KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!



We are in 2020 and the US president is about to ban TikTok, a video-sharing social network mobile app, because “it poses a risk to US national security”. At the same time, Microsoft started discussions on a potential TikTok purchase in the United States. TikTok has received a lot of media coverage lately, but how much of it is factual? This is what I will try to answer in this series of articles. Each article will answer a very specific question. It is time to put the facts back on the table.
On August 2, 2020, I started to analyse TikTok and tweeted about it.
Few minutes after this tweet, one of my followers commented.
We discussed by private messages and he explained me the issue. He listened to the network requests made by TikTok and noticed that a request was made every 2 minutes. However, the content was encrypted and he was unable to decrypt it.
Sounds like a good starting point for our journey:
When debugging something, 90% of the work is being able to reproduce it. So, first I tried to reproduce the issue.
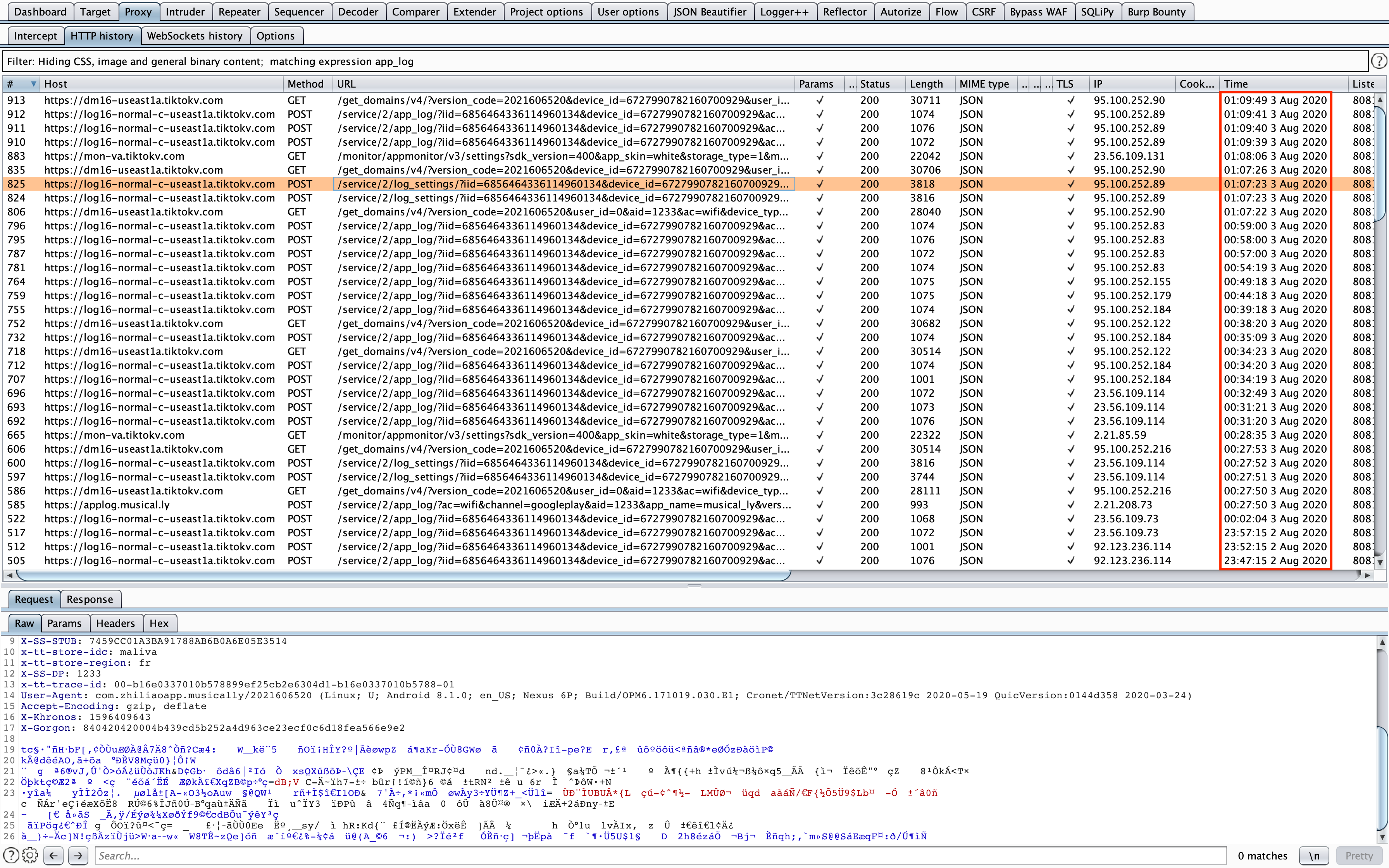
Bingo! Every 5 minutes, TikTok sent a network request with an encrypted content.
Let’s focus on the requests made to the endpoint /service/2/app_log/.
