KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A very clever phishing campaign targets bloggers and website owners with emails pretending to be from their hosting provider who wants to upgrade their domain to use secure DNS (DNSSEC).
As it’s possible to determine who is hosting a domain for a website via the WHOIS records, IP addresses, and HTTP headers, the email scam is highly targeted and impersonates the specific hosting company used by a website.
In a new report by Sophos, researchers explain how the scammers are using this WHOIS information to send targeted emails that impersonate WordPress, NameCheap, HostGator, Microsoft Azure, and other well-known hosting companies.
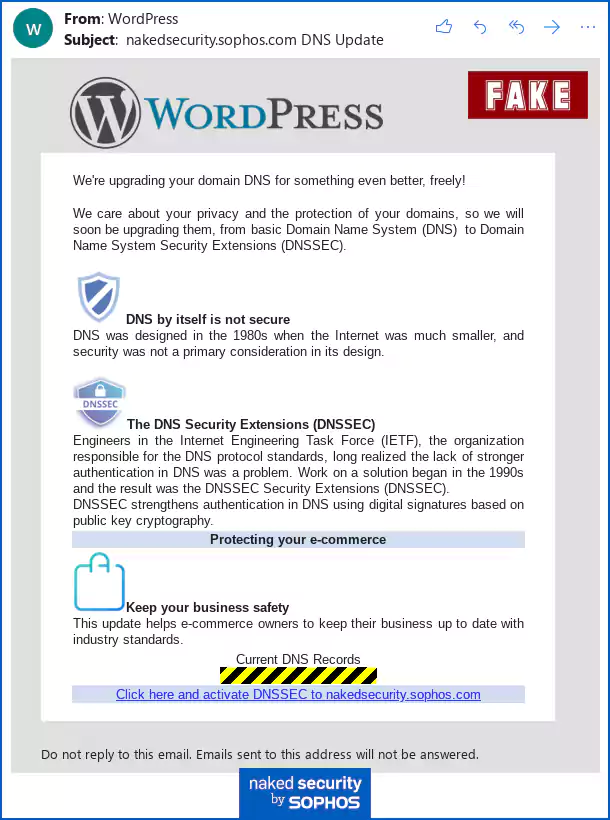
The security company was first alerted to this scam when they received the phishing scam pretending to be WordPress, who hosts their NakedSecurity blog.
Domain Name System (DNS) is the technology that is analogous to a real-world “phone book.” It maps and resolves the memorable domain names such as bleepingcomputer.com into the corresponding IP address of the server (in this case, 104.20.59.209), where the website is hosted.
There is a newer protocol, DNSSEC, that exists to provide extra security to DNS queries and responses. This feature is typically implemented as a safeguard by domain hosting providers to prevent DNS data from being tampered.
These phishing emails state that the website’s DNS provider will be upgrading their DNS to secure DNS (DNSSEC), but need them to click on a link to activate this enhanced security feature.
Sophos’ report explains that DNSSEC is not something website owners would typically setup on their own.
“You’ve probably never set up DNSSEC or used it directly yourself because it has typically been a feature used by service providers to help to keep their DNS databases intact when they exchange data with other DNS servers,” the report explained.
Considering most independent bloggers and webmasters would seldom have a reason to look into DNSSEC, the spammers exploit their curiosity and fear through this campaign.
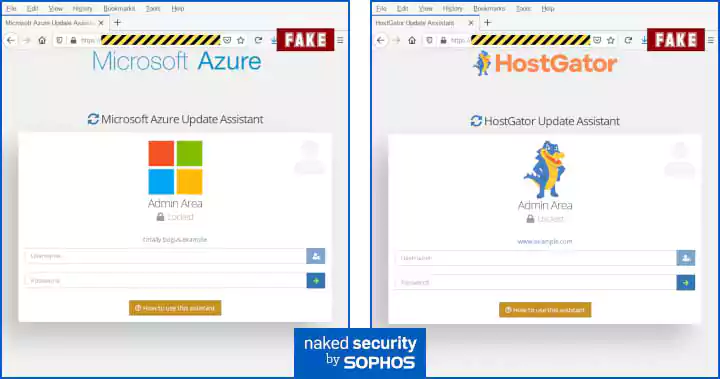
Once the malicious links in the email are clicked, a “surprisingly believable” Update Assistant page is generated on the fly.

Of interest, is that these pages are dynamically generated based on the base64-encoded GET parameters in the URL. These parameters instruct the backend to render the page with the appropriate website name, logo, and the URL of the client website.
For example, the link within the phishing email Sophos team received, had the base64 encoded “banner” parameter set to WordPress, which is their hosting provider, and the “URL” set to base64-equivalent of “nakedsecurity.sophos.com”
Also read: Cost of GDPR Compliance for Singapore Companies
The Sophos team further demonstrated how they could simply alter these two parameters, and new pages would be generated on the fly to impersonate different hosting providers.
As the attackers forgot to turn off directory indexing on their malicious phishing domain, Sophos could see all the logos of different hosting providers they had hosted on their server.
