KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





A heavily obfuscated and malicious NPM project is used to steal Discord user tokens and browser information from unsuspecting users.
NPM is a JavaScript package manager that allows developers to download and integrate different JS modules from a public registry containing over one million packages.
NPM is an open system where anyone can submit modules for other developers to use.
Due to this open system, it is becoming common for malicious actors to upload malicious modules that steal data, download and execute programs, or perform malicious behavior when used in other projects.
On August 25th, 2020, NPM removed a malicious package called “fallguys” designed to steal Discord tokens and browser information from Google Chrome, Brave Browser, Opera, and Yandex Browser.
Today, open-source security firm Sonatype discovered another malicious module that steals browser information and Discord tokens called ‘discord.dll’ that is believed to be a successor to the fallguys module.
Sonatype researcher Ax Sharma told BleepingComputer that it is common for malicious NPM projects to utilize names similar to legitimate projects to trick developers into using them.
Also Read: How To Prevent WhatsApp Hack: 7 Best Practices
“Typosquatting and brandjacking packages capitalize on an existing brand’s value and take advantage of an innocent mistake made by a user,” Sharma explained.
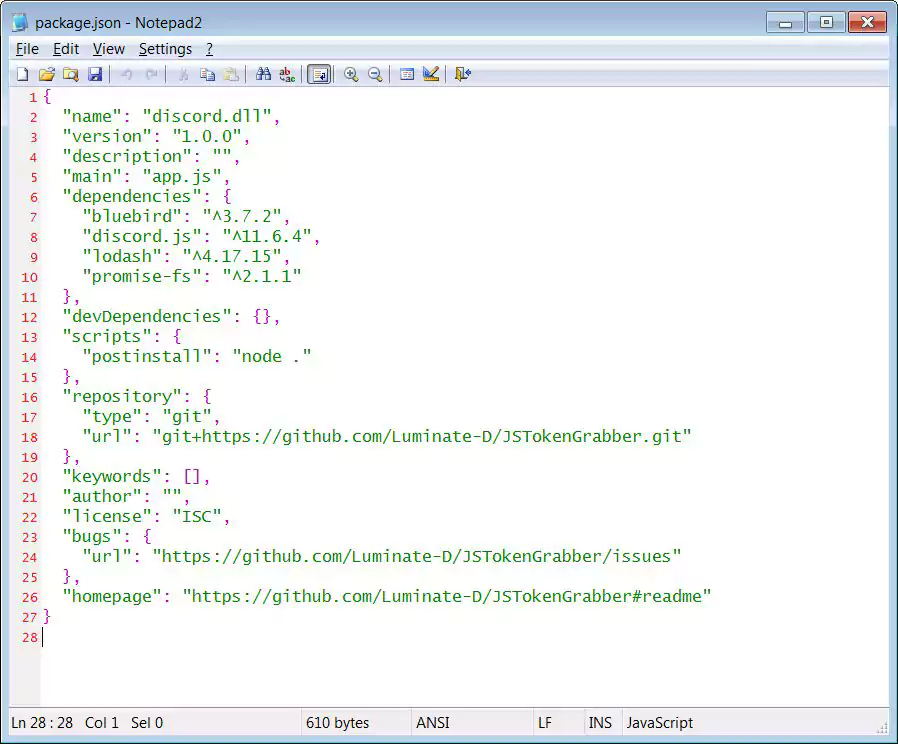
Though it is named discord.dll, its package.json file indicates that the module is based on another project called ‘JSTokenGrabber’ that was previously on GitHub.
When used in a project, the module will attempt to steal Discord user tokens and browser information from the LevelDB databases in the following folders:
From the filenames used in this package, you can see the different components used to perform the theft of information.
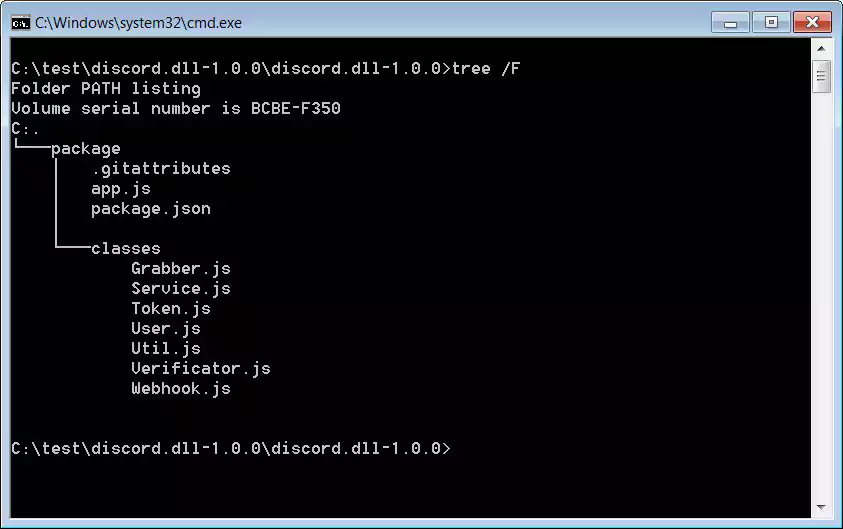
The information that is collected includes:
When done collecting a user’s information, it will be sent via a Discord webhook to a Discord channel under the attacker’s control.
In addition to the discord.dll package, Sonatype also discovered three other suspicious packages from the same author named ‘discord.app,’ ‘wsbd.js,’ and ‘ac-addon’.
Also Read: 15 Best Tools For Your Windows 10 Privacy Settings Setup
When launched, these packages will automatically start executables named ‘bd.exe’, ‘dropper.exe,’ and ‘lib.exe.’
For example, Sonatype states that discord.app will launch the dropper.exe program when it started.
“require('child_process').exec('dropper.exe');”Unfortunately, these programs have not been found, so it unknown what behavior they perform.
The discord.dll project has been available on NPM for five months and has been downloaded one hundred times.
Full disclosure: Ax Sharma contributes articles to BleepingComputer.