KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







An advanced HM Revenue and Customs (HMRC) tax rebate scam is targeting UK residents this week via text messages (SMS).
The smishing campaign is concerning as it employs multiple HMRC phishing domains and tactics, with new domains added every day as older ones get flagged by spam filters.
Not only do the phishing pages mimic HMRC’s web interface meticulously, but they also have entire online banking workflows built into them, depending on who your banking provider is.
As observed by BleepingComputer, the smishing scam starts with a text message informing the recipient that they are eligible for a tax rebate as they had paid “emergency tax” this year.
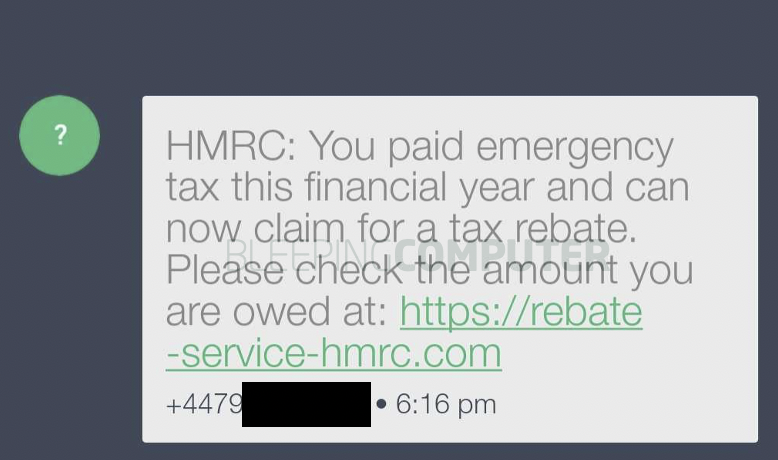
You would think a user would know better not to click on a .com domain for accessing government services. However, some UK government services are offered via “.com” domains to the public.
One such example is householdresponse.com, which mimics the GOV.UK color scheme and UI so well it once had me fooled if it was a phishing domain.
Also Read: Personal Data Websites: 3 Things That You Must Be Informed
Yet householdresponse.com is an entirely legitimate website used by the UK government to collect updates on household voter information from residents.
BleepingComputer has also come across variations of this smishing campaign employing scaremongering tactics, such as texting the user with:”HMRC records show that you are owed a tax repayment of £XXX.XX Failure to submit the return could lead to a fine. Please continue via hmrc.help-rebate.com …”
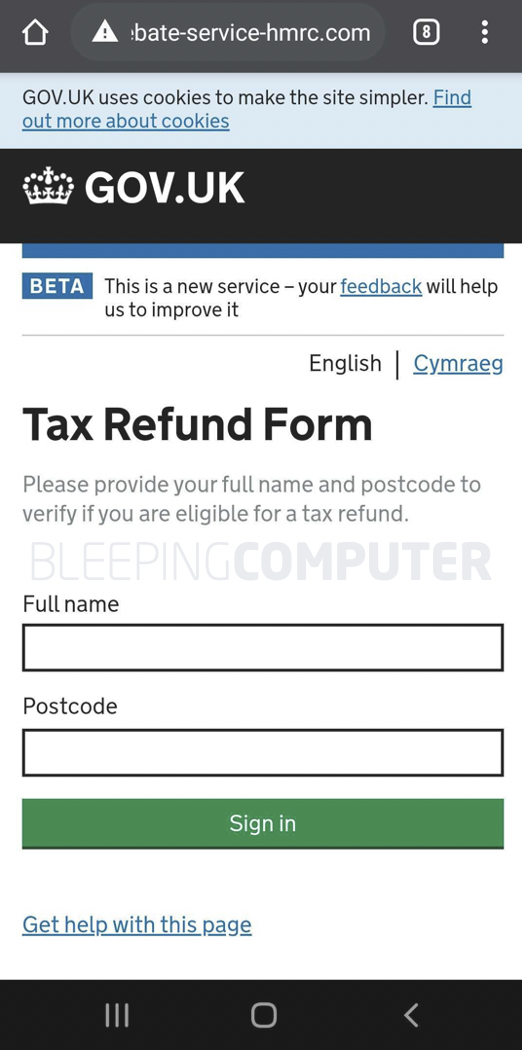
On clicking the link in the message, the user is taken to what looks like a GOV.UK site.