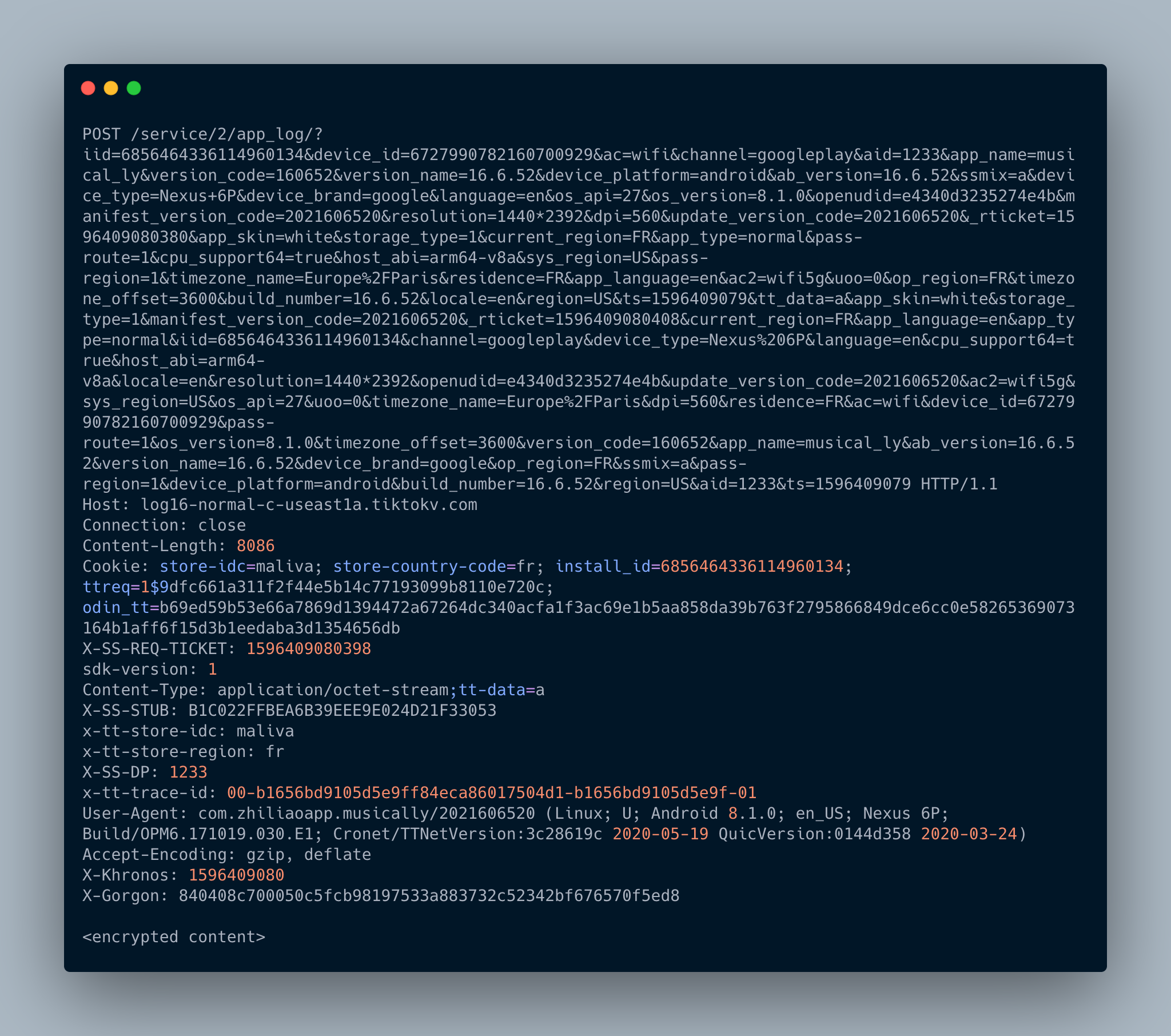
Parameters
Before studying its encrypted content, we can already see that this request contains a huge amount of parameters.
Most of the names speak for themselves. I can see 3 types of parameters:
While that might sound surprising to you, it really isn’t. Such practice is pretty standard and you can be assured that most apps you use have the same data-retrieval process.
