KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





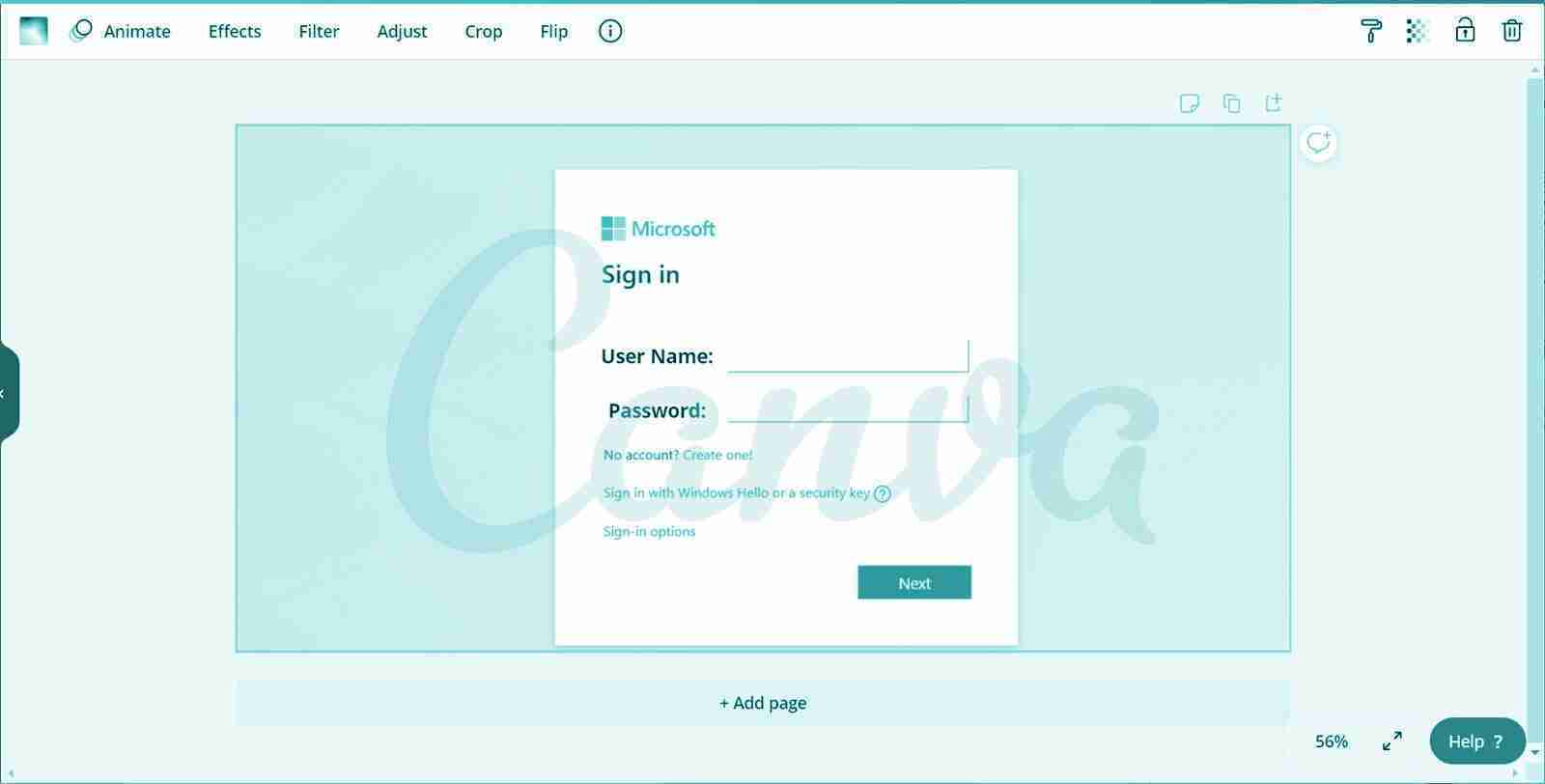
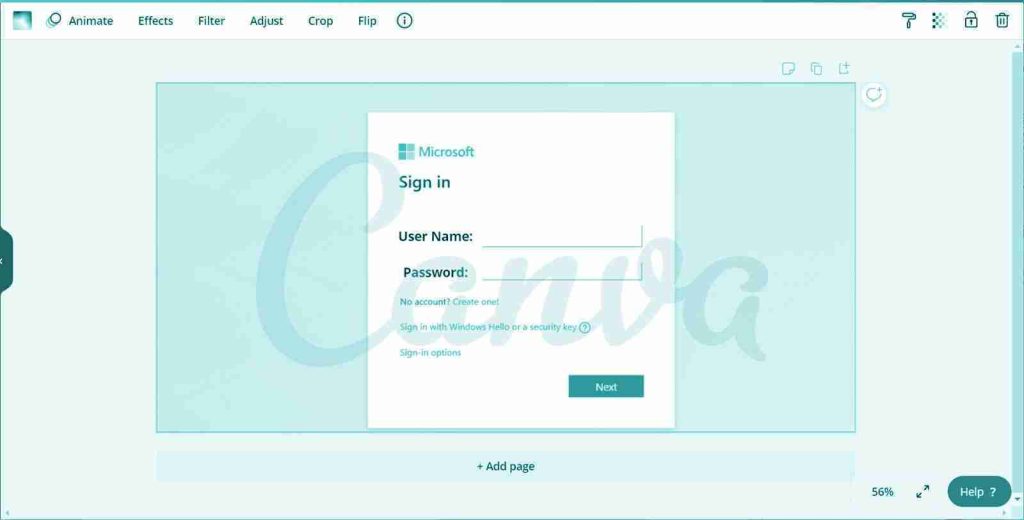
Free graphics design website Canva is being abused by threat actors to create and host intricate phishing landing pages.
Canva is a graphic design platform that lets users create posters, letterheads, holiday cards, and other digital media that can then be downloaded as an image, shared as HTML with clickable links, or printed.