But this isn’t your basic one-page phishing form. The extensive workflow employed by this campaign spans multiple steps and pages.
It starts with a simple Tax Refund claim form asking for the user’s name and postcode.
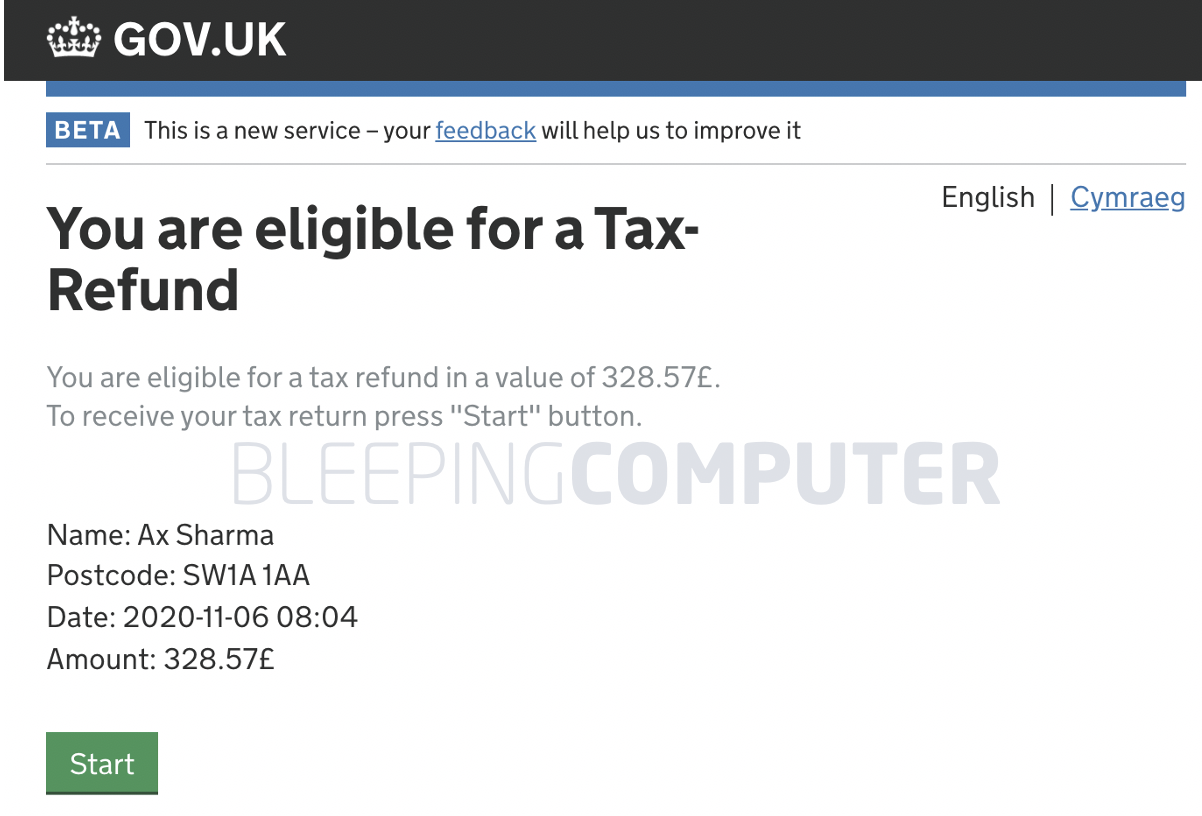
On the next step, the form shows a randomly picked refund amount value between £200 and £400 that the taxpayer is eligible to claim.
On clicking “Start,” the subsequent pages collect a considerable amount of information from the unsuspecting user.
The details collected by this campaign include but are not limited to the following, depending on which phishing domain you are on.
The phishing pages also have validations built into them, so entering invalid values for certain fields would throw errors. This error validation may further trick a user into believing the webpage is legitimate.
The fun begins after some of this information has been submitted by the user.
Also Read: PDPA For Companies: Compliance Guide For Singapore Business
A “processing” interstitial page is shown validating some of the fields gathered thus far.