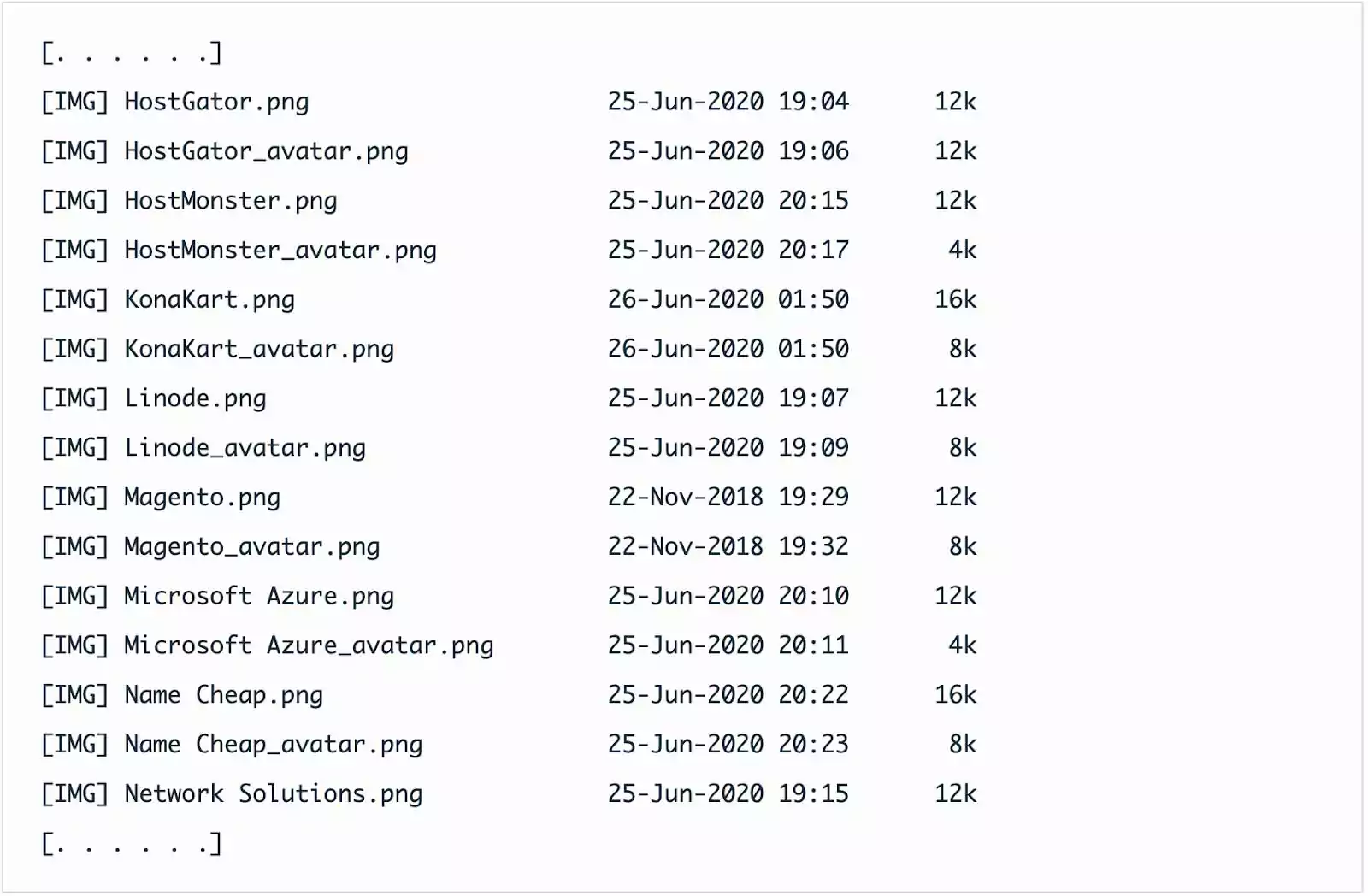
Some prominent names of hosting companies impersonated include HostGator, HostMonster, KonaKart, Linode, Magento, Microsoft Azure, NameCheap, and Network Solutions.
The goal of this phishing campaign is to steal credentials from unsuspecting users rather than offering them any legitimate DNSSEC protection service.
Once the user enters their credentials, the malicious website pretends to kick off a series of installation and “update” sequences, using bogus AJAX-style loaders and popup alerts, imitating an installation.
Users are told that once the update completes, they will be redirected to their website. But this doesn’t happen, perhaps due to a programming error on the scammers’ part.
“As you can see, the crooks claim that you’ll be redirected to your own site at the end of the process, but instead you end up at a URL that includes the name of your site preceded by the name of the fake site set up by the crooks. This produces a 404 error – what we can’t tell you is whether the crooks made a programming blunder and accidentally redirected you to https://[THEIRDOMAIN]/your.example instead of directly to https://your.example or whether they intended this all along, to avoid redirecting to you directly to your own login page, which might seem suspicious given that you put in your username and password already,” Sophos states in their report.
As a general rule, to safeguard against scams like these, email recipients should be mindful of the links they click in an email and especially when entering their credentials on unfamiliar sites and systems.
Enabling two-factor authentication can also help deter phishing attacks that attempt to steal login credentials.
Also read: 6 Simple Tips on Cyber Safety at Home