Encrypted content
Time to look at the encrypted content! This is the fun part 😉. I decompiled the app and searched for “app_log”. I immediately found the method sendEncryptLog in the class com.ss.android.common.applog.NetUtil
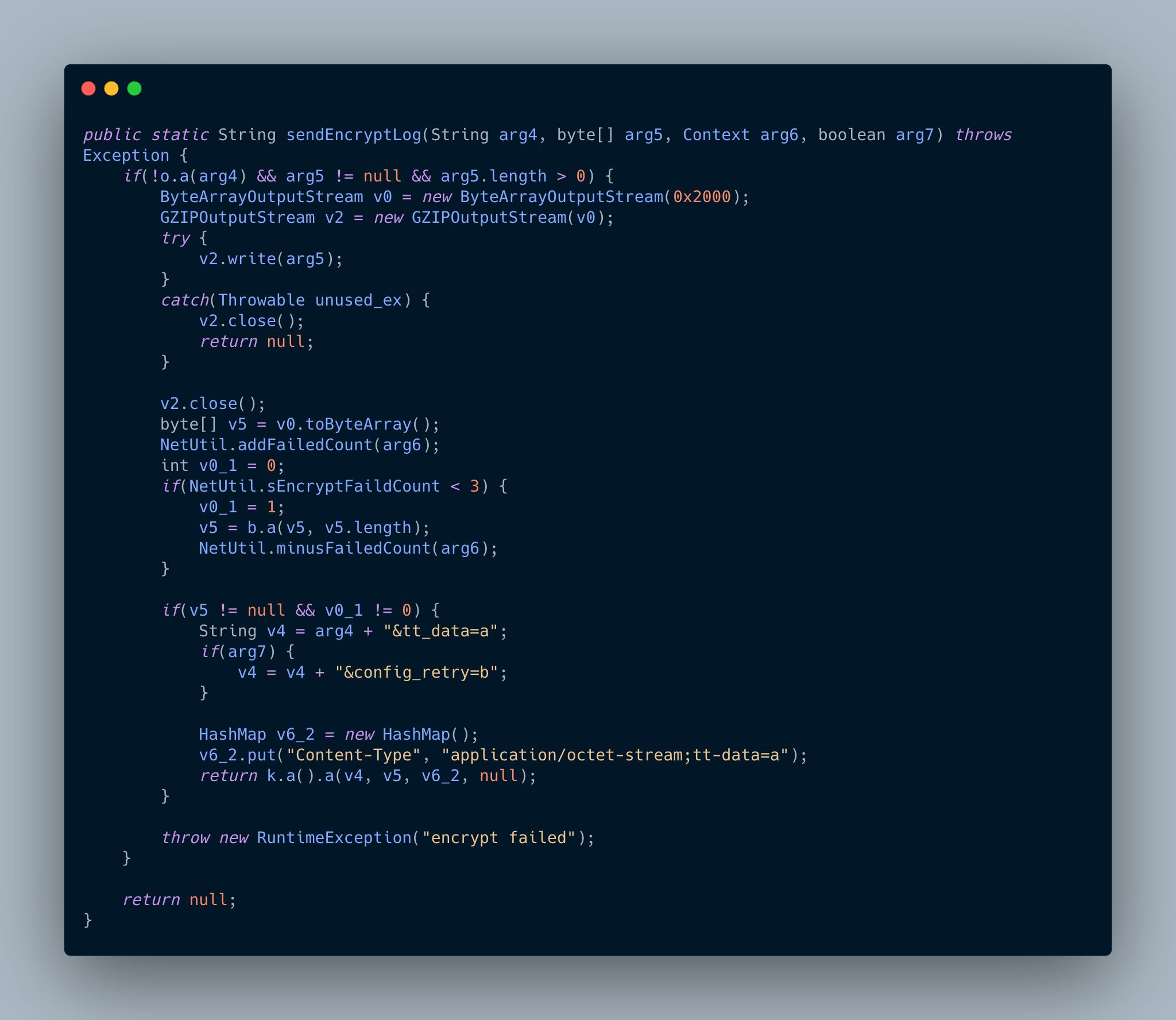
You don’t read code? That’s ok, don’t worry. Look at the method signature. It took 4 parameters. arg4 is the url, arg5 is the content of the request (non encrypted) and the rest we don’t care for the moment.
Now, I can use Frida to intercept the call of this method and see the content of the request before encryption.