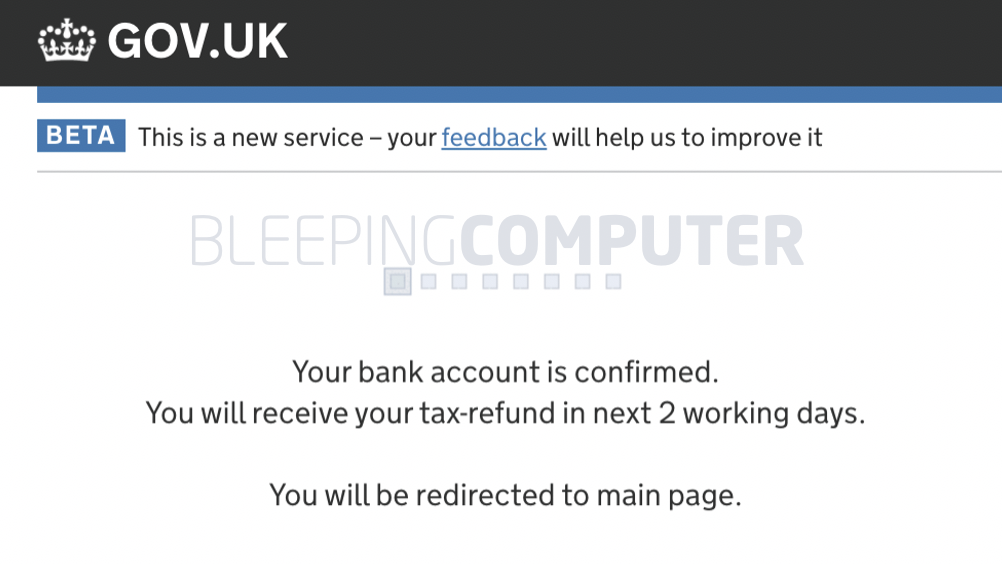
In tests by BleepingComputer, the workflow exited at this step, and the user was redirected to the real HMRC website.
However, in other tests where a real bank branch sort code was entered, and the test data provided would seem ‘real’ enough to a machine, we observed the redirection would lead to the online banking phishing pages hosted on the same phishing domain.
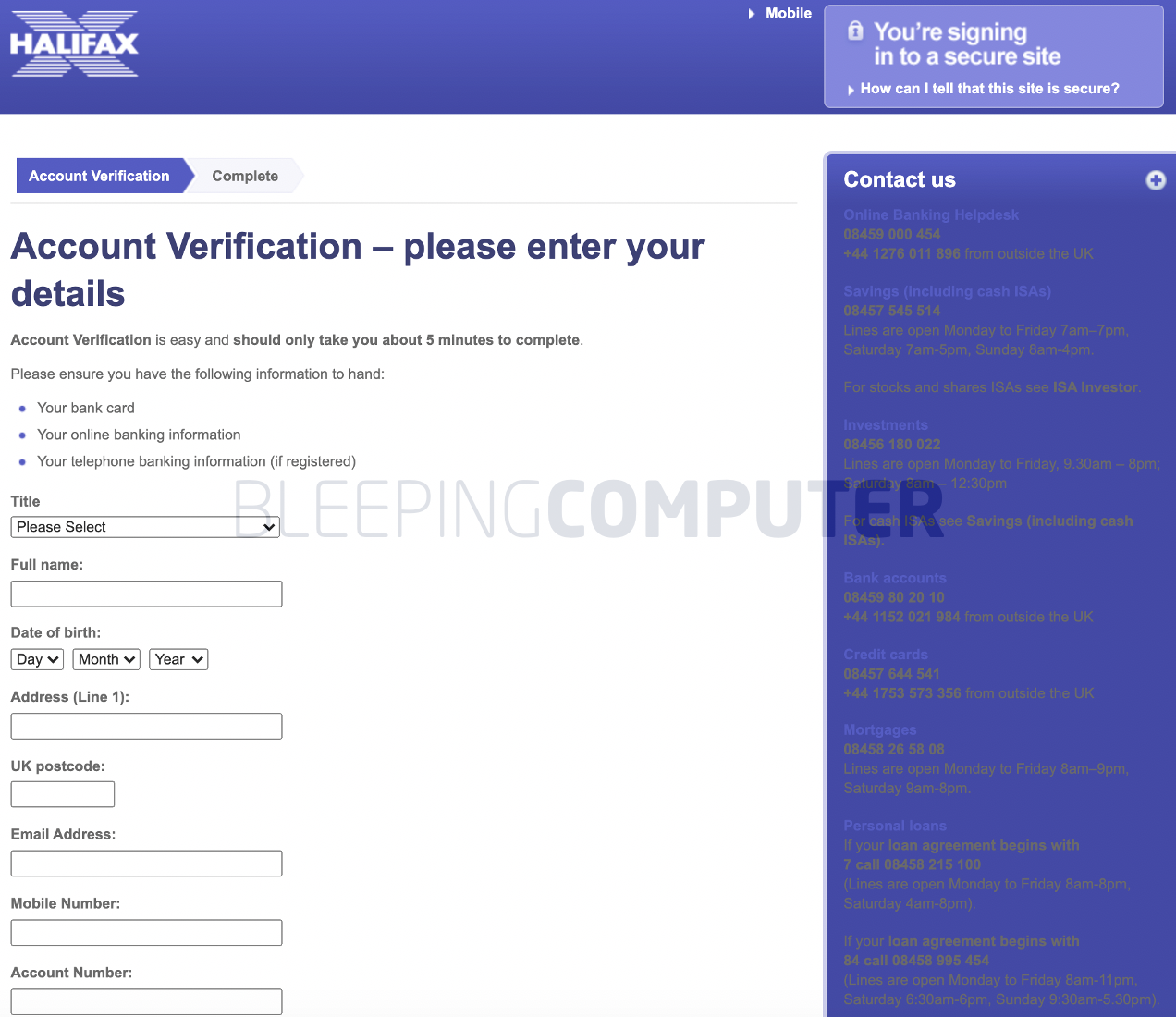
