KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Researchers tracking malicious use of parked domains have spotted the Emotet botnet using such domains to deliver malware payloads as part of a large scale phishing campaign.
Domain owners park their domains using parking service providers to monetize them via advertisement networks while they’re not being used to host an active website or online service.
Out of 6 million newly parked domains detected as parked between March and September 2020 by Palo Alto Networks, roughly 1% started being used as part of malware or phishing campaigns.
“Often, the parking services and the advertisement networks do not have the means or willingness to filter abusive advertisers (i.e. attackers),” Palo Alto Networks.
“Therefore, users are exposed to various threats, such as malware distribution, potentially unwanted program (PUP) distribution, and phishing scams.”
Also Read: What Legislation Exists in Singapore Regarding Data Protection and Security?
The attacks targeted potential victims from multiple countries around the world including the United States, the United Kingdom, France, Japan, Korea, and Italy according to researchers with Palo Alto Networks’ Unit 42 threat intelligence team.
Emotet’s campaign focused on several industry sectors ranging from government and education to energy, manufacturing, construction, and telecommunications.
One of the domains used in these attacks, valleymedicalandsurgicalclinic[.]com, was first registered on July 8, 2020, and was immediately parked according to Unit 42’s parking detector.
Starting with September 14, only two months after its initial registration, the domain turned malicious and was seen delivering various malware samples.
Additionally, it was used to spread Emotet payloads via phishing emails that led to credential theft and takeover of the infected devices.
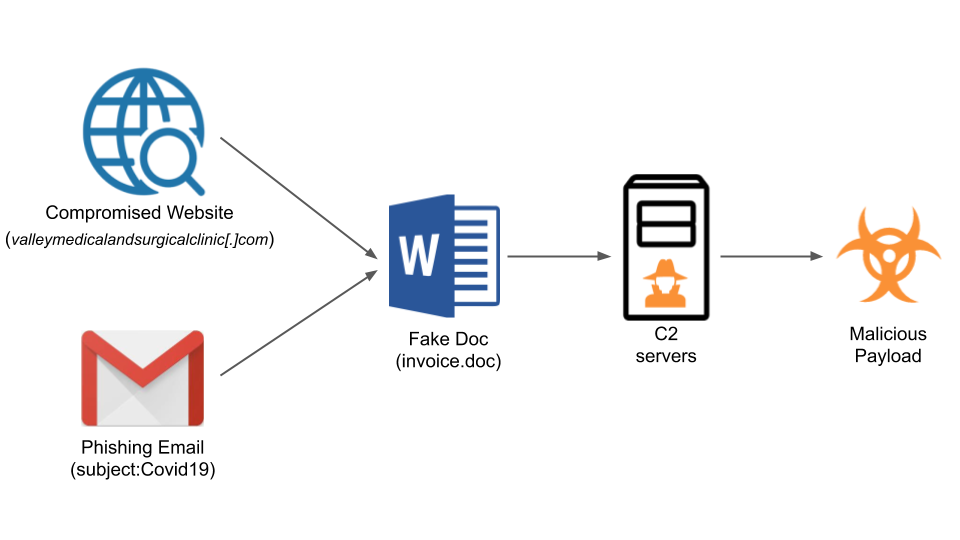
“The documents attached to the phishing emails contain macro scripts that call back to the C2 servers from victims’ machines,” Unit 42 explains.
“Emotet further downloads Trojan payloads that steal victims’ credential information or even compromises their machines.”
Some of the Emotet attacks directed at French organizations also employed COVID-19-themed baits designed to exploit the targets’ anxiety regarding the current pandemic, but none of these attacks were successful.
Emotet, initially a banking Trojan, when it was first spotted in 2014, has now evolved into a botnet used by the TA542 threat group (also tracked as Mummy Spider) to deliver second-stage malware payloads on compromised devices.
The payloads dropped by Emotet include the QakBot and Trickbot (an infection vector used to deploy both Ryuk and Conti ransomware) trojans.
Also Read: Advisory Guidelines on Key Concepts in the PDPA: 23 Chapters
Since it came back online in July after 5 months of silence, Emotet has consistently ranked first in a list of top 10 malware strains analyzed on the interactive malware analysis platform Any.Run.
As the Cybersecurity and Infrastructure Security Agency (CISA) disclosed in an advisory published on October 6, Emotet has targeted multiple US state and local governments in potentially targeted campaigns that have been ramping up since August.
Starting with July, the “EINSTEIN Intrusion Detection System, which protects federal, civilian executive branch networks” detected around 16,000 Emotet-related alerts according to CISA.
CISA advises admins and users to be cautious when opening suspicious email attachments, to use anti-malware software, and to block suspicious IPs addresses to protect their networks and devices against Emotet attacks.