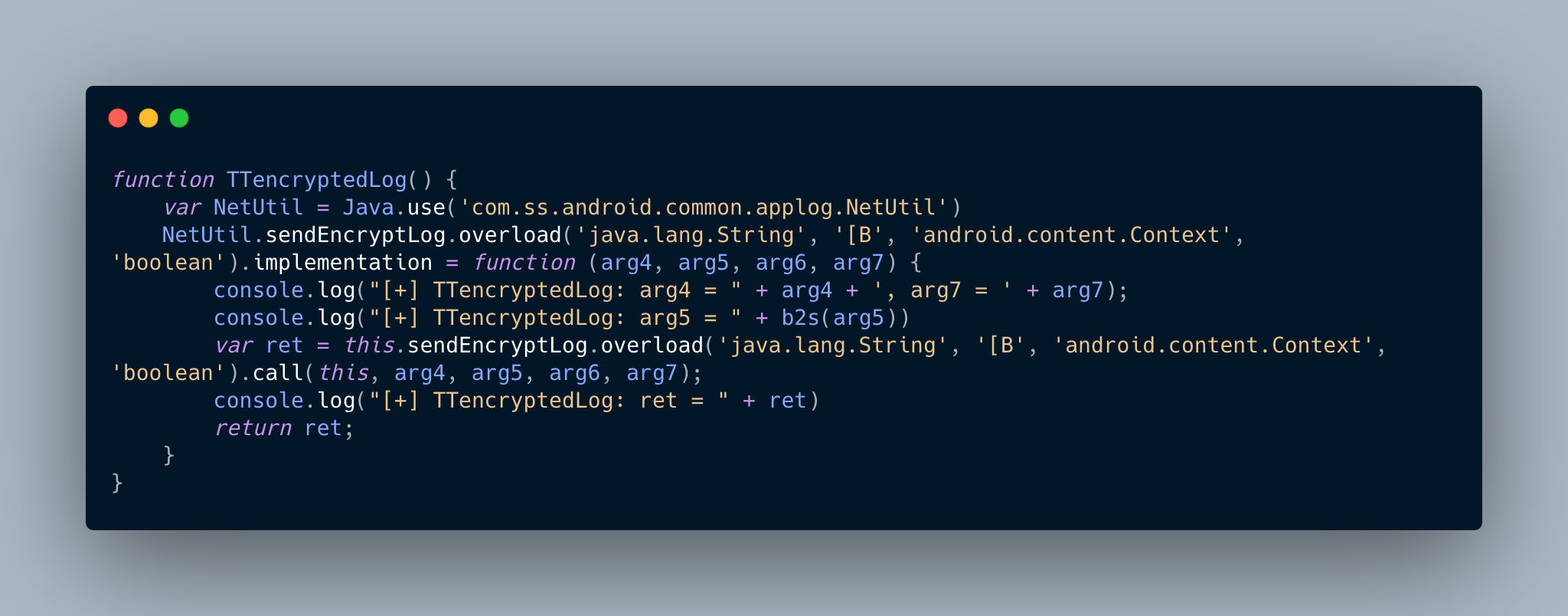
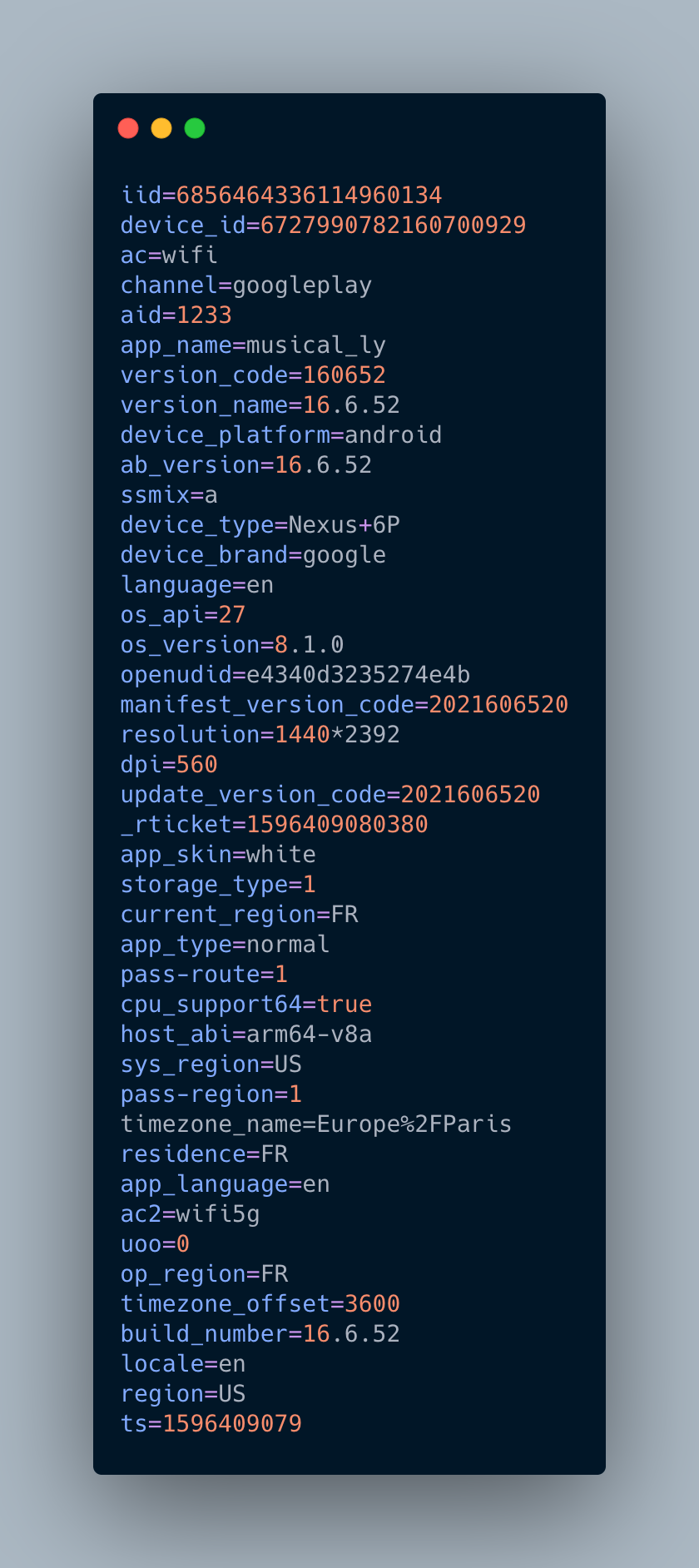
I used my small TTencryptedLog method and I got the following output
If we go through the content of the JSON file, we can see pretty standard data.
Also read: 12 brief explanation about the benefits of data protection for business success
Answer to this question is equal to answer to when the method sendEncryptLog is called. By pressing the key X with JEB, you can easily get all the cross references.