BleepingComputer tested the phishing pages with real Halifax and NatWest bank branch sort codes, which confirmed our suspicions.
These online banking lookalikes further collect user’s banking credentials, memorable words, 2-factor codes, etc.
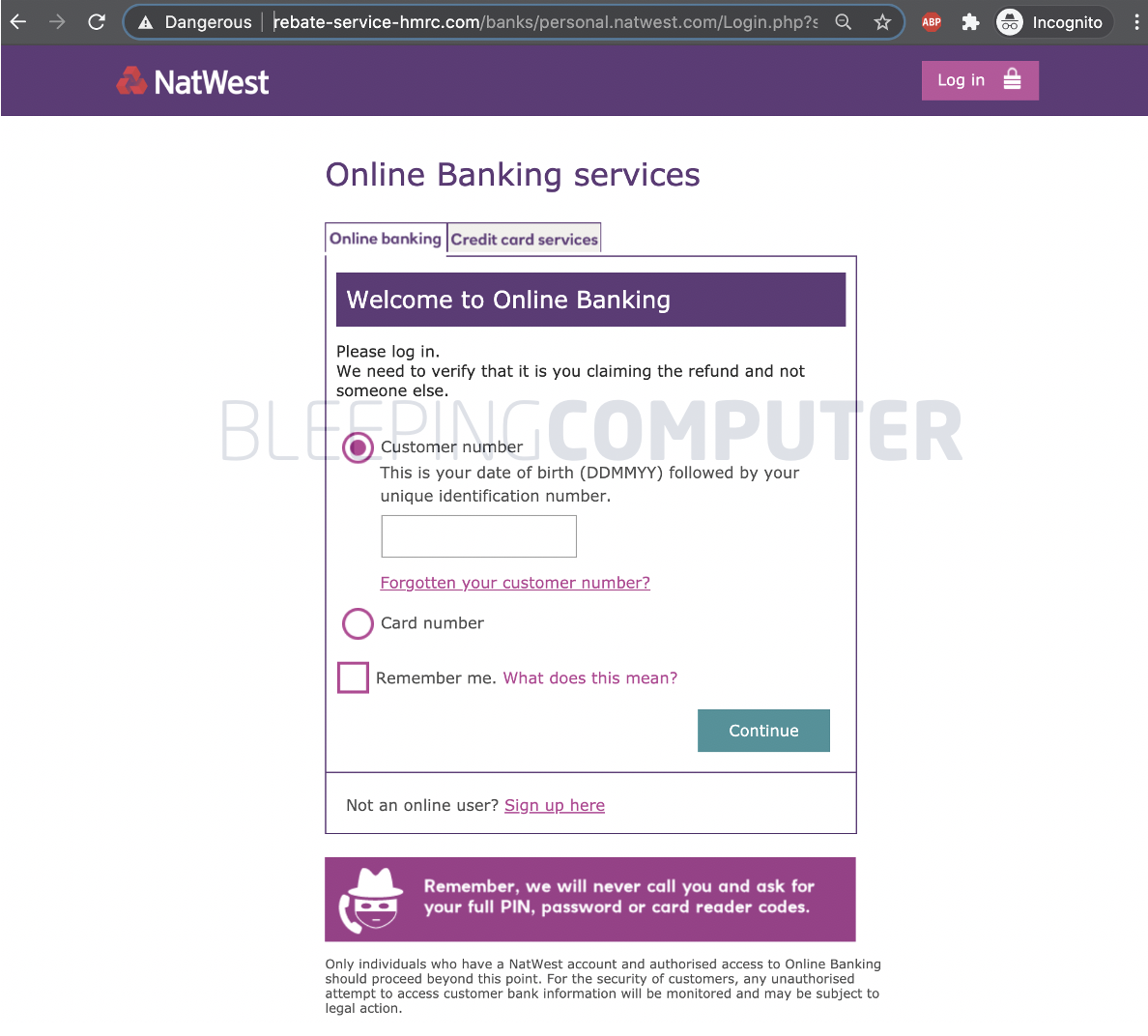
BleepingComputer discovered, the campaign has entire sets of phishing sites mirrored from real websites of prominent UK high street banks to target their customers.
