KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Malware campaigns distributing Android trojans that steals online bank credentials have infected almost 300,000 devices through malicious apps pushed via Google’s Play Store.
The Android banking trojans delivered onto compromised devices attempt to steal users’ credentials when they log in to an online banking or cryptocurrency apps. Credential theft is commonly done using fake bank login form overlays displayed on top of the legitimate apps’ login screens.
The stolen credentials are then sent back to the attacker’s servers, where they are collected to be sold to other threat actors or used to steal cryptocurrency and money from victims’ accounts.
Also Read: 6 Simple Guides On PDPA Clause For Agreements Of Personal Data
In a new report by ThreatFabric, researchers explain how they discovered four different malware dropper campaigns distributing banking trojans on the Google Play Store.
While threat actors infiltrating the Google Play Store with Android banking trojans are nothing new, recent changes to Google’s policies and increased policing have forced threat actors to evolve their tactics to evade detection.
This evolution includes creating small realistic-looking apps that focus on common themes such as fitness, cryptocurrency, QR codes, and PDF scanning to trick users into installing the app. Then, to add further legitimacy to the apps, the threat actors create websites that fit the theme of the app to help pass reviews by Google.
Furthermore, ThreatFabric has seen these apps only being distributed to specific regions or at later dates to further evade detection by Google and antivirus vendors.
“This policing by Google has forced actors to find ways to significantly reduce the footprint of dropper apps. Besides improved malware code efforts, Google Play distribution campaigns are also more refined than previous campaigns,” ThreatFabric researchers explain in their new report.
Also Read: The Top 10 Primary GDPR Requirements PDF To Secure Business
“For example, by introducing carefully planned small malicious code updates over a longer period in Google Play, as well as sporting a dropper C2 backend to fully match the theme of the dropper app (for example a working Fitness website for a workout focused app).”
However, once these “dropper” apps are installed, they will silently communicate with the threat actor’s server to receive commands. When ready to distribute the banking trojan, the threat actor’s server will tell the installed app to perform a fake “update” that “drops” and launches the malware on the Android device.
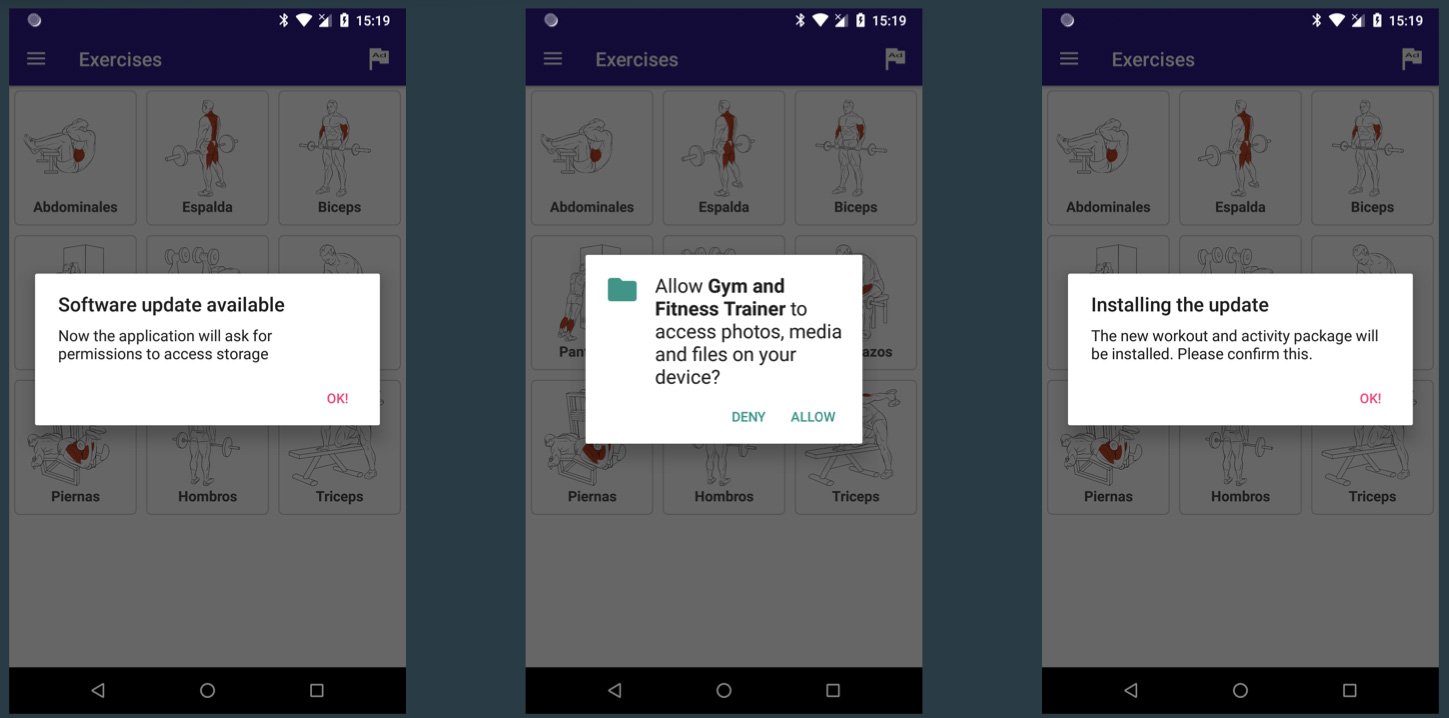
Since July 2021, ThreatFabric has these fake apps dropping four different banking trojans named ‘Alien’, ‘Hydra’, ‘Ermac’, and and ‘Anatsa’ through sixteen different apps.