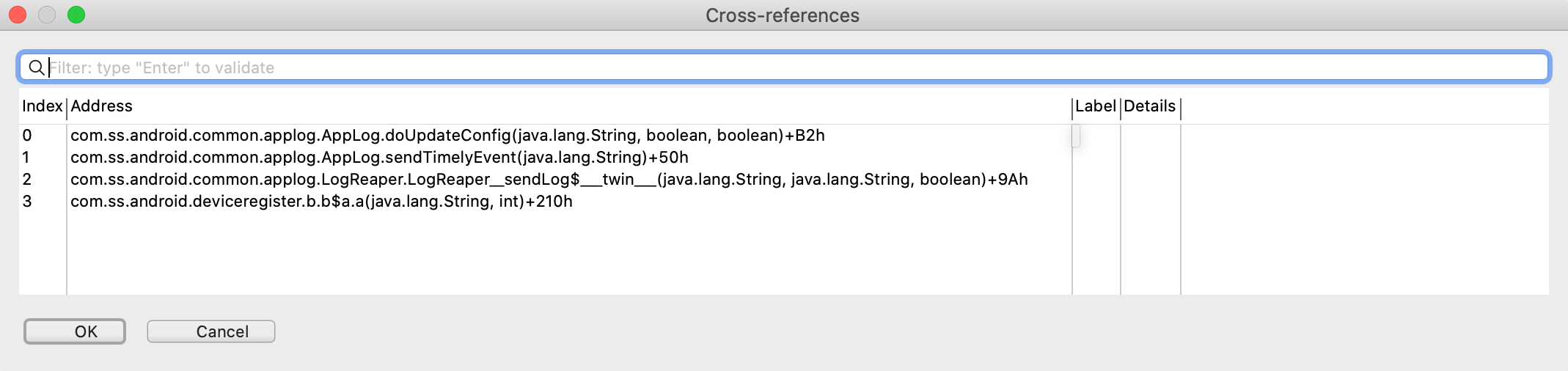
We can see 4 methods:
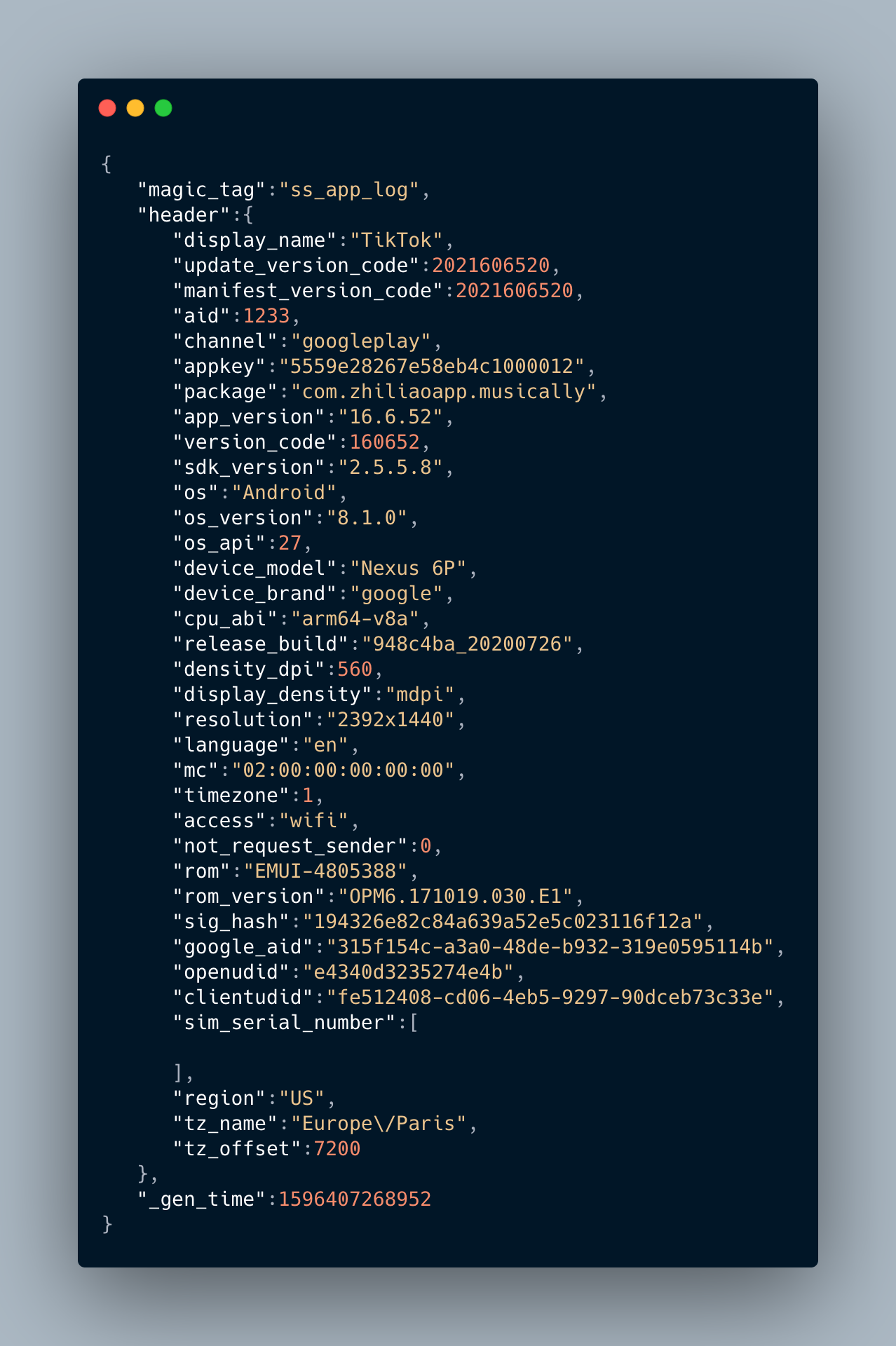
The sendEncryptLog method is used to send different type of JSON. So, I cleared the data of TikTok and I restarted everything from scratch. I managed to catch the following JSONs
Content of the request when the device is register
Content of the request when the TikTok modify the log settings
