KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





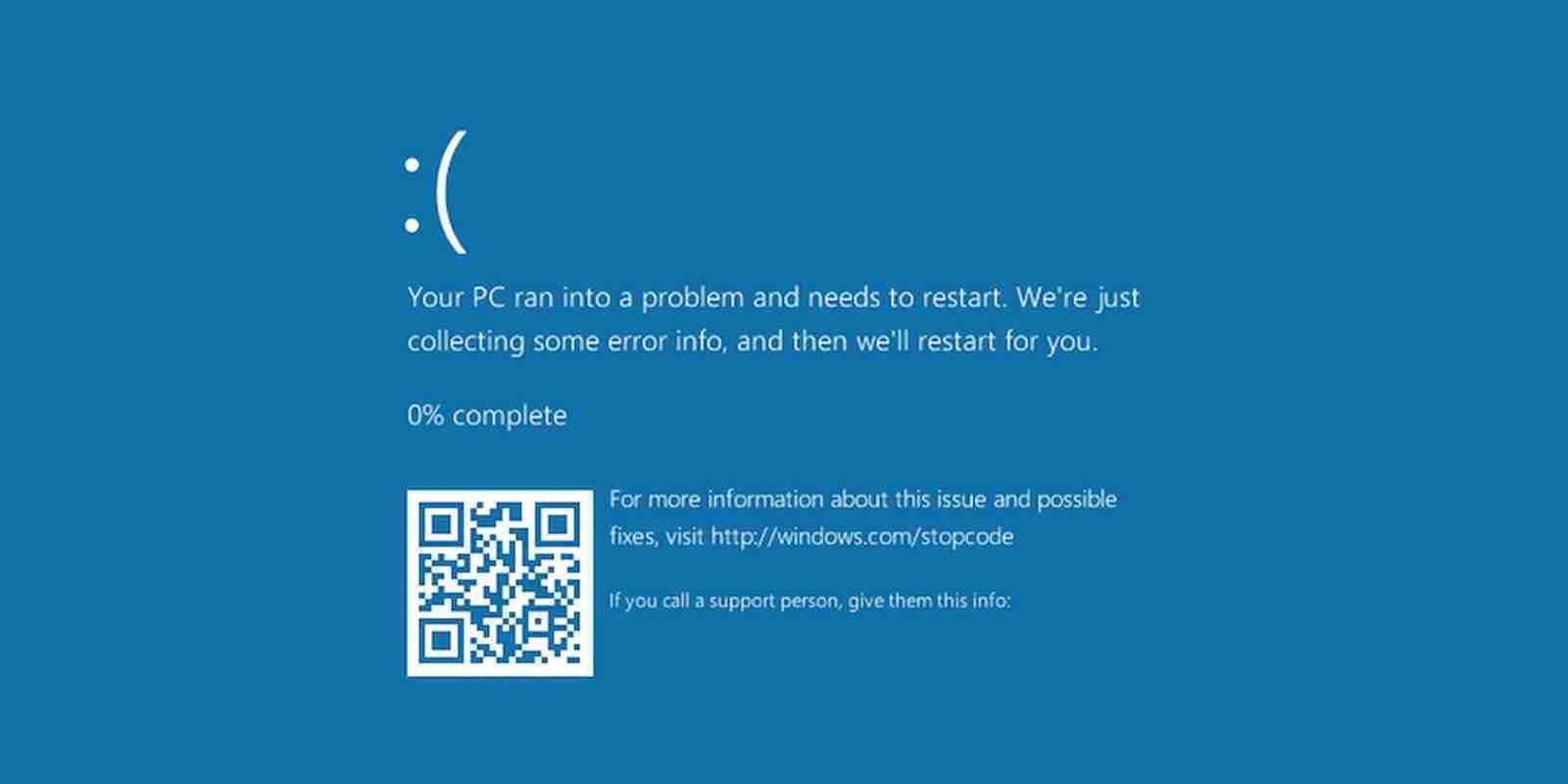
A bug in Windows 10 causes the operating system to crash with a Blue Screen of Death simply by opening a certain path in a browser’s address bar or using other Windows commands.
Last week, BleepingComputer learned of two bugs disclosed on Twitter by a Windows security researcher that can be abused by attackers in various attacks.
The first bug allows an unprivileged user or program to enter a single command that causes an NTFS volume to become marked as corrupted. While chkdsk resolved this issue in many tests, one of our tests showed that the command caused corruption on a hard drive that prevented Windows from starting.
Today, we look at the second bug that causes Windows 10 to perform a BSOD crash by merely attempting to open an unusual path.
Since October, Windows security researcher Jonas Lykkegaard has tweeted numerous times about a path that would immediately cause Windows 10 to crash and display a BSOD when entered into the Chrome address bar.
When developers want to interact with Windows devices directly, they can pass a Win32 device namespace path as an argument to various Windows programming functions. For example, this allows an application to interact directly with a physical disk without going through the file system.
Lykkegaard told BleepingComputer that he discovered the following Win32 device namespace path for the ‘console multiplexer driver’ that he believes is used for ‘kernel / usermode ipc.’ When opening the path in various ways, even from low-privileged users, it would cause Windows 10 to crash.
Also Read: How To Prevent WhatsApp Hack: 7 Best Practices
\.globalrootdevicecondrvkernelconnect
When connecting to this device, developers are expected to pass along the ‘attach’ extended attribute to communicate with the device properly.
