KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







As the weakest link to an organisation’s cybersecurity, every organisation should ensure that its employees are properly trained and made aware of various forms of phishing scams that could bait them into giving their access to the organisation.
Since phishing scams are rampant and come in various forms, having the employees be knowledgeable to know the difference between a legitimate transaction from a spoofed one goes a long way toward the organisation safety and security.
The following are the 10 templates that organisations could use to train their employees so that when bad actors are targeting them, they will never fall for it as they already have exposure to their tactics.
Also Read: Trackers are following Singaporeans online: They are the 2nd highest number per site!
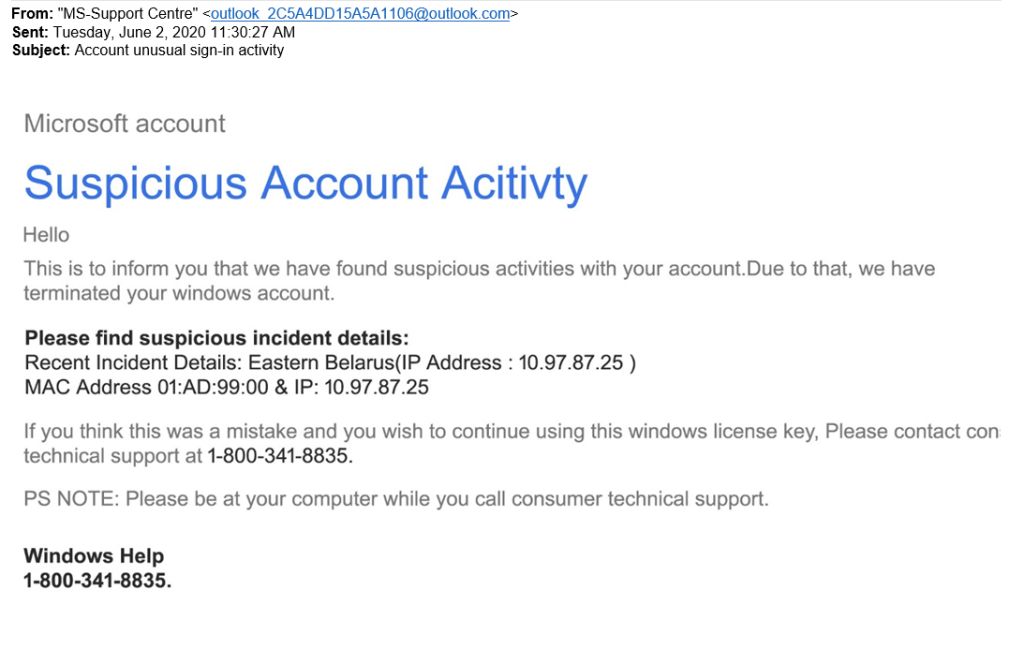
This attack plays on the fear that someone you don’t know will get into your account and look through your sensitive information. This is enough to make many people act without thinking and take the bait. The phishing warning at the bottom of the email is the cherry on top of this scam. This is a sneaky way to make the target feel like they can trust the email.
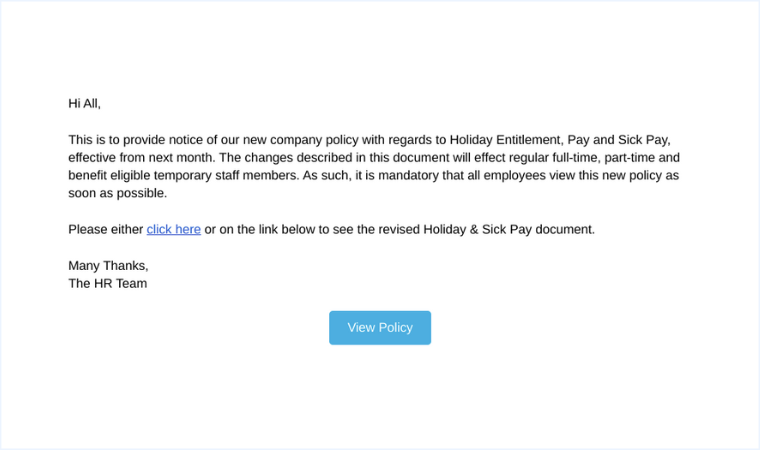
Changes to the holiday policy This phishing template piques the recipient’s interest by mentioning policy updates without giving away too much. This makes them more likely to click the call-to-action link to find out what’s changed.