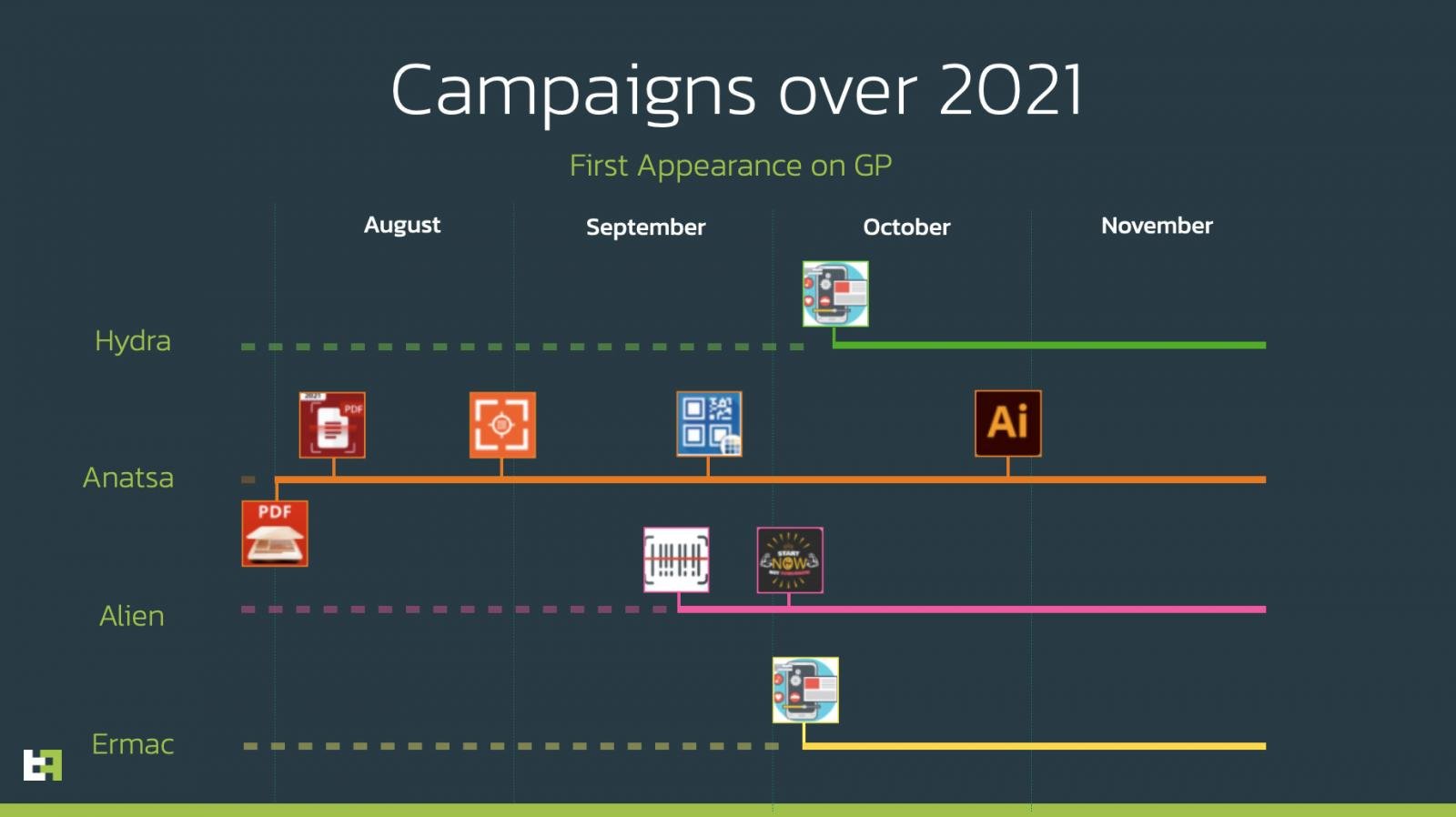
The “dropper” apps known to be used during these malware distribution campaigns are:
Other malicious apps seen installed by the above droppers and their associated banking trojans are:
During these four months of malicious activity, ThreatFrabric found that the droppers were installed 300,000 times, with some individual droppers installed over 50,000 times.
The number of banks, money transfer apps, cryptocurrency exchanges, cryptocurrency wallets, and mail services is impressive, with approximately 537 online sites and mobile apps targeted for credential theft.
The targeted organizations include Gmail, Chase, Citibank, HSBC, Coinbase, Kraken, Binance, KuCoin, CashApp, Zelle, TrustWallet, MetaMask, and more.
Google has since removed all of these malicious apps from the Play Store and you should also immediately remove them from your Android device if you have any of them installed.
If you have installed any of the above apps, you should immediately remove them from your Android device.
Furthermore, due to the evolving techniques used by Android malware developers, users must pay more attention to the permissions requested by apps and block the install if they seem overly broad.