As part of its service, designers can generate shareable URLs so that friends and colleagues can view their work on canva.com.
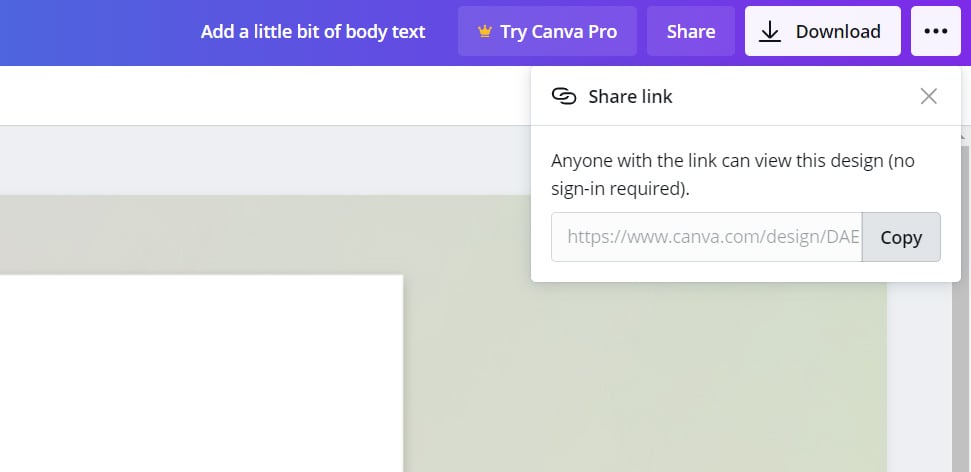
When sharing designs, a user who clicks on the link will see a full-page view and be able to interact with any embedded links or forms.
Also Read: How To Anonymised The Data: What Are The Importance Of This?