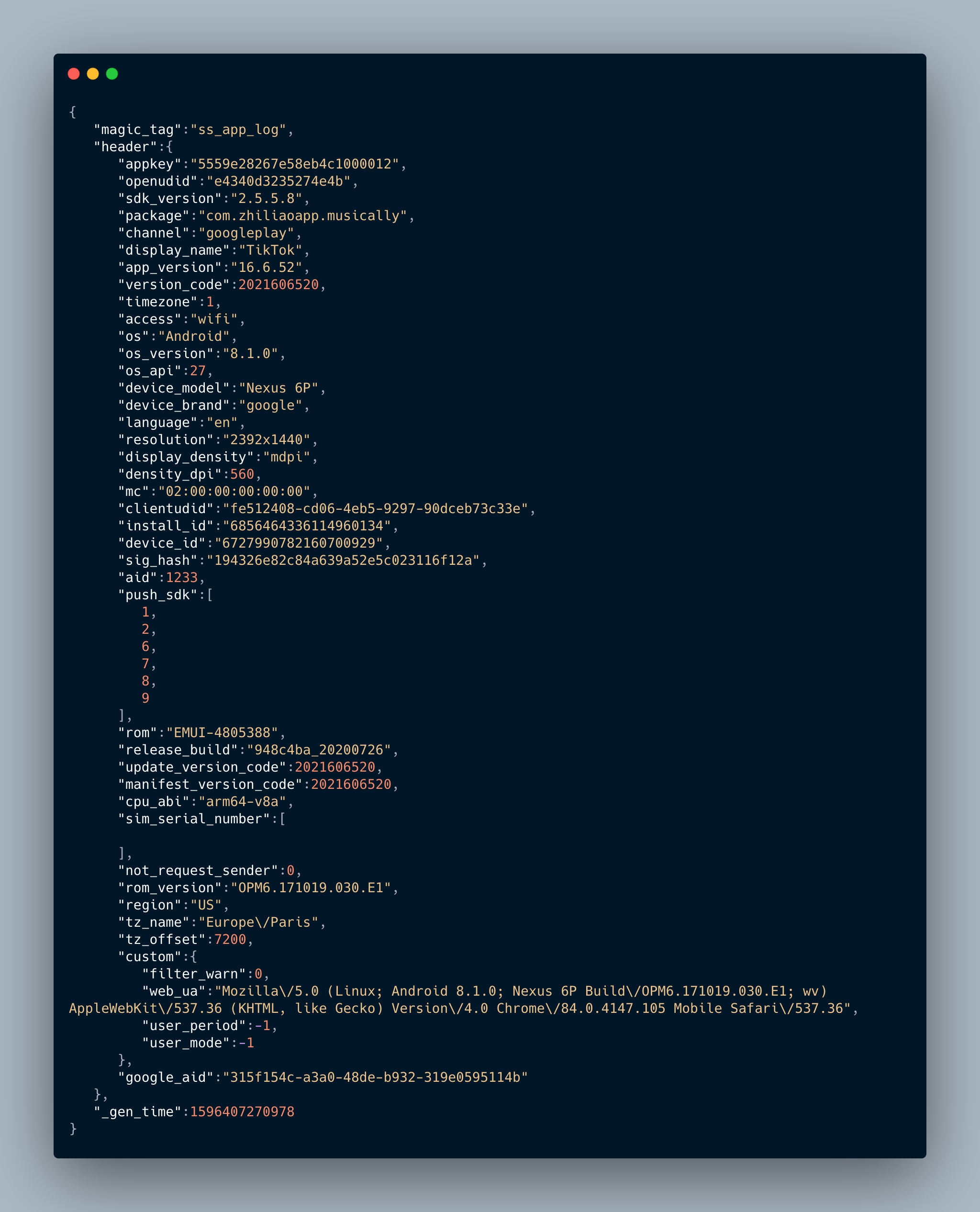
Again, the field names speak for themselves. I cannot see anything suspicious or specific to TikTok in these JSONs.
As you saw in the previous screenshots, the requests are sent to log16-normal-c-useast1a.tiktokv.com. Funny to see that I’m sitting in Europe and my logs are sent to a us-east enpoint… TikTok is an app used worldwide, they probably used several endpoint to upload the logs.
