KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The PurpleFox botnet has refreshed its arsenal with new vulnerability exploits and dropped payloads, now also leveraging WebSockets for C2 bidirectional communication.
Although it’s mainly based in China, the PurpleFox botnet still has a global presence through hundreds of compromised servers.
Its activity starts with the execution of a PowerShell command that downloads a malicious payload from the specified URL, pointing to an available C2 server.
The payload used in recent campaigns tracked by researchers at Trend Micro is a long script that comprises three privilege escalation components.
Also Read: PDPA Compliance Singapore: 10 Areas To Work On
These target Windows 7 to Windows 10 systems, but are limited to 64-bit systems only.
The flaws that are exploited by the latest PurpleFox variants are the following:
PurpleFox detects the host system, selects the appropriate exploit, and then uses the PowerSploit module to load it.
An MSI package is also initiated from an admin-level process without requiring any user interaction, checking for older PurpleFox installations and replacing their components with new ones.
The backdoor that is installed on the host system is a DLL file obfuscated with the VMProtect file compressing utility.
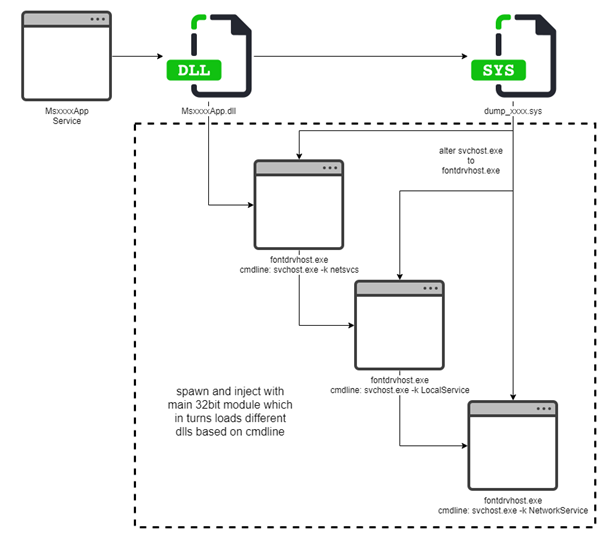
The malware also uses a rootkit driver that hides its files, registry keys, and processes, reducing the chances of being detected on the compromised server.
A new .NET backdoor retrieved from recent campaigns is dropped days after the initial intrusion to leverage WebSockets for C2 communications.
This component is responsible for setting up the communication configuration as well as for the initialization of cryptographic functions.
The use of WebSockets for communications is something unusual in the malware space, but PurpleFox shows that it can be very effective nonetheless.
Also Read: What Does A Data Protection Officer Do? 5 Main Things
The exchanged messages between the infected machine and the selected C2 server begin with negotiations for a session RSA encryption key, but even this first exchange is AES-encrypted using a default key.
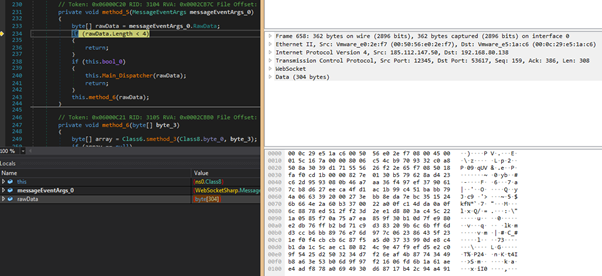
By sending “keepalive” messages, the TCP connection is maintained for as long as needed.
The list of WebSocket commands observed by TrendMicro is extensive, and although there are some discrepancies between different variants, the table below summarizes them all.
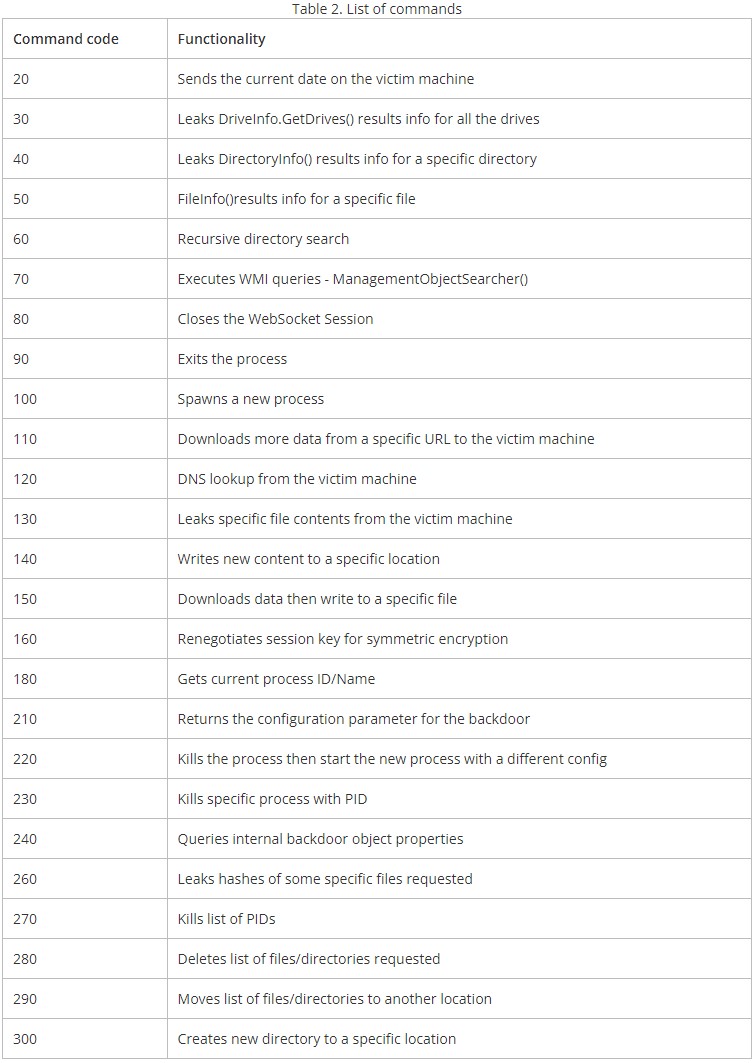
Currently, PurpleFox is still active and there’s a notable number of C&C servers controlling the WebSocket clients.
By doing some profiling of the targets, TrendMicro reports the most notable activity hotspots to be in the US, Turkey, UAE, Iraq, and Saudi Arabia.