In a new report by cybersecurity firm Cofense, threat actors are increasingly using Canva to create hosted HTML landing pages that are then used to redirect phishing victims to fake login forms.
As you can see from the spam email below, threat actors conduct a Phishing campaign pretending to be SharePoint eFax delivery notification. Embedded in this notification is a link to a phishing landing page hosted on canva.com.
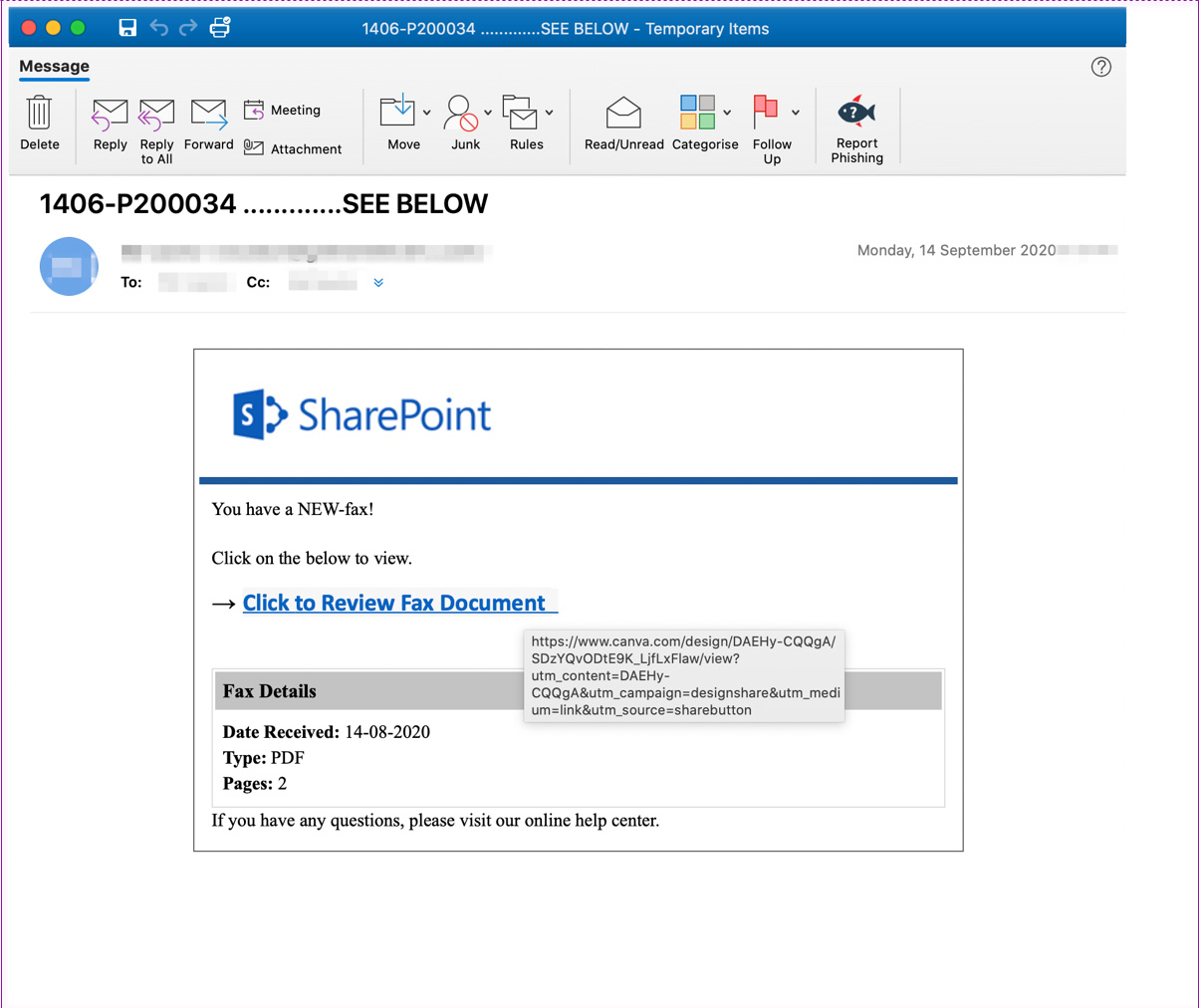
When a phishing victim clicks on the link, they will be brought to a Canva-designed intermediary HTML page hosted on Canva.com. This landing page pretends to be information about the Fax you received, with a clickable link that states it can be used to review the fax document.