After digging in the code we can find the URLConfig class
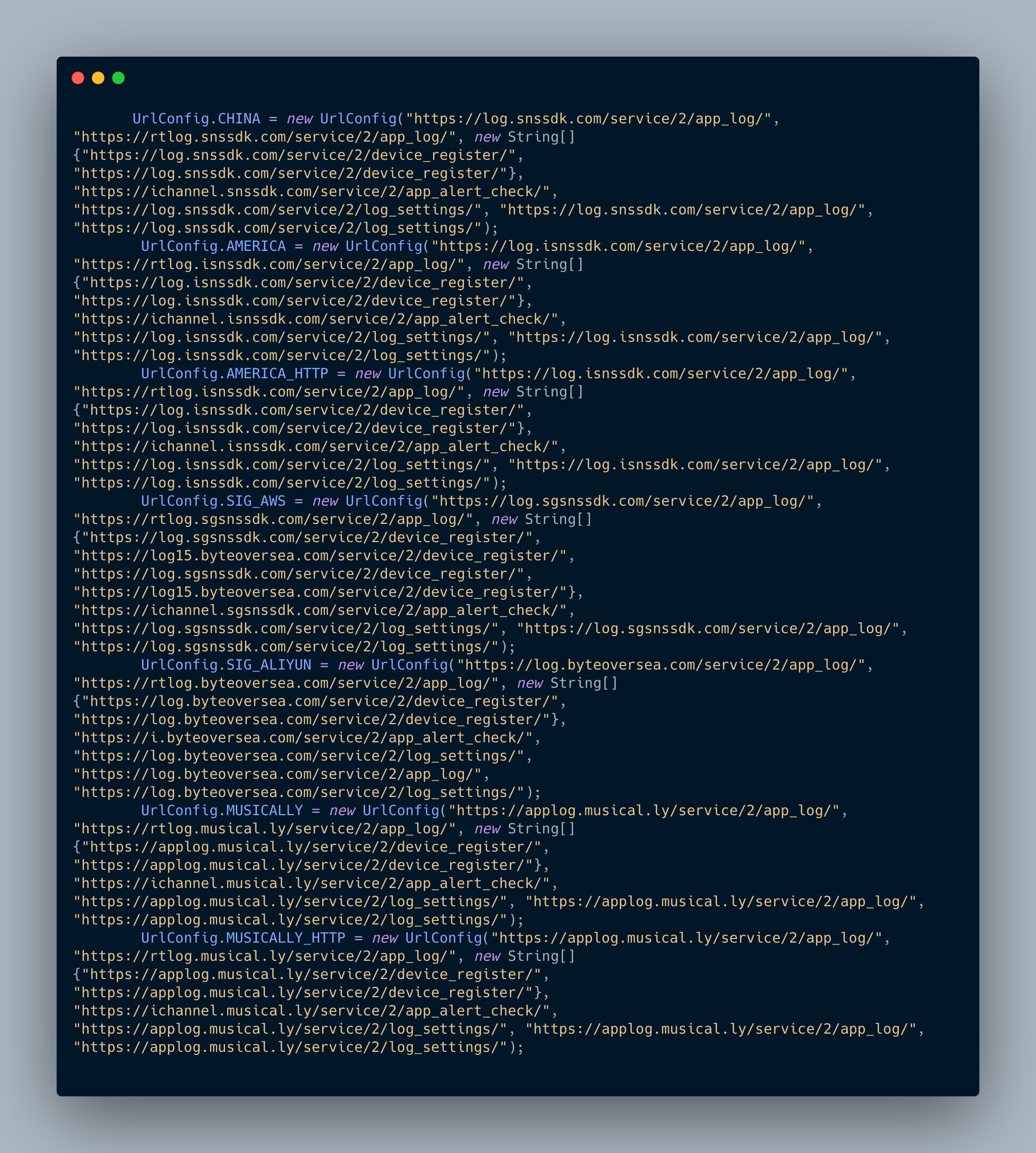
There are 7 url configurations: China, America, America HTTP, SIG AWS, SIG ALIYUN (Alicloud Singapore), Musically, Musically HTTP.
Again, it seems weird to not have an European url configuration but ok.
Do you remember the sendEncryptLog method?

