KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Phishing campaigns have started to use Basecamp as part of malicious phishing campaigns that distribute malware or steal your login credentials.
Basecamp is a web-based project management solution that allows people to collaborate, chat with each other, create documents, and share files.
When creating documents, they can be formatted with HTML links, images, and stylized text. Basecamp also allows users to upload any file to a project, including file formats that are usually considered unsafe such as executables, JavaScript files, etc.
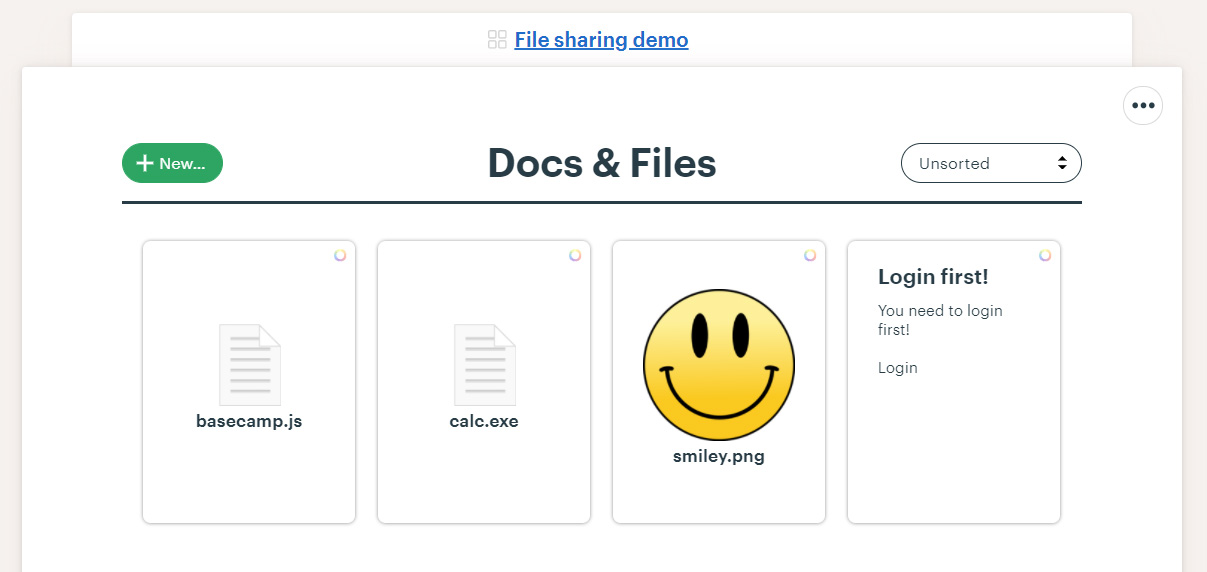
To publicly share uploaded files, users can create a public link that allows people outside the organization to preview the file and download it.
Also Read: 5 Assessment Tools To Find The Right Professional Fit
When users click on this link [example shared file], they will be brought to a page that previews the file and includes another link to download the file to your computer.
As Basecamp offers a free license, users get free hosting that they can use to distribute any type of file they want.
Security researchers MalwareHunterTeam and James have found that threat actors are distributing BazarLoader executables using public Basecamp download links.
BazarLoader is a stealthy backdoor Trojan from the TrickBot gang used against high-value targets to compromise their networks. Once installed, BazarLoader will deploy Cobalt Strike beacons that allow threat actors to access the network and ultimately deploy the Ryuk ransomware.
By abusing safe services such as Basecamp to host malicious files and phishing pages, users can be lulled into a false sense of trust and open files that they normally would not.
Furthermore, by using Basecamp URLs, threat actors can create carefully constructed and targeted campaigns to infiltrate a network as users may feel that the file is from their Basecamp project.
Due to this, it is always essential for everyone to treat all shared links or downloads as suspicious, regardless of where they originate.
This week security researcher Will Thomas discovered that threat actors are also abusing Basecamp as part of phishing campaigns.
Also Read: Best Privacy Certification: 3 Simple Steps On How To Achieve
In a report by cybersecurity firm Cyjax, Thomas explains that phishing campaigns are now abusing Basecamp to host intermediary pages that redirect users to phishing landing pages.
As Basecamp is considered a trusted service, it allows threat actors to create pages that bypass security solutions that it as safe traffic.
“This technique is effective because Basecamp and Google Cloud hosting are often used for business operations and are regarded as safe by default by most detection systems. Cloud platforms also preserve the anonymity of their users and can be set up in no time at all. They are difficult for human SOC analysts to recognise as a threat because the traffic to and from these services appears legitimate,” Thomas explains in his report.
For example, Thomas discovered a recent Phishing campaign that used a shared Basecamp document to redirect to a phishing Office 365 credential phishing page.
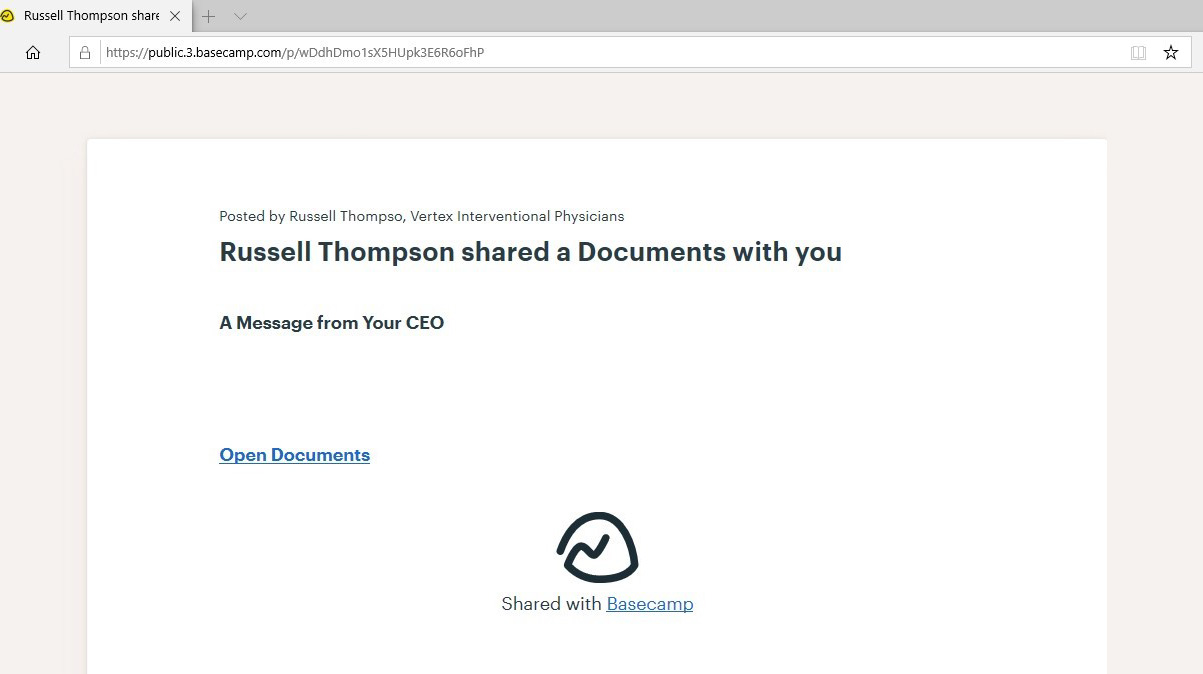
In addition to security solutions seeing the referer as “safe” traffic, the advantage of using Basecamp for intermediary pages is that they can be edited as needed.
Suppose a phishing landing page is taken down. In that case, the threat actors can simply log into Basecamp and modify their intermediary page to redirect to a different page to steal login credentials.
This ability allows threat actors to keep a campaign alive even when their phishing pages are removed.