KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft announced today the extension of Data Loss Prevention (DLP) to Microsoft 365 customers’ endpoints, making it easier for organizations to prevent data leaks, inappropriate or unintentional data sharing or transfer, and other similar risks.
Microsoft 365 Endpoint Data Loss Prevention (DLP) extends DLP’s activity monitoring and protection capabilities to sensitive data and items on Windows 10 devices.
“Once devices are onboarded into device management, the information about what users are doing with sensitive items is made visible in activity explorer and you can enforce protective actions on those items via DLP policies,” Microsoft explains.
Microsoft 365 services like Microsoft Teams, SharePoint, Exchange, apps such as Word, PowerPoint, Excel, and Outlook, as well as third-party cloud apps with Microsoft Cloud App Security already come with built-in data loss prevention capabilities provided through Microsoft Information Protection (MIP).
Also read: 7 Client Data Protection Tips to Keep Customers Safe
The public preview of Microsoft Endpoint Data Loss Prevention (DLP) now extends MIP protection to devices and allows customers to deploy the same information protection strategy across all environments.
For instance, organizations can use Endpoint DLP to block their employees from printing sensitive documents or from copying sensitive data to USB drives.
“Today we are excited to announce that we are now extending data loss prevention to the endpoint with the public preview of the new Microsoft Endpoint Data Loss Prevention (DLP),” Microsoft 365 Senior Director Alym Rayani said today.
“Endpoint DLP builds on the labeling and classification in Microsoft Information Protection and extends the existing DLP capabilities in Microsoft 365, helping you to meet compliance requirements and protect sensitive information on endpoints.”
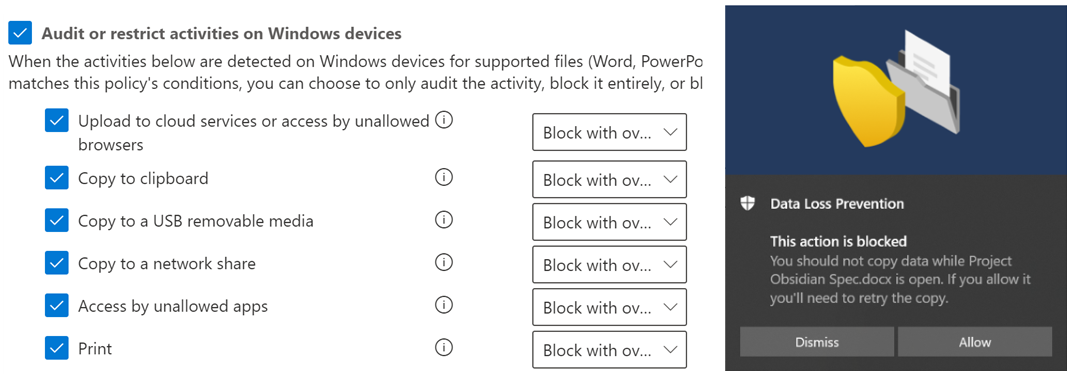
Right now, Endpoint DLP allows organizations to enforce policies for a wide range of activities unique to each endpoint including:
Data loss prevention policies can be managed from the compliance center across an entire Microsoft 365 environment, for an organization’s software, services, and Windows devices.
“All that is required is for the endpoint to be onboarded in your environment using your established device management onboarding process,” Microsoft said.
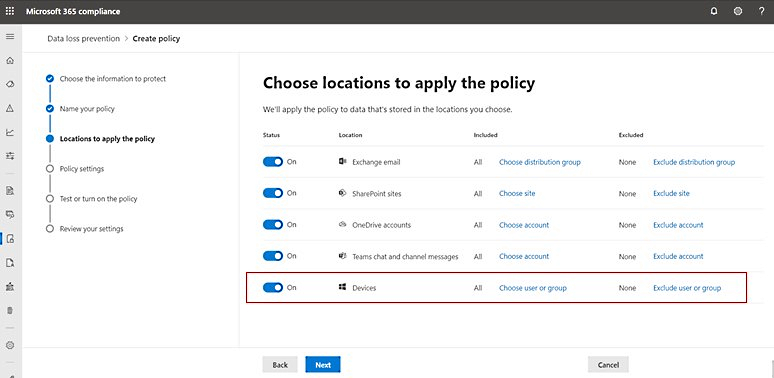
According to Microsoft, Endpoint DLP has already begun rolling out to customers’ tenants today in Microsoft 365 E5/A5 (EDU), Microsoft 365 E5/A5 Compliance, and Microsoft 365 E5/A5 Information Protection and Governance.
Microsoft 365 customers can learn more about Endpoint DLP on the feature’s dedicated documentation page. You can also go here for more info on how to get started with Endpoint DLP and here to get more details on how to use it.
You can sign up for a Microsoft 365 E5 trial to take Endpoint DLP for a spin today or navigate to the Microsoft 365 compliance center to get started if you already have a relevant Microsoft 365 subscription or add-on.
To deploy Endpoint DLP on a Windows 10 device, that endpoint has to meet these requirements:
Microsoft is also rolling out Double Key Encryption in public preview today, a Microsoft 365 E5 feature that enables customers to protect highly sensitive data while also keeping full control of their encryption keys.
“Double Key Encryption for Microsoft 365 uses two keys to protect your data, with one key in your control and the second in Microsoft’s control,” the company explained.
“To view the data, one must have access to both keys. Since Microsoft can access only one key, your data and key are unavailable to Microsoft, helping to ensure the privacy and security of your data.”
Also read: 7 Phases Of Data Life Cycle Every Business Must Be Informed