The list includes Barclays, Clydesdale, Halifax, NatWest, HSBC UK, Metro Bank, Nationwide, Citi, Lloyd’s, TSB, Co-op, Royal Bank of Scotland (RBS), Santander, Tesco Bank, and Yorkshire Bank.
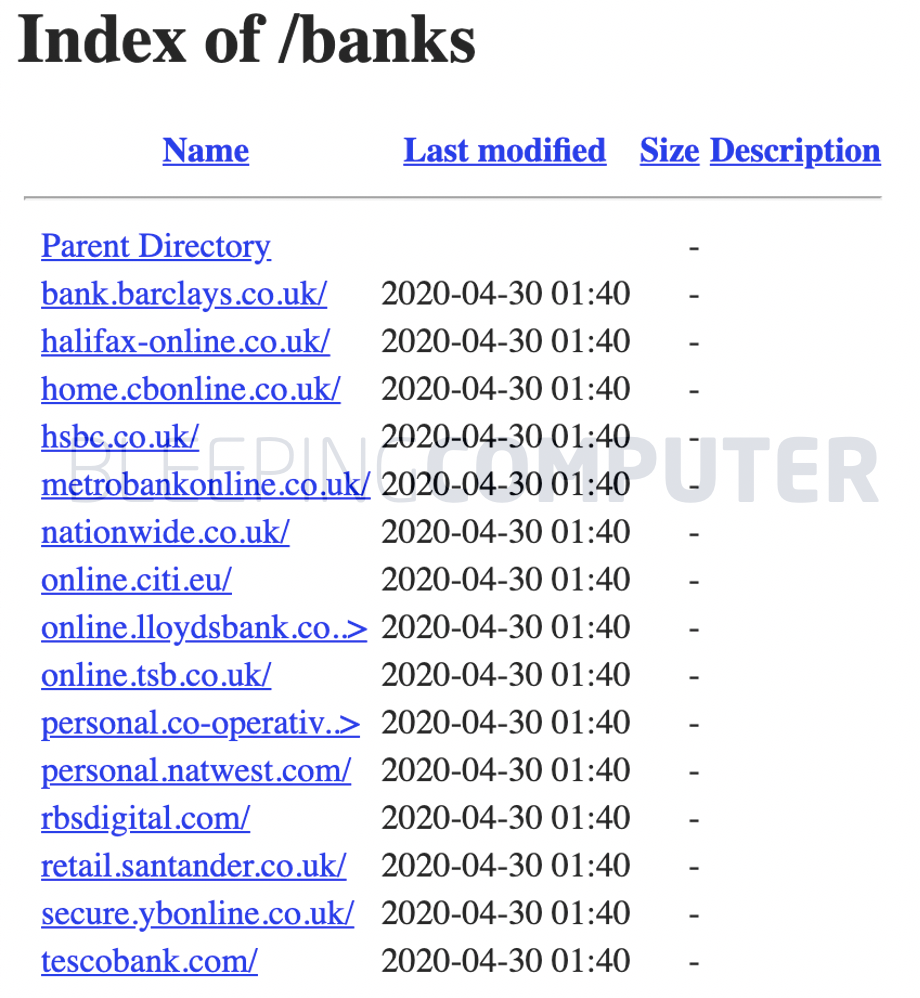
Despite the thoroughness of the threat actors behind this campaign, they didn’t do a splendid job of securing the collected data—hardly their concern, which makes this campaign even more dangerous.
