KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





Experienced fraudsters made off with $15 million from a U.S. company after carefully running an email compromise that took about two months to complete.
The cybercriminal executed their plan with surgical precision after gaining access to email conversations about a commercial transaction. They inserted themselves in the exchange to divert the payment and were able to keep the theft hidden long enough to get the money.
Although researchers investigated events at a single victim, they found clues indicating that dozens of businesses in construction, retail, finance, and legal sectors are on their list of targets.
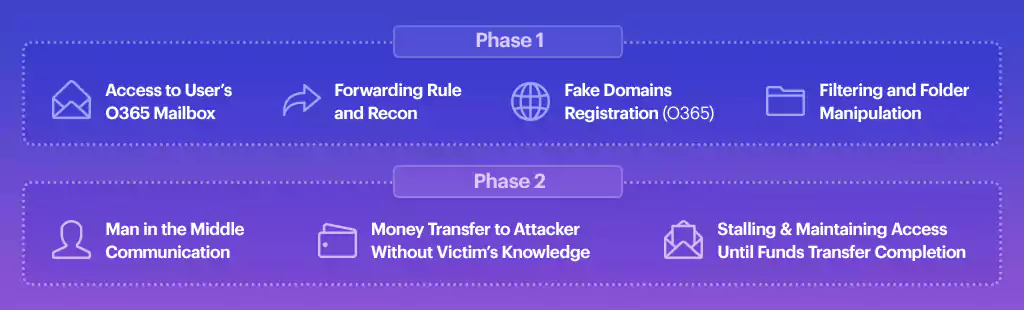
After the actor decided on a target, they spent about two weeks trying to access email accounts. Once in, they devoted another week collecting information from the victim’s mailbox and identifying an opportunity.
Ariel Parnes, Chief Engineering Officer at Mitiga, the company investigating the incident told BleepingComputer that their researchers did not find malware on the victim systems, pointing to email login compromise.
Email access was not enough, though, Parnes told us. Since the actor could lose that at any moment, they created email forwarding rules to get the messages from the monitored email inbox.
By also using the Microsoft Office 365 email service for domains impersonating the two parties involved in the transaction, the cybercriminals would be able to continue the attack.
Mitiga says that the threat actor delivered emails using an Office 365 account to reduce suspicion and evade detection. They also registered domains via a GoDaddy registrar (Wild West Domains) that were similar to those used by legitimate businesses (many of them in the U.S.).
These details allowed Mitiga to establish a pattern and discover more than 150 of these rogue domains, revealing the larger activity of the cybercriminal group.
For four weeks, the attacker carefully progressed with their plan using information gathered from the compromised inboxes of senior executives. They took over the conversation using the fake domains at the opportune moment to provide altered details for the money transfer.
Also Read: Privacy Policy Template Important Tips For Your Business
It was not the end of it, though. Banks can lock a transaction when money goes to the wrong account, and the error is flagged in time. The threat actor was well aware of this detail and had prepared for this phase.
To conceal the theft until they moved the money to foreign banks and make it lost forever, the attacker used inbox filtering rules to move messages from specific email addresses to a hidden folder.
It was a move that kept the legitimate inbox owner unaware of communication about the money transfer. It lasted for about two weeks, Mitiga says, sufficient for the actor to make the $15 million disappear.
Mitiga’s role in this incident was to investigate what happened after the victim company realized that they lost the money to cybercriminals. The researchers are helping the FBI’s and the U.S. Secret Service’s efforts to track the attacker.
Organizations can strengthen their defenses against this type of attack by following a simple set of recommendations which include, among others, enabling two-factor authentication in Office 365 and preventing email forwarding to external addresses.
Additionally, MItiga recommends the following:
Also Read: Basic Info On How Long To Keep Accounting Records In Singapore?