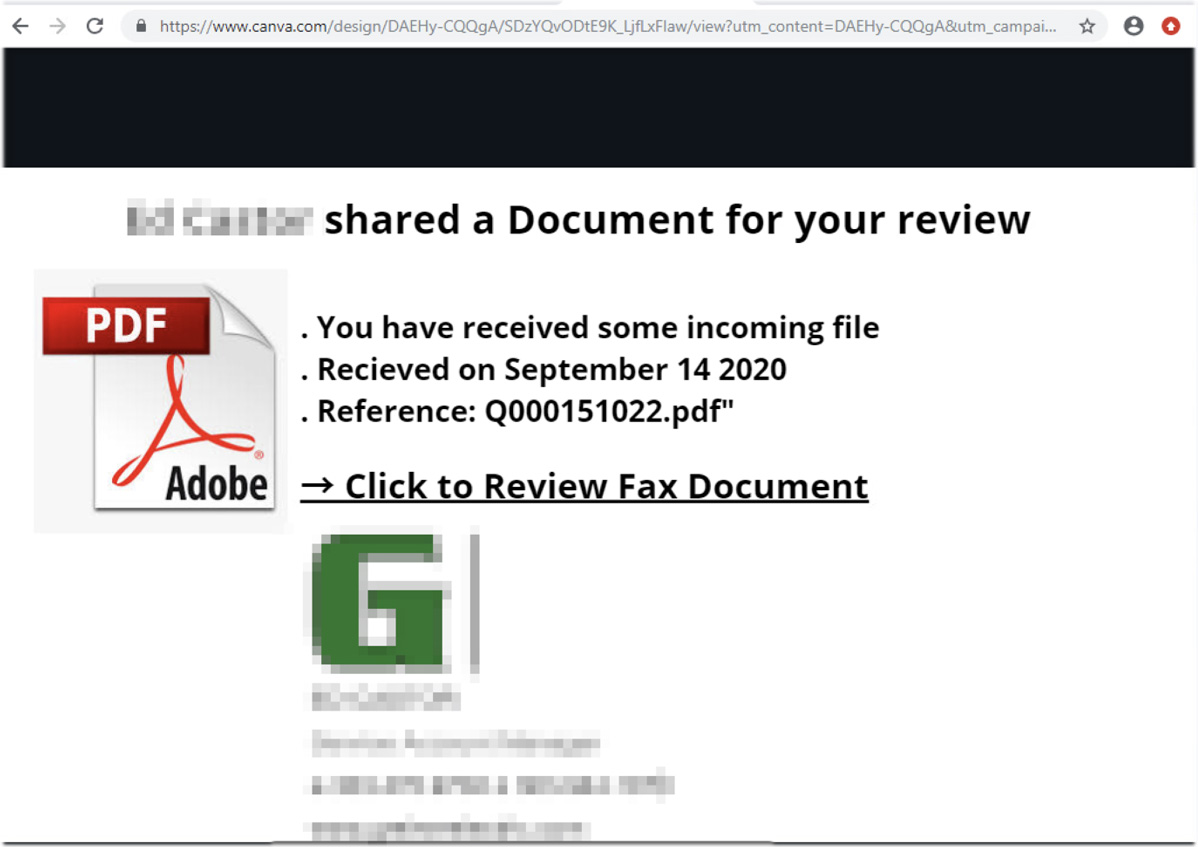
Clicking on the link brings a victim to the final phishing landing page, where they are prompted to log in to see the document.
