KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





Microsoft Office 365 users are targeted by a new phishing campaign using fake Zoom notifications to warn those who work in corporate environments that their Zoom accounts have been suspended, with the end goal of stealing Office 365 logins.
Zoom is a cloud-based communication platform providing users with audio and videoconferencing services, online meetings, as well as chat and team collaboration via mobile, desktop, and telephone systems. Since the start of 2020 Zoom has seen a radical increase of new monthly active users after millions of employees have switched to remote working.
So far the phishing campaign impersonating automated Zoom account suspension alerts has landed in over 50,000 mailboxes based on stats provided by researchers as email security company Abnormal Security who spotted these ongoing attacks.
Those targeted by this campaign are a lot more willing to trust such emails during this time since the number of remote workers taking part in daily online meetings through video conferencing platforms such as Zoom has drastically increased due to stay-at-home orders or lockdowns caused by the pandemic.
The phishing emails spotted by Abnormal Security’s researchers spoof an official Zoom email address and are designed to impersonate a legitimate automated Zoom notification.
Using a spoofed email address and an email body almost free of any grammar errors or typos (besides an obvious ‘zoom’ instead of ‘Zoom account’) makes these phishing messages even more convincing and potentially a lot more effective.
The use of a cheerful “Happy Zooming!” at the end of the email could raise some alarms though, as it doesn’t quite fit with the rest of the message’s tone.
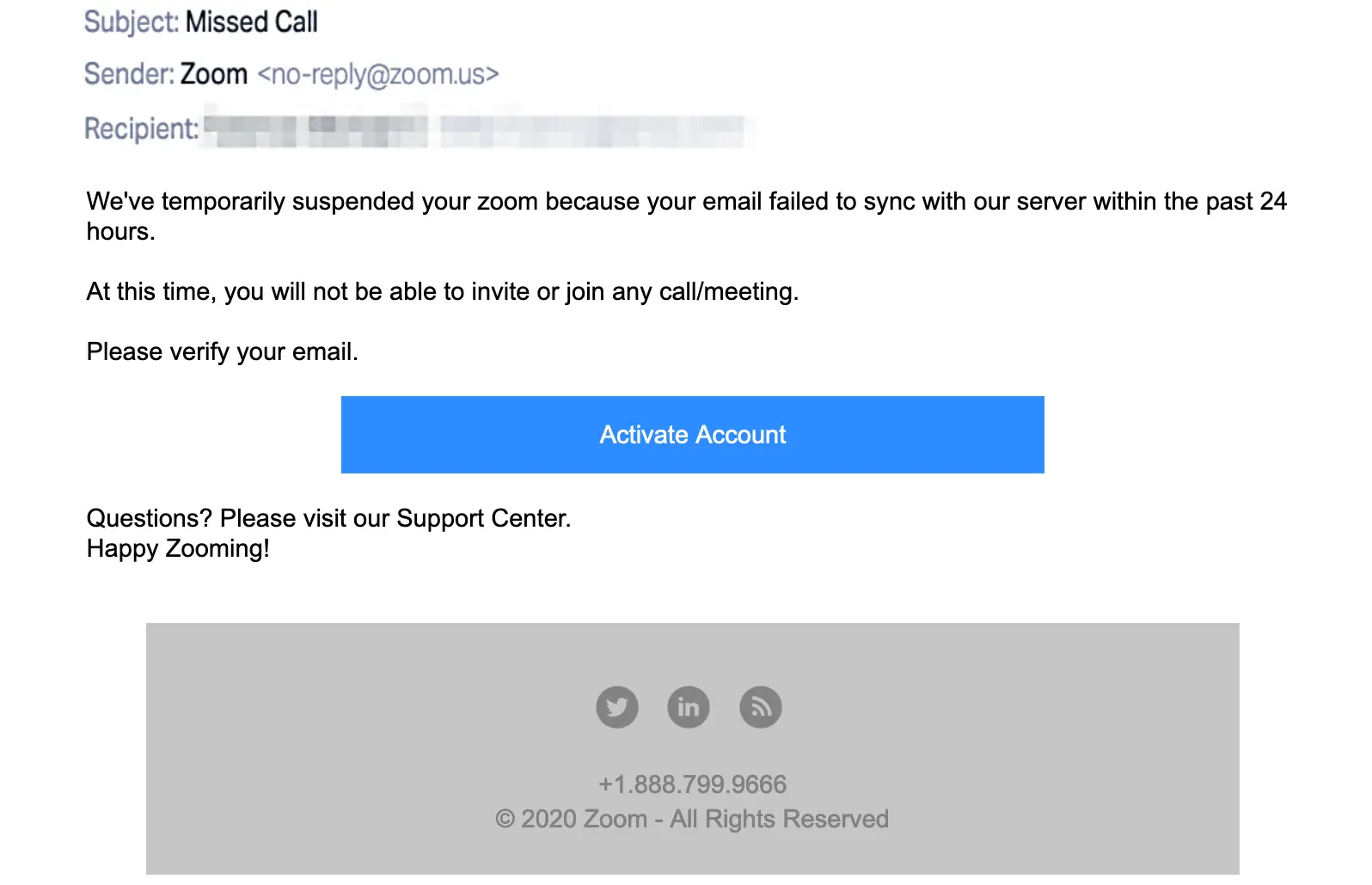
The targets are warned that their Zoom accounts were temporarily suspended and that they will not be able to join any calls and meetings until they re-activate their accounts by clicking on an activation button embedded within the message.