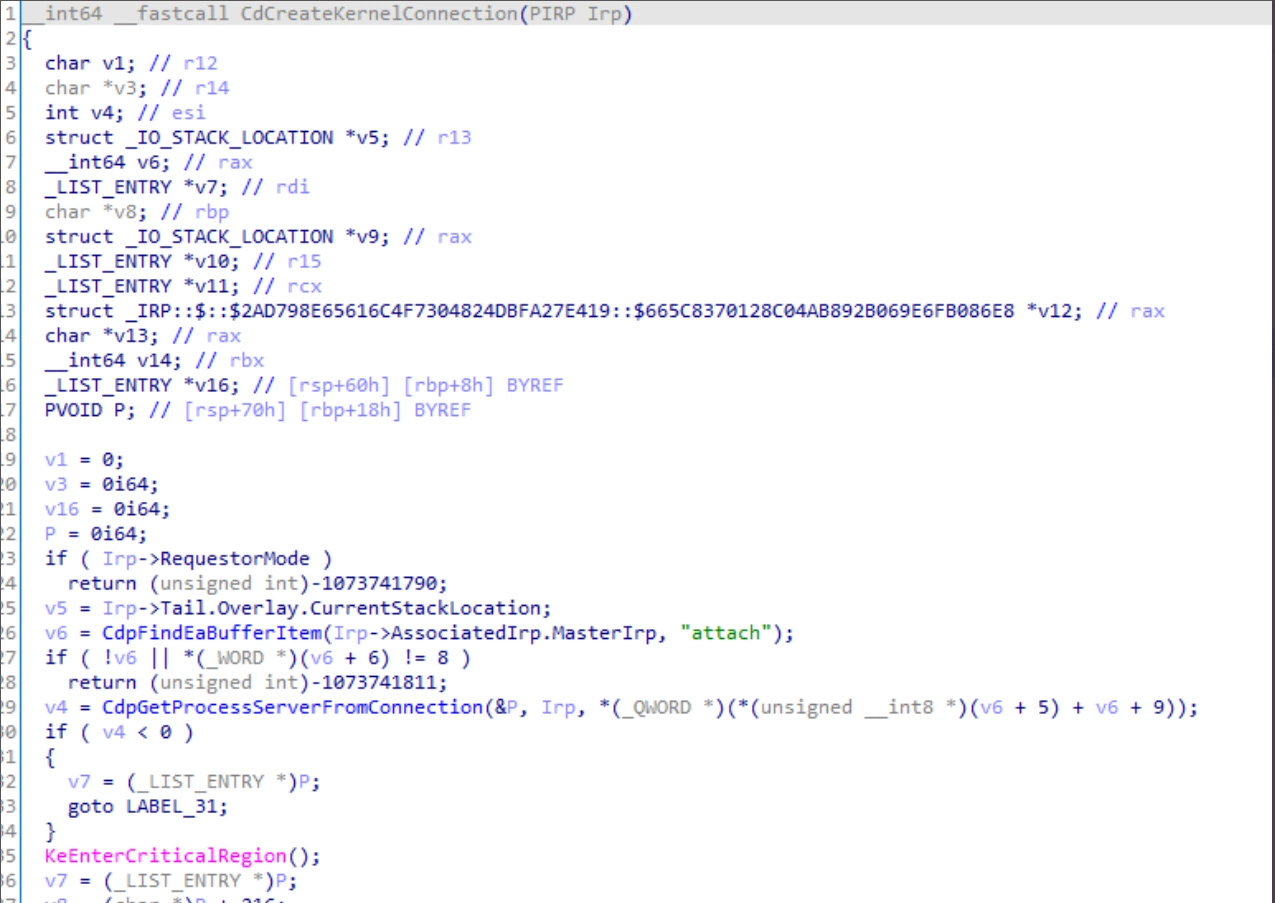
Lykkegaard discovered if you try to connect to the path without passing the attribute due to improper error checking, it will cause an exception that causes a Blue Screen of Death (BSOD) crash in Windows 10.
Even worse, low privileged Windows users can attempt to connect to the device using this path, making it easy for any program executed on a computer to crash Windows 10.
In our tests, we have confirmed this bug to be present on Windows 10 version 1709 and later. BleepingComputer was unable to test it in earlier versions.
BleepingComputer reached out to Microsoft last week to learn if they knew of the bug already and if they would fix the bug.
“Microsoft has a customer commitment to investigate reported security issues and we will provide updates for impacted devices as soon as possible,” a Microsoft spokesperson told BleepingComputer.
While it has not been determined if this bug could be exploited for remote code execution or elevation privilege, in its current form, it can be used as a denial of service attack on a computer.
Lykkegaard shared with BleepingComputer a Windows URL file (.url) with a setting pointing to \.globalrootdevicecondrvkernelconnect. When the file is downloaded, Windows 10 would try to render the URL file’s icon from the problematic path and automatically crash Windows 10.
BleepingComputer has since found numerous other ways to exploit this bug, including methods to cause BSODs automatically on Windows login.
In a real-life scenario, this bug could be abused by threat actors who have access to a network and want to cover their trail during an attack.
If they have admin credentials, they could remotely execute a command that accesses this path on all of the Windows 10 devices on a network to cause them to crash. The havoc caused on the network could delay investigations or prevent administrative controls from detecting an attack on a particular computer.
Also Read: Going Beyond DPO Meaning: Ever Heard of Outsourced DPO?
In 2017, a similar attack scenario was used by threat actors during a bank heist on the Far Eastern International Bank (FEIB) in Taiwan. In that attack, the threat actors deployed the Hermes ransomware on the network to delay investigations into the attack.