KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Following a year-long investigation led by Interpol, three members of a prolific cybergang with a confirmed victim count of about 50,000 organizations have been arrested recently in Lagos, Nigeria.
The suspects are likely part of a larger organized group involved in business email compromise (BEC) attacks since at least 2017.
Cybersecurity company Group-IB has been tracking the gang since 2019 and assisted the Interpol-led investigation, which received the code name Operation Falcon.
The Nigerian Police Force apprehended the three suspects. Its cybercrime unit analyzing electronic devices belonging to the three suspects determined their involvement in cybercriminal activity and identified data stolen from at least 50,000 victims.
The tally may be much higher, though as Group-IB established that the TMT gang targeted around 500,000 organizations from the private and government sector in more than 150 countries.
In an announcement today, the Interpol says that the three suspects “are alleged to have developed phishing links, domains, and mass mailing campaigns in which they impersonated representatives of organizations.”
This enabled them to distribute to victims at least 26 different malicious programs. On the list is malware designed to steal information (AgentTesla, Azorult, Loki, Pony, ) and remote access tools like NanoCore, Remcos, and NetWire.
Also Read: Contract for Service Template: 5 Important Sections
These tools are commonly used by Nigerian threat actors specialized in BEC scams. They are either freely available or widely accessible on cybercriminal forums for low prices.
The FBI’s Internet Crime Complaint Center received close to 24,000 complaints about this attacks last year, causing estimated losses of $1.7 billion.
BEC scammers use malware to collect sensitive information like authentication data from browsers, email, and FTP clients.
The details are then used to carry out the fraud, which typically consists in tricking companies into making a payment to bank accounts controlled by the attackers.
In some cases, the threat actors change the payment details so the victim company transfers the money to their account. Other times, BEC scammers turn to social engineering and just trick the organization into making a payment for a bogus order.
According to Group-IB, TMT would impersonate legitimate companies in phishing emails purporting to be purchasing orders, product inquiries, and inquiries, and messages related to Covid-19.
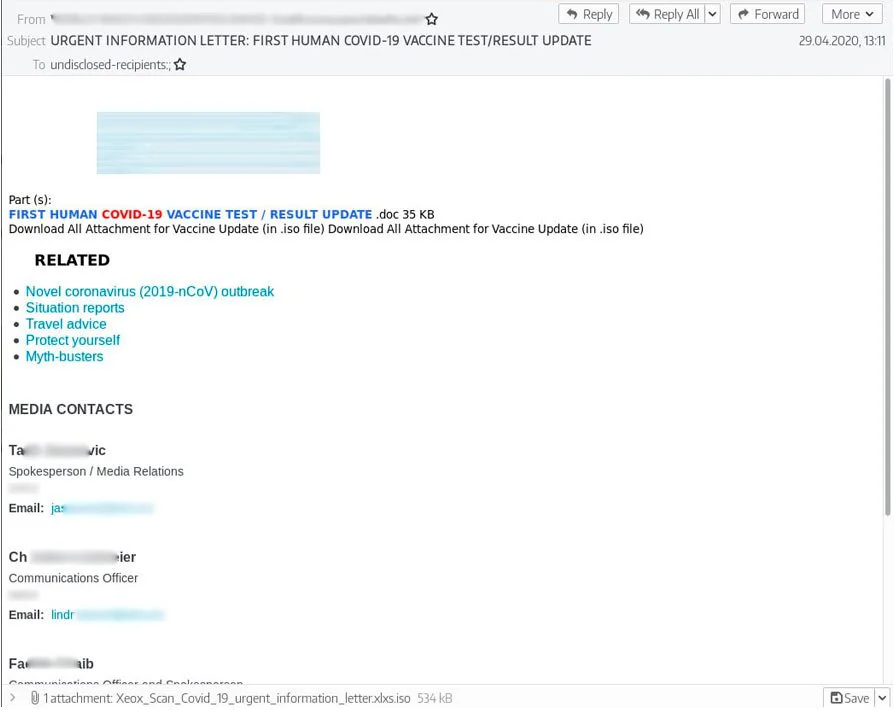
The scammers created their messages in the language of the victim, Group-IB says, some samples being written in English, Russian, and Spanish.
They automated the email sending process using Gammadyne and Turbo mass mailers advertised as email marketing tools. They also monitored if the recipients opened the message using MailChimp automation platform.
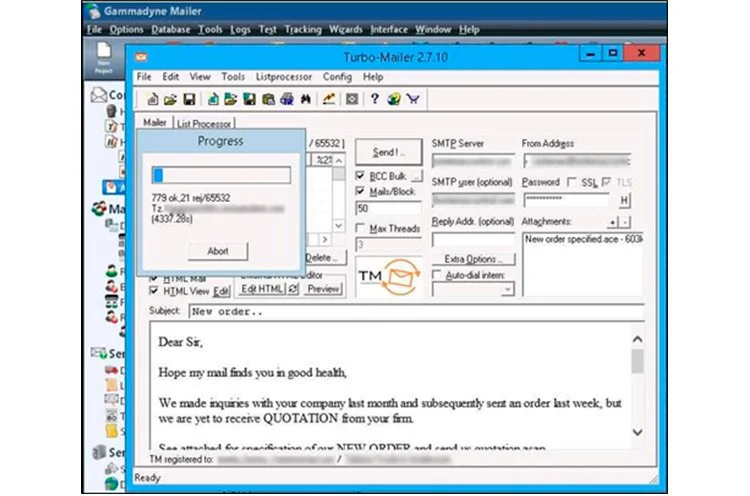
According to logs analyzed by the researchers, TMT also used previously compromised inboxes to send out a new set of phishing emails.
Also Read: Letter of Consent MOM: Getting the Details Right
TMT is a well-organized gang with multiple sub-groups that perform various tasks. Group-IB says that they tracked down other suspects and shared the information with Interpol’s Cybercrime Directorate headed by Craig Jones.
Jones says that TMT operators had an effective criminal business model that covered everything from the infiltration stage to withdrawing the stolen money.