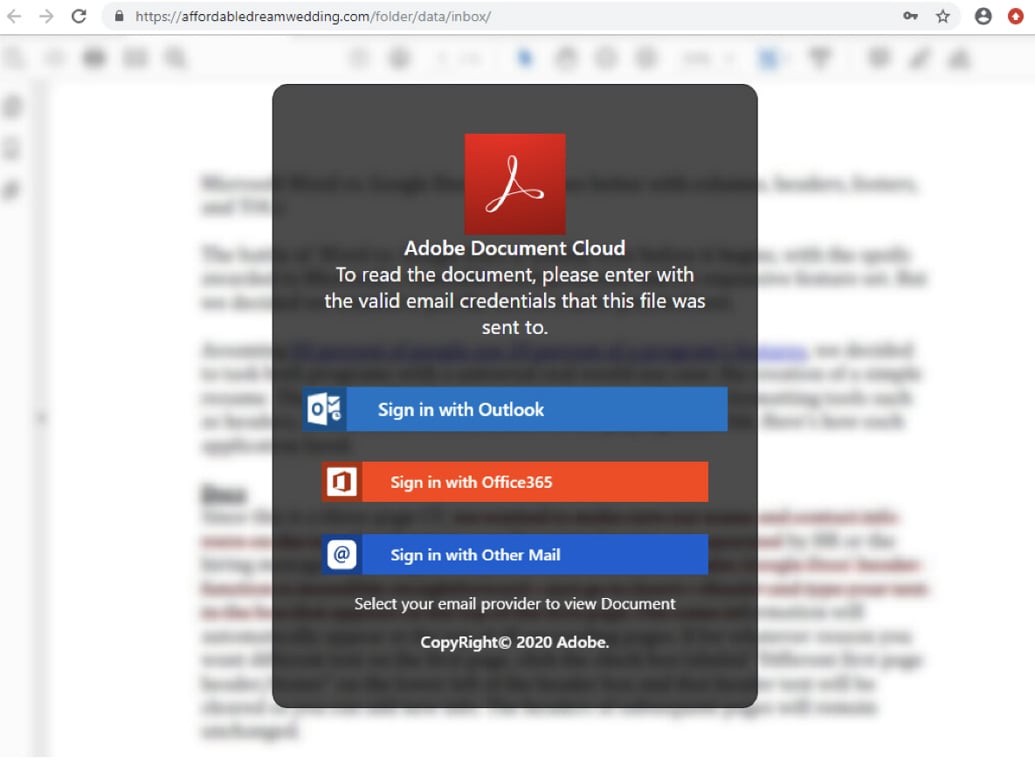
As you can expect, any login credentials you enter into this page will be stolen by the attackers.
Also Read: Trusted Data Sharing Framework IMDA Announced In Singapore
It may be confusing why phishing campaigns are using Canva to host their pages rather than Google Docs, Sheets, or even Dropbox.
The likely reason is that Google and Dropbox have a long history of dealing with malicious threats and have better systems in place to detect and remove them.
Canva, on the other hand, is not designed to be a hosting platform but rather a platform for creating content that is not generally associated with malicious behavior.
Due to this, Cofense has found them to be far less efficient at finding hosted threats, and the landing pages tend to stay active for longer periods.
“Canva is probably aware of the problem, removing malicious files as and when they’re found but, as our research has concluded, many of these malicious files have remained on Canva’s hosted platform for hours and even days at a time. Sites, such as Google where hackers have traditionally hosted their phishing emails, appear to be a lot faster in detecting and removing them, which is another reason threat actors have begun to exploit the Canva platform,” Cofense explains in their report.
Furthermore, using Canva as an intermediary redirect page, when the final phishing landing page is taken down, the attackers can update their Canva designs to point to a new final phishing URL so that their campaign is not broken.