KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Security researchers have created exploit code for CVE-2022-24086, the critical vulnerability affecting Adobe Commerce and Magento Open Source that Adobe that patched in an out-of-band update last Sunday.
The vulnerability, which Adobe saw being “exploited in the wild in very limited attacks,” received a severity score of 9.8 out of 10 and adversaries exploiting it can achieve remote code execution on affected systems without the need to authenticate.
Earlier today, Adobe updated its security advisory for CVE-2022-24086 adding a new issue that is now tracked as CVE-2022-24087, which has the same severity score and can lead to the same result when leveraged in attacks.
Both are Improper Input Validation vulnerabilities and the company released patches for Adobe Commerce and Magento Open Source to address the two security issues.
Also Read: Top 8 Main PDPA Obligations To Boost And Secure Your Business
In a tweet today, the Offensive Team of cybersecurity company Positive Technologies announced that they created a reliable exploit for CVE-2022-24086.
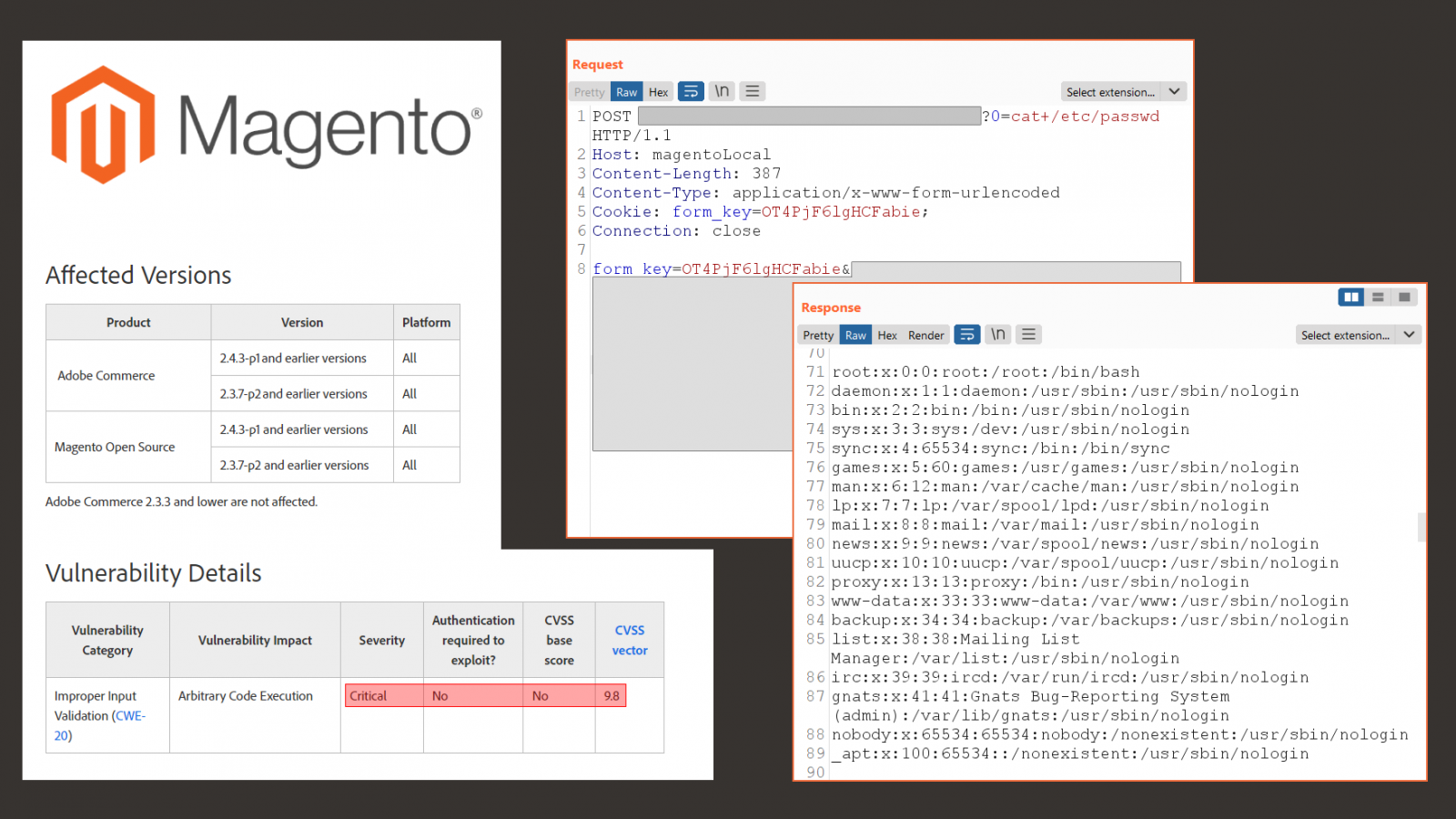
The researchers told BleepingComputer that attackers leveraging the bug can get “full access to the target system with web-server privileges.”
They are warning that trying to block exploitation attempts by setting up a web application firewall (WAF) is not a reliable solution because there are multiple ways to leverage the bug, “without specific and non-removable constructions in the request.”
Positive Technologies researchers told us that developing “a complete exploit is quite a difficult task” if technical details are not available. However, once this obstacle is eliminated, attacking vulnerable targets “is quite straightforward and simple.”
However, threat actors are not to be underestimated. Even if it takes them longer to come up with an exploit, motivated adversaries will invest the effort to develop it.
Online stores are a prime target for financially-driven hackers that are after payment card data, typically captured by a web skimmer – a malicious script injected into payment forms.
Furthermore, as Adobe noted in their advisory, some threat actors are already leveraging CVE-2022-2408 in limited attacks.
Also Read: 5 Tips In Using Assessment Tools To A Successful Businesses
According to the researchers’ estimations, there are more than 17,000 vulnerable websites, some of them from “major businesses.”
The researchers say that they have no plans to publish the proof-of concept (PoC) exploit code they created or to share it privately within the infosec industry.
The decision is primarily motivated by the significant number of websites running unpatched Adobe Commerce and Magento products.
Online store administrators are recommended to install the patches for both critical vulnerabilities to defend exploitation attempts.
Credited for the second critical bug (CVE-2022-24087) are researchers Eboda and Blaklis, the latter stressing that applying the first fix is not sufficient: