KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Federal Bureau of Investigation (FBI) issued a flash alert to warn of the potential use of spoofed US Census Bureau domains in future malicious campaigns including phishing and credential theft attacks.
The US Census Bureau is a federal government statistical agency that collects statistical data on the US economy and population, data used by the federal government to allocate over $675B in federal funds to tribal, local, and state governments each year.
The flash alert was published by the FBI Cyber Division in coordination with DHS’Office of Intelligence & Analysis, DHS-CISA, the Department of Commerce, and the Census Bureau.
“The FBI has observed entities not associated with the US Census Bureau registering numerous domains spoofing the Bureau’s websites, likely for malicious purposes,” the US intelligence and security service says.
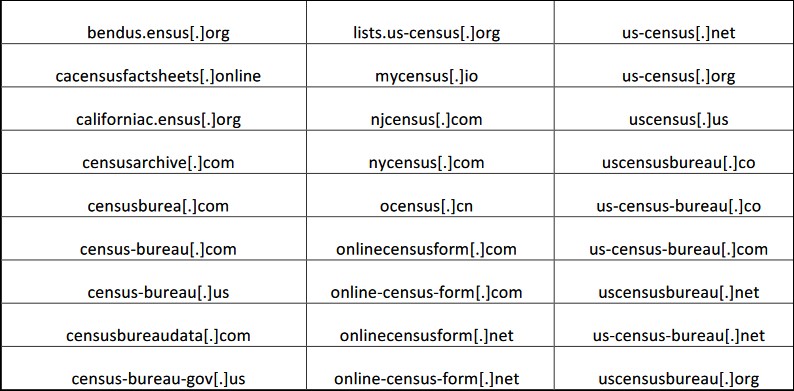
“Spoofed domains (aka typosquatting) mimic legitimate domains by either altering character(s) within the domain or associating another domain with similar characteristics to the legitimate domain, such as ‘Censusburea[.]com’ or “census-gov[.]us’.”
Although there are no signs that the lookalike domains have already been used in attacks, they could be used in the future by both nation state-backed hacking groups and cyber-criminals to spread malware as part of espionage or financially motivated campaigns targeting individuals and businesses.
Also Read: The Importance Of DPIA And Its 3 Types Of Processing
The FBI also provides a list of recommended mitigations just in case these lookalike domains will get used in future malicious campaigns:
• Users should pay close attention to the spelling of web addresses, or websites that look trustworthy but may be close imitations of legitimate Census Bureau websites.
• Devise a continuity of operations plan for a potential cyber-attack; prioritize the systems most important to continued operations.
• Ensure the SSL (Secure Sockets Layer) certificate is present, and the top-level domain is “.gov” for the website.
• Regularly patch operating systems, software, and firmware.
• Update anti-malware and anti-virus software and conduct regular network scans.
• Use multi-factor authentication where possible.
• Audit networks and systems for unauthorized remote communication.
• Disable or remove unneeded software, protocols, macros, and portals.
The full list of 63 domains with names similar to legitimate Census Bureau domains registered by unknown entities in this recent typosquatting campaign is available in the flash alert.
The US Department of Homeland Security (DHS) also said in its first-ever Homeland Threat Assessment (HTA) report released two weeks ago that unknown threat actors have already targeted the US Census network multiple times during the last year.
“Unidentified cyber actors have engaged in suspicious communications with the U.S. Census public-facing network over at least the last year, including conducting vulnerability scans and attempting unauthorized access,” the DHS said.
Also Read: Data Storage Security Standards: What Storage Professionals Need to Know
“Cyber activity directed at the U.S. Census could include attempts to gain illicit access to census-gathered bulk data; to alter census registration data; to compromise the census infrastructure supply chain, or conducting denial-of-service attacks.”
The US Census was also targeted by attackers two years ago as highlighted by a Reuters report on hacks and DDoS attacks during a 2018 test of census systems, with Russian IP addresses being involved in at least one of the reported incidents.
“As part of the US government’s facilities sector, the Census Bureau remains a target for both criminal and nation-state actors aiming to negatively affect the US Government and create distrust among US citizens,” the FBI added.
“In order to prevent website confusion for site visitors, the Census Bureau is actively working to disable spoofed domains.”