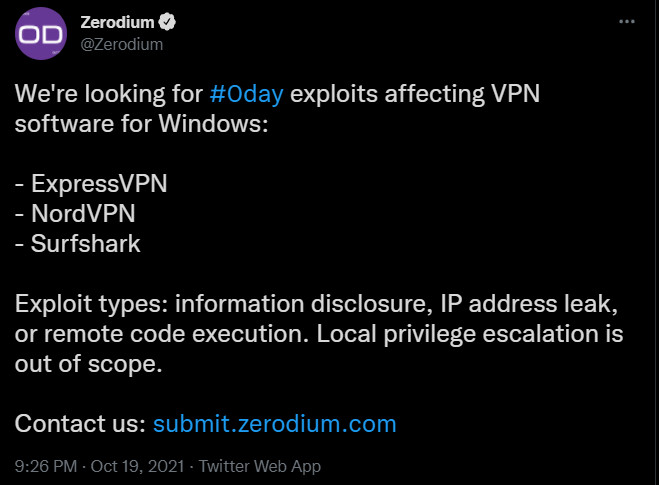
In a short tweet today, exploit broker Zerodium said that it is looking to acquire zero-day exploits for vulnerabilities in three popular virtual private network (VPN) service providers on the market.
VPN services allow you to hide your IP address when accessing resources on the internet by running the connection through the provider’s servers.
This routing makes it more difficult for third parties to track your activity online, increasing the privacy on the internet.
Also Read: Top 3 Common Data Protection Mistakes, Revealed
Zerodium’s current interest is in vulnerabilities affecting Windows clients for NordVPN, ExpressVPN, and SurfShark VPN services. Together, they serve millions of users, the first two reportedly claiming at least 17 million users around the globe.
According to data on their sites, the three companies manage more than 11,000 servers spread over tens of countries.
The vulnerability broker’s announcement today called for bugs that could reveal information about users, their IP addresses, and vulnerabilities that can be used to achieve remote code execution. One type of flaw that the broker does not want is local privilege escalation.
BleepingComputer reached out to the three VPN service providers for comment on Zerodium’s announcement but did not receive a reply at publishing time.
Zerodium’s customer base is formed of government institutions, primarily from Europe and North America, that need advanced zero-day exploits and cybersecurity capabilities.
The reason behind the exploit broker’s announcement remains undisclosed but one motive could be that government customers need a way to identify cybercriminal activity hiding behind VPN services.
NordVPN and Surfshark have been used by threat actors in the past.
Last year, the Federal Bureau of Investigation (FBI) alerted of Iranian hackers using the NordVPN service to run a fake Proud Boys campaign.
Also Read: The Financial Cost of Ransomware Attack
A more recent example is from the National Security Agency (NSA) this year, who warned that Russian hackers launched brute-force attacks against Kubernetes servers with their origin concealed through TOR and VPN services, among them Surfshark and NordVPN.
The company says that its business is guided by ethics and selects customers based on strict criteria and vetting processes; and that only a small number of government clients have access to acquired zero-day research.
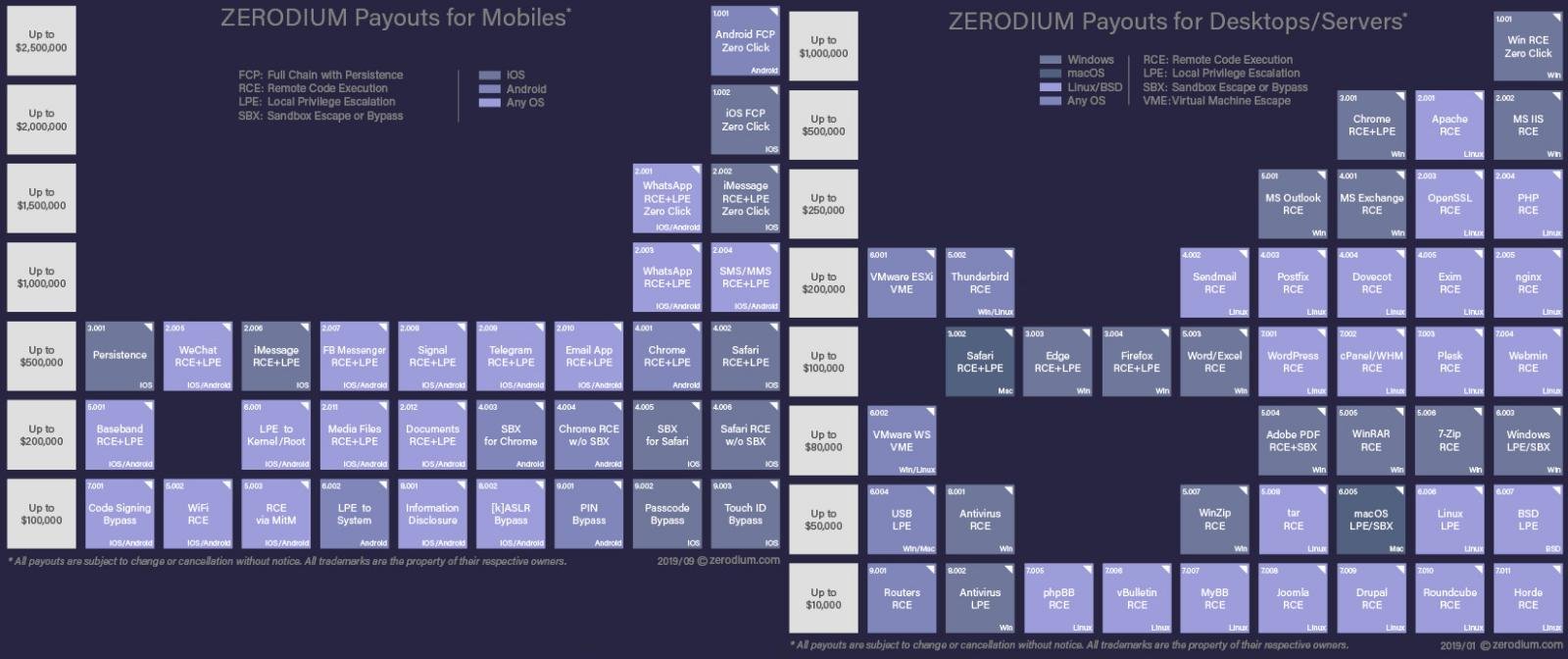
Earlier this year Zerodium announced a temporary payout increase for Chrome exploits. Zerodium offered $1,000,000 for an exploit that chained remote code execution (RCE) with sandbox escape (SBX).
Separately, the bounties for RCE and SBX in Chrome were increased to $400,000 each. These payouts are still active at the time of writing.
Zerodium offers payouts for any operating system for both mobile and desktop platforms. The largest are for Windows, macOS, LinuxBSD, iOS, and Android.
BleepingComputer reached out to Zerodium for further information about its interest in exploits for VPN clients for Windows but did not hear back at publishing time