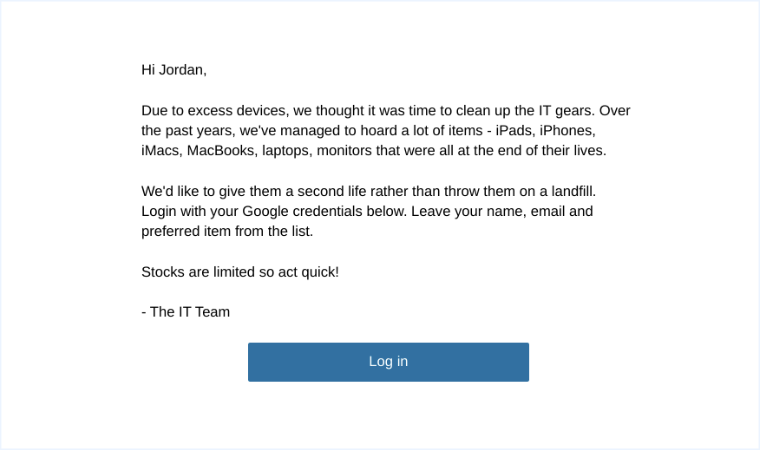
Who wouldn’t take the chance to get a laptop or tablet for free? Even more so when your trusted employer offers it to you. Even though it’s unlikely that a company would just give away a bunch of tech, it’s not unheard of for a company to give hardworking employees their old IT gear.
When you are excited and hopeful at the same time, you are more likely to fall for a “freebie” phishing attack.
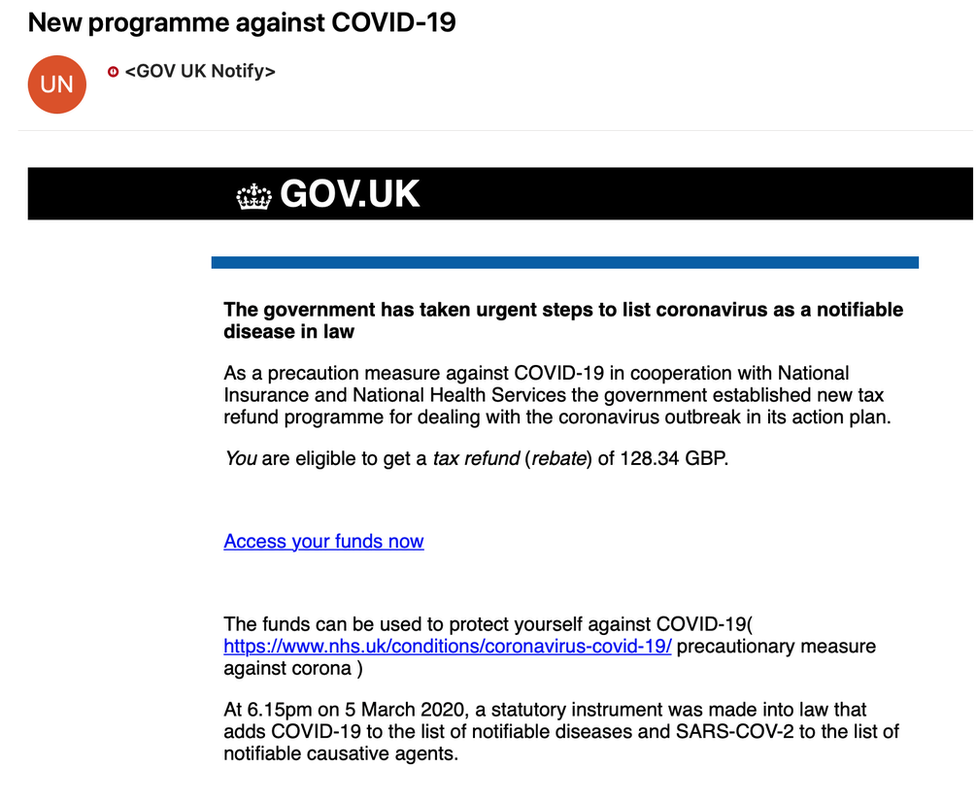
During the height of COVID-19, phishing attacks went up by 220%, with cybercriminals pretending to be the WHO, CDC, and government agencies.