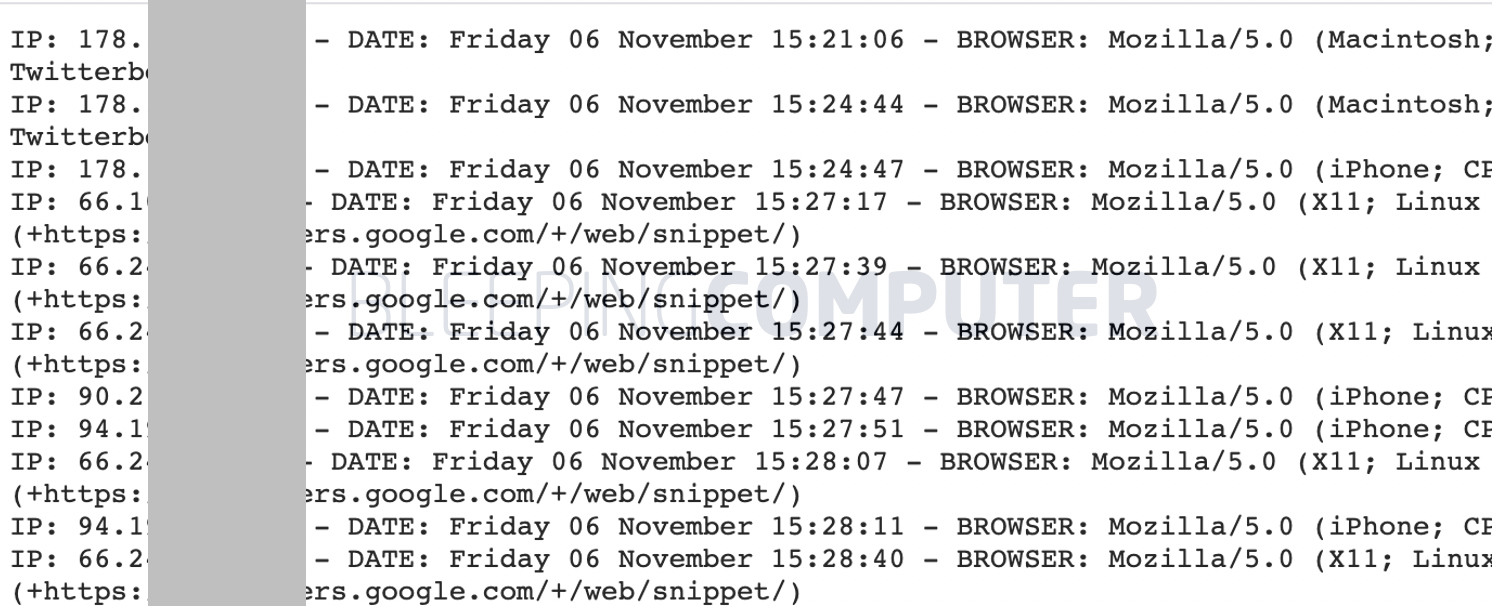
One phishing domain used by the campaign was observed leaking visitor logs with over 4,500 records. The domain leaking these logs is no longer accessible.
On analyzing the logs, BleepingComputer discovered, well over 1,000 unique IPs had accessed this phishing campaign.
At the time of writing, BleepingComputer has observed the following domains associated with this campaign, some of which are still active:
hmrc-online-verify.com
hmrc.help-rebate.com
hmrcsupport.com
rebate-service-hmrc.com
taxclaim-govuk.com
Spam blocklist maintainers are constantly catching up and adding these malicious domains to their databases.
It is also interesting to note that these domains were registered quite recently.
For example, hmrc-online-verify.com has a November 4th, 2020 registration date, with the other domains having been registered on subsequent days.

The extensive nature of this campaign and thoroughly built online banking workflows indicate this is a well-planned smishing project designed by skilled threat actors.
If you have received similar suspicious messages, phone calls, or emails that claim to come from HMRC, you are encouraged to report these to HMRC.
Additionally, you may also report instances of such scams to BleepingComputer using our online form.
Update November 9, 2020: Added taxclaim-govuk.com domain to list.