KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





A new email tool advertised on a cybercriminal forum provides a stealthier method for carrying out fraud or malware attacks by allowing messages to be injected directly into the victim’s inbox.
By slipping content in the normal email flow, the utility can help bypass protections that verify messages traveling to their destination mail server.
Called “Email Appender,” the tool can enable more sophisticated phishing and business email compromise (BEC) attacks as well as help the less technical actors in the ransomware business.
Researchers at Gemini Advisory saw this utility advertised in October, from an actor that also provides a mass email service called “GetMailer Pro.”
Also Read: What is Pentest Report? Here’s A Walk-through

Translation:
I offer you a tool for targeting mailings and extracting installations from IMAP databases
The software can put any email on your account with your content bypassing spam filters
The work of the software is limited only by your imagination and the availability of databases
The software is written in Node JS + GUI from bas
For the software to work, you will need valid IMAP databases mail: pass
Functionality
full change of sender (whether paypal, blockchain or any Bank)
support for html messages of any format
support for sockets
it is possible to attach any attach
it is possible to randomize
it is possible to add your own it servers to the databaseAccording to the advertisement and the tool’s site, the developer offers subscriptions for one day ($50), one week ($300), and one month ($1,000), which is double the prices for the email spam service.
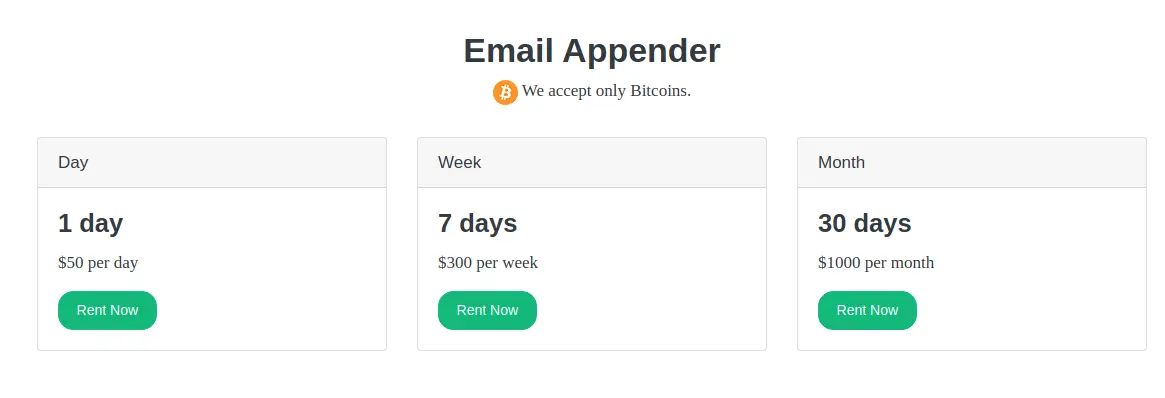
Gemini Advisory told BleepingComputer that the price difference is likely accounted for by the fact that direct email injection is a more sophisticated technique than the standard spam techniques used by GetMailer.
While Email Appender’s method is not new, it provides a much simpler way to inject emails in a thread, enabling less technical actors to run more sophisticated attacks.
The tactic has been in use since at least 2017 in spear phishing attacks and later adopted in cybercriminal campaigns. Among the malware embracing this method are Emotet, Ursnif, Valak, and QBot.
The tool preys on credential stuffing where passwords are reused on multiple services. Credential lists are neither difficult nor expensive to obtain these days.
If valid email credentials are on the list, the tool connects to the account through the Internet Message Access Protocol (IMAP) used to receive messages from a mail server.
“A unique feature of the IMAP protocol allows a properly authenticated user to append a message to their mailbox. An attacker, using this feature, can thus “implant” emails directly into the victim’s mailbox as opposed to sending them through traditional channels”
– Gemini Advisory
The researchers published a demo video from the advertiser showing how a even non-technical attackers could use it for successful compromise.
Also Read: The PDPA Data Breach August 2020: A Recap of 8 Alarming Cases
The concerns stemming from the availability of this tool are obvious: phishing attacks are certain to be more successful, even against targets aware of the threat and in environments where spam detection systems do a good job.
With valid ‘Sender’ and ‘From’ fields, it is easy to bypass defenses and even trick a trained eye to deliver fraudulent messages and malware-laden emails that appear legitimate communication from a trusted sender.
One way to protect against this attack vector is to enable two/multi-factor authentication security feature, which validates the login after the user provides a supplemental code apart from the username and password.
Major email providers also issue alerts when an account is accessed from a different device or IP address than normal.