During a pandemic, these attacks do a good job of taking advantage of people’s fear and willingness to follow official instructions. This makes them a dangerous trap.
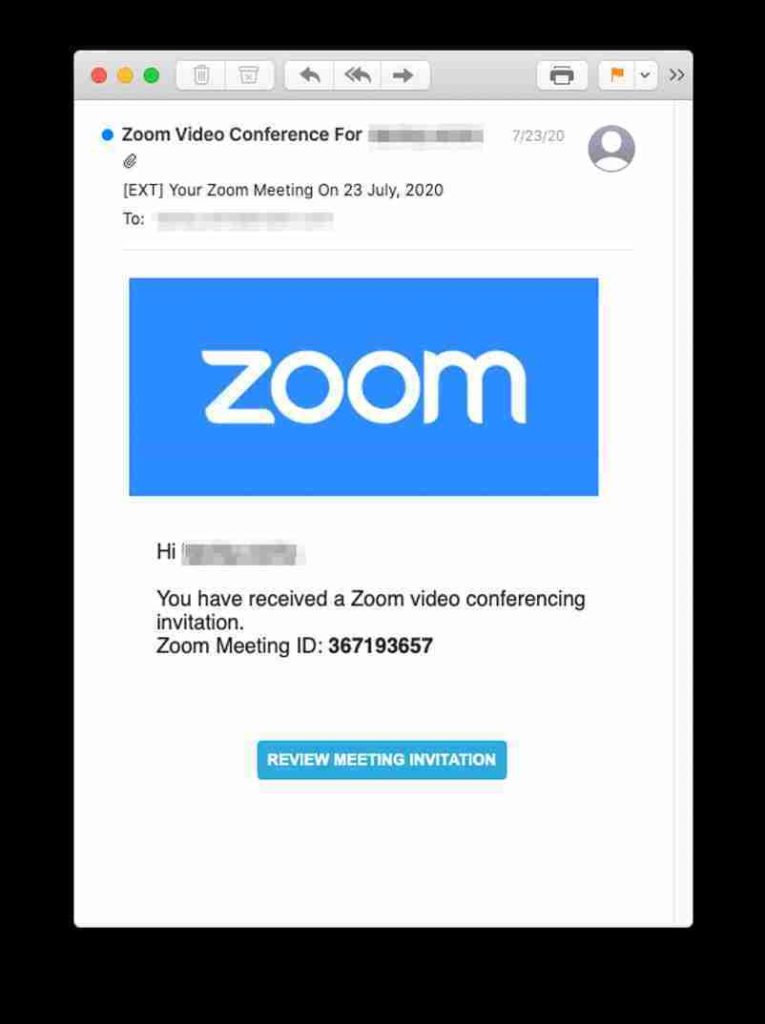
Since more people are working from home, we’ve been getting a lot of invites to virtual meetings. When people are busy, it’s easy to just click on another Zoom invite without thinking.
This phishing email also uses curiosity by leaving out the name of the host and the agenda, which makes the recipient want to click the link to find out more.
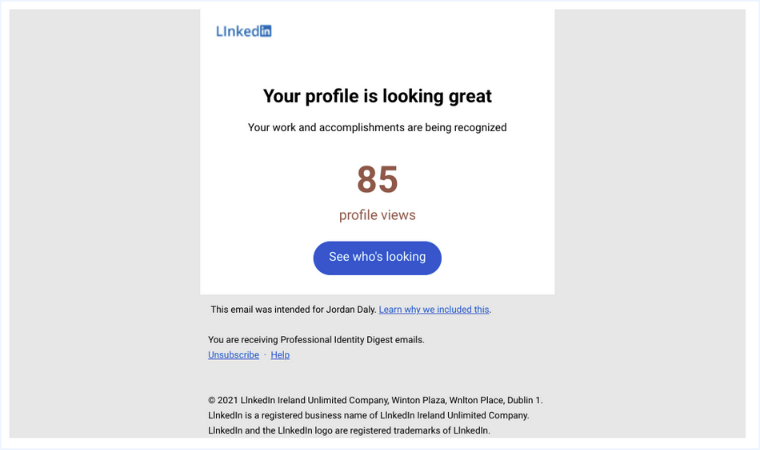
If you rarely post or apply for jobs, it can be surprising to find out that a lot of people are looking at your LinkedIn profile.