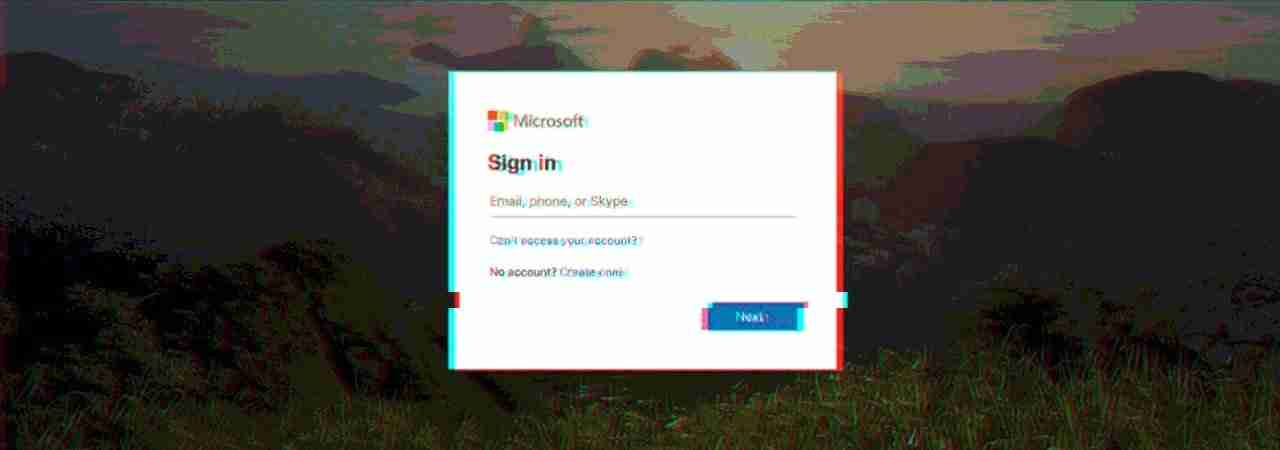
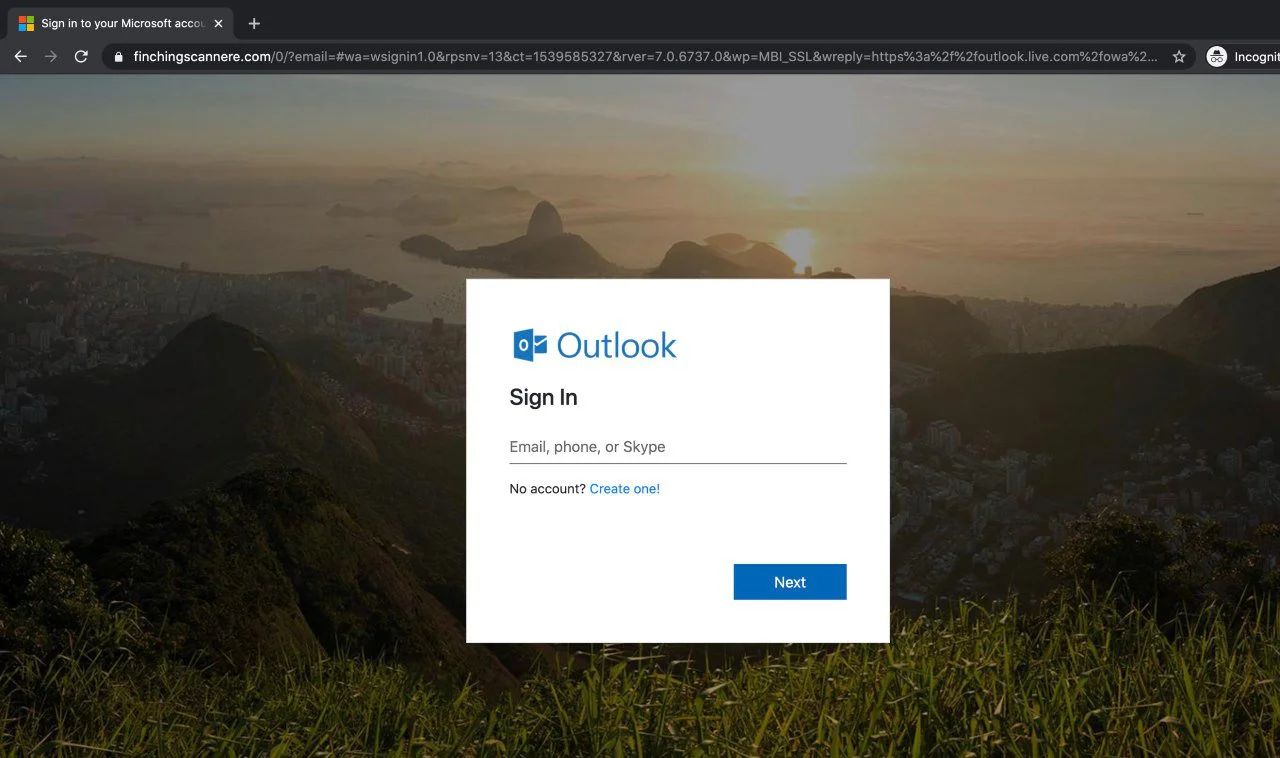
Once they click the “Activate Account” button, the recipients are redirected to a fake Microsoft login page through an intermediary hijacked website.
On the phishing landing page, the victims are asked to input their Outlook credentials in a form designed to exfiltrate their accounts details to attacker-controlled servers.
“The importance of Zoom as a communications method is essential in a world under the shadow of the COVID-19 pandemic,” Abnormal Security explained. “Thus, the user may rush to correct their account, click on the malicious link, and inadvertently enter credentials on this bad website.”
If they fall for the attackers’ tricks, the victims’ Microsoft credentials will be used to take full control of their accounts and all their information will be ripe for the picking, later to be used as apart of identity theft and fraud schemes such as Business Email Compromise (BEC) attacks.
Also read: Cost of GDPR Compliance for Singapore Companies
The US Federal Bureau of Investigation (FBI) warned of BEC scammers abusing popular cloud email services such as Microsoft Office 365 and Google G Suite through Private Industry Notifications issued in March and in April.
“Between January 2014 and October 2019, the Internet Crime Complaint Center (IC3) received complaints totaling over $2.1 billion in actual losses from BEC scams targeting Microsoft Office 365 and Google G Suite,” the FBI notified at the time.
The FBI’s Internet Crime Complaint Center (IC3) also issued a PSA in September 2019 advising that BEC scams are increasingly dangerous, with victim complaints with a total exposed dollar loss of more than $26 billion between 2016 and 2019, as well as a 100% surge in the identified global exposed losses from May 2018 to July 2019.
Office 365 users are continuously targeted by phishing campaigns with the end goal of harvesting their credentials.
Microsoft customers were lured with fake Microsoft Teams alerts, fake VPN configs, and Small Business Grants Fund (SGF) relief payment baits to hand over their Office 365 login information, with tens of thousands of these phishing messages landing in the targets’ inboxes.
Yesterday, Microsoft also warned of phishers’ recent shift to new types of phishing tactics such as consent phishing, besides conventional email phishing and credential theft attacks.
“While application use has accelerated and enabled employees to be productive remotely, attackers are looking at leveraging application-based attacks to gain unwarranted access to valuable data in cloud services,” Microsoft Partner Group PM Manager Agnieszka Girling said.
The company also took legal action to dismantle part of the attack infrastructure used to host malicious 365 OAuth apps used in consent phishing to hijack victims’ Office 365 accounts.
Also read: 6 Simple Tips on Cyber Safety at Home