The encryption is happening at this line: v5 = b.a(v5, v5.length);
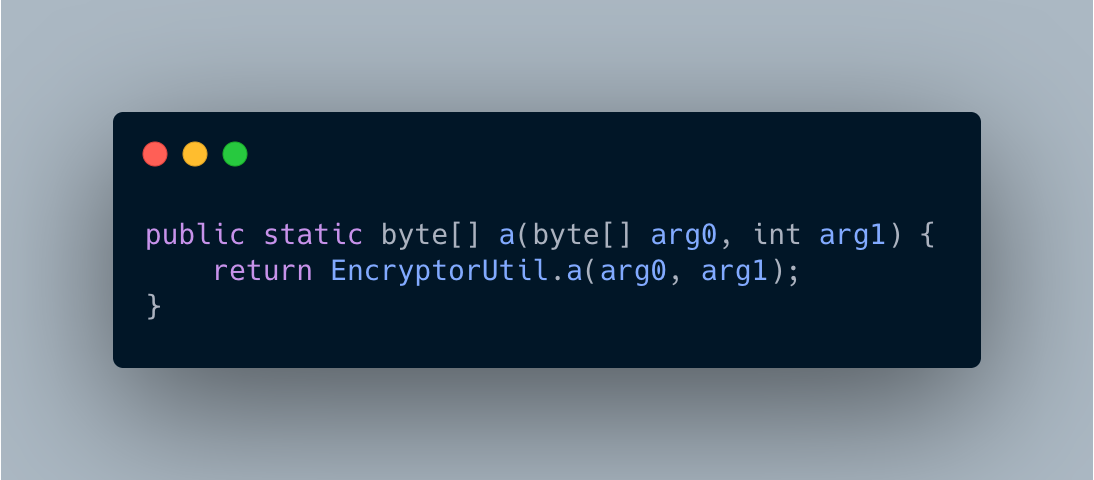
EncryptorUtil is where the fun is
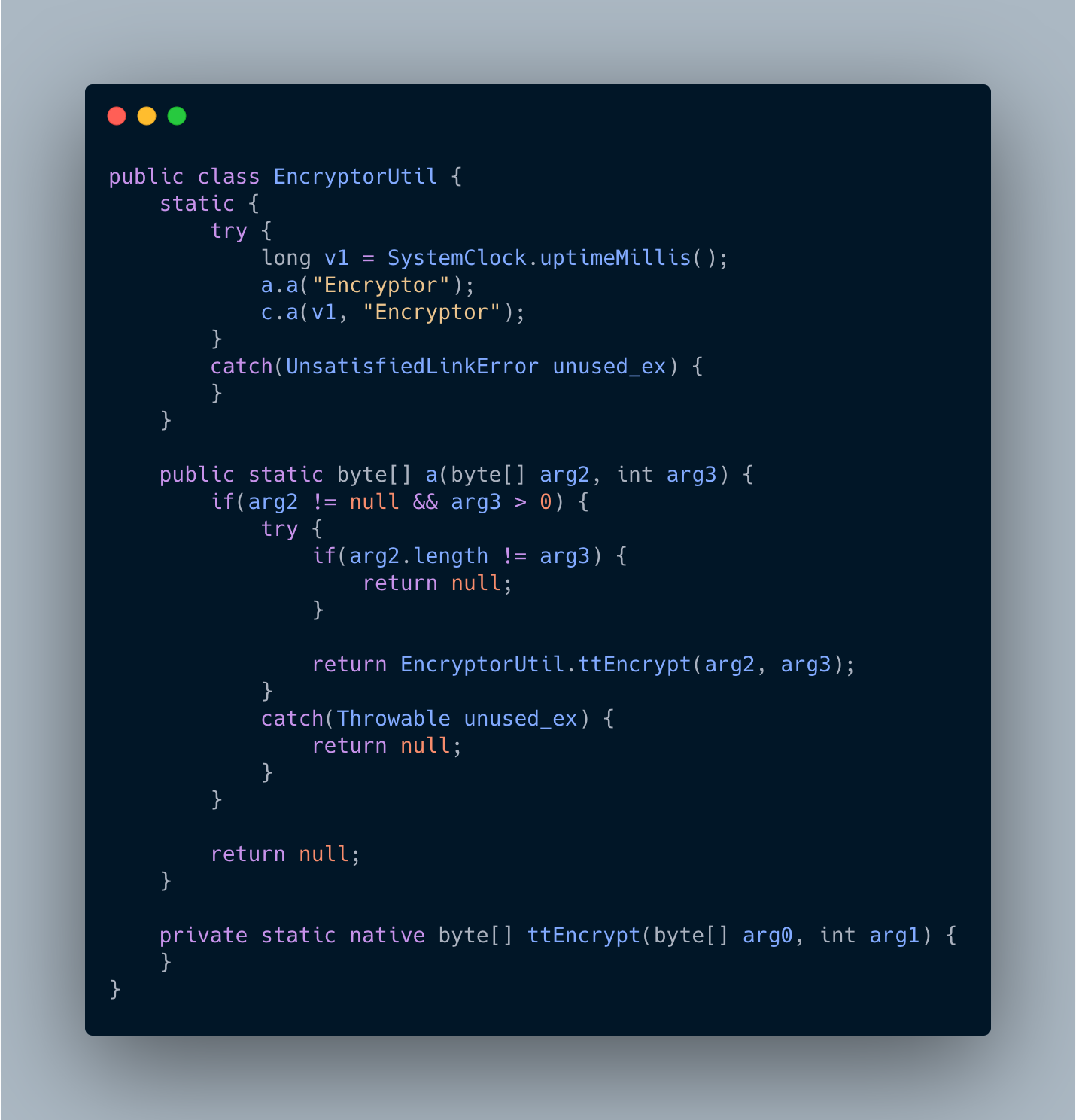
Bingo! The encryption is done in a native library. All the native library used by TikTok are located in the folder /data/data/com.zhiliaoapp.musically/app_librarian/<version> in your phone. I’ll stop there for now. As for how TikTok is actually encrypting the data, that deserves its own article. And, well, it’s 12pm and I’m quite hungry.
In this article, I tried to understand what data does TikTok regularly send back to its servers. I decrypted the content of the requests and analysed it. As far as we can see, in its current state, TikTok doesn’t have a suspicious behavior and is not exfiltrating unusual data. Getting data about the user device is quite common in the mobile world and we would obtain similar results with Facebook, Snapchat, Instagram and others.
I hope you enjoy this article. Others will follow. Don’t forget to follow me on Twitter and if you have questions don’t hesitate to sent me a message on Twitter or by email at [email protected]
Also read: Privacy policy template important tips for your business