KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





Cybercriminals are making strides towards attacks with malware that can execute code from the graphics processing unit (GPU) of a compromised system.
While the method is not new and demo code has been published before, projects so far came from the academic world or were incomplete and unrefined.
Earlier this month, the proof-of-concept (PoC) was sold on a hacker forum, potentially marking cybercriminals’ transition to a new sophistication level for their attacks.
Also Read: Lessons from PDPC Incident and Undertaking: August 2021 Cases
In a short post on a hacker forum, someone offered to sell the proof-of-concept (PoC) for a technique they say keeps malicious code safe from security solutions scanning the system RAM.
The seller provided only an overview of their method, saying that it uses the GPU memory buffer to store malicious code and to execute it from there.
According to the advertiser, the project works only on Windows systems that support versions 2.0 and above of the OpenCL framework for executing code on various processors, GPUs included.
The post also mentioned that the author tested the code on graphics cards from Intel (UHD 620/630), Radeon (RX 5700), and GeForce (GTX 740M(?), GTX 1650).
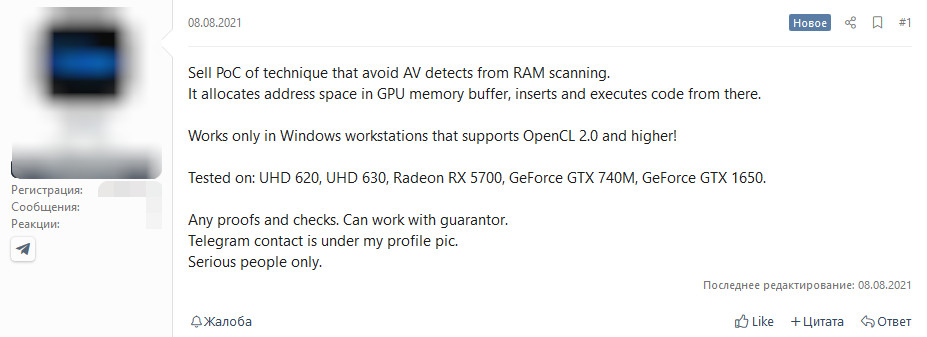
The announcement appeared on August 8. About two weeks later, on August 25, the seller replied that they had sold the PoC without disclosing the terms of the deal.
Another member of the hacker forum indicated that GPU-based malware has been done before, pointing to JellyFish – a six-year PoC for a Linux-based GPU rootkit.
In a tweet on Sunday, researchers at VX-Underground threat repository said that the malicious code enables binary execution by the GPU in its memory space. They also added that they will demonstrate the technique in the near future.
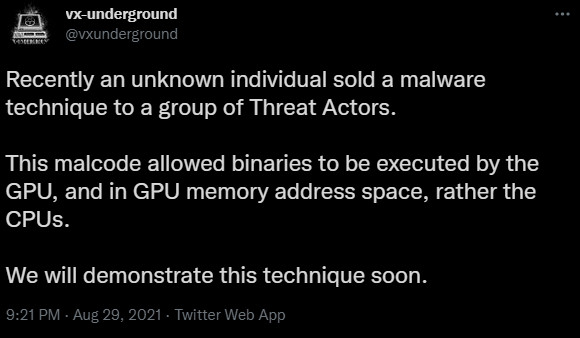
The same researchers behind the JellyFish rootkit also published PoCs for a GPU-based keylogger and a GPU-based remote access trojan for Windows. All three projects were published in May 2015 and have been publicly available.
The seller rejected the association with the JellyFish malware saying that their method is different and does not rely on code mapping back to userspace.
There are no details about the deal, who bought it and how much they paid. Only the seller’s post that they sold the malware to an unknown party.
While the reference to the JellyFish project suggests that GPU-based malware is a relatively new idea, the groundwork for this attack method has been set about eight years ago.
In 2013, researchers the at Institute of Computer Science – Foundation for Research and Technology (FORTH) in Greece and at Columbia University in New York showed that GPUs can host the operation of a keylogger and store the captured keystrokes in its memory space [PDF paper here].
Previously, the researchers demonstrated that malware authors can take advantage of the GPU’s computational power to pack the code with very complex encryption schemes much faster than the CPU.