This sudden increase can be enough to make the recipient curious enough to click the “See who’s looking” link without thinking.
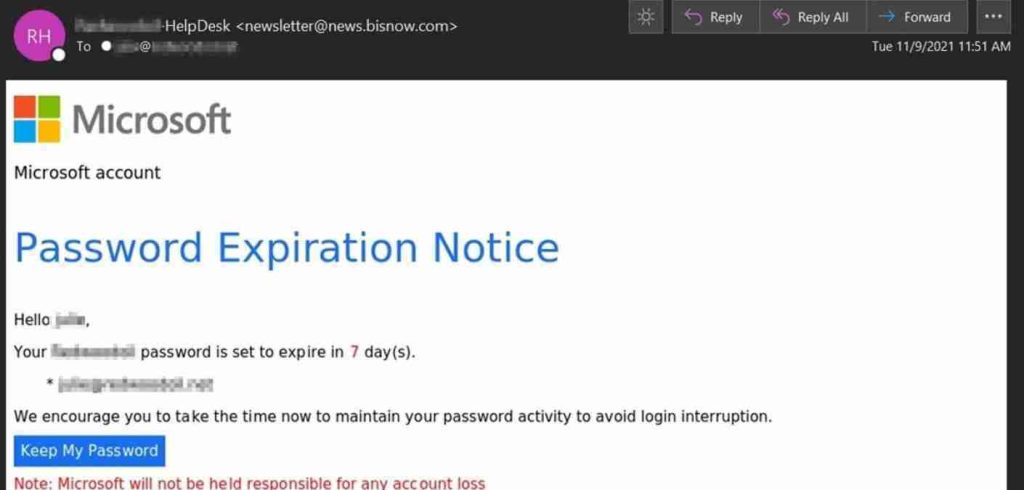
Microsoft is one of the brands that people around the world trust the most. But trust can be a very effective phishing technique, especially when the email looks like the real thing. This Microsoft scam uses fear and time pressure to get the person to act right away.
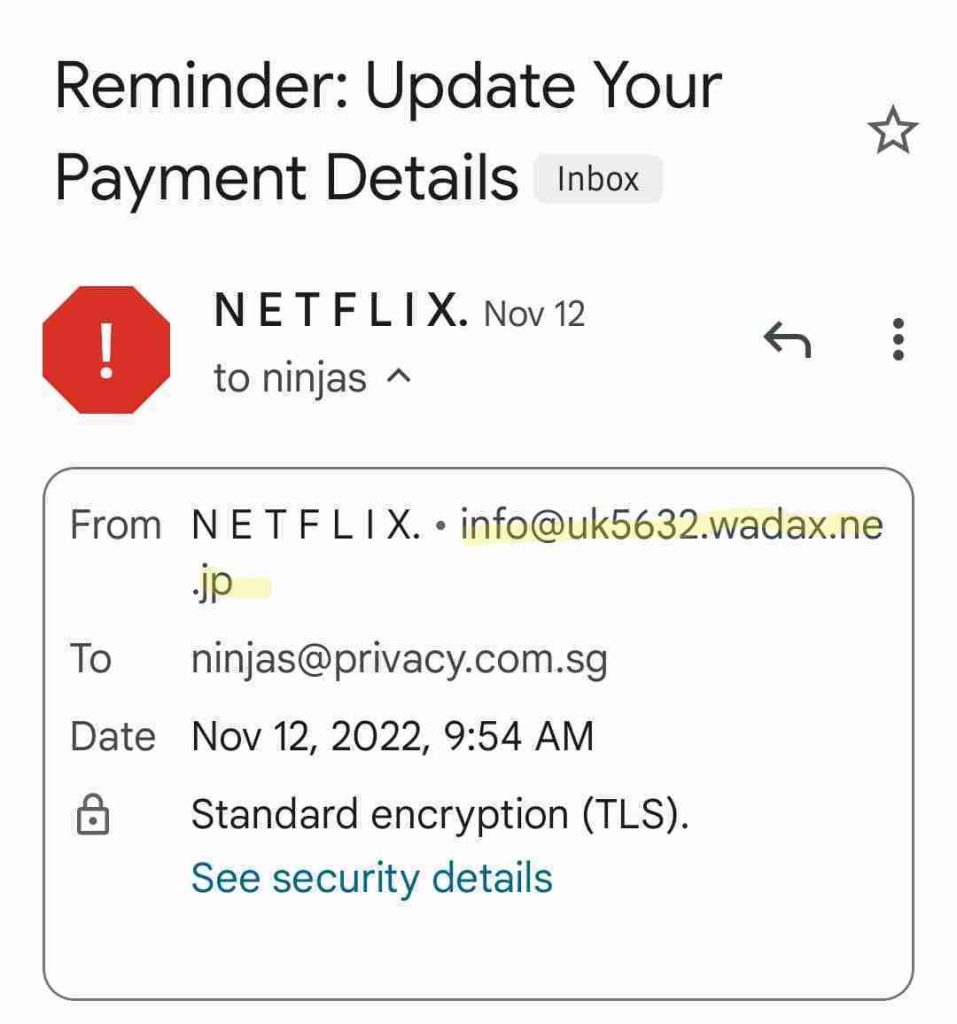
Little information is given about why the payment information is about to expire, which makes the victim more likely to click the malicious link to find out.
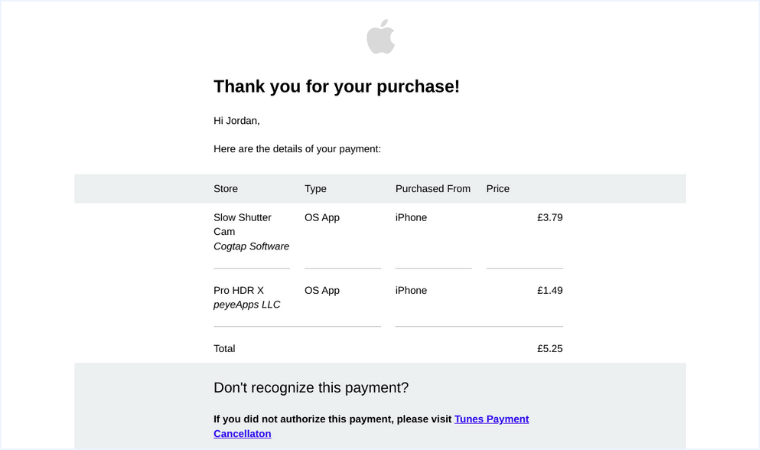
The person who gets this phishing email might be confused as to why they got an e-receipt for something they don’t remember buying. The template makes it look more real by showing what was bought and giving a “helpful” link to learn more and stop the payment.

Cybercriminals like to use the “missed package” phishing email during busy shopping times like Christmas and Black Friday. This attack has two ways to trick the target. First of all, the person might be expecting a package, which makes this email seem even more real and tempting. If no order has been made, the person who got the email might be tempted to sign in and see what’s been ordered.
Scammers often use the name of well-known business software, such as Xerox, to trick people. There’s a good chance that at least some of the people the criminal is after using the product and wouldn’t be surprised to get an email from the vendor. This phishing email about an unpaid bill uses a trusted brand and makes the target feel confused and scared.
Email phishing should be taken lightly by organisations as a successful one could mean a financial penalty from the PDPC for breaching the protection obligation. This could also mean a financial disaster for the employees themselves as the bad actor could impersonate their superiors or officers and ask them for their bank details.
This is why it is of great importance that employees, as the weakest link to the organisation’s cybersecurity, be familiar with the different forms of phishing emails so that they can identify one when they are being targeted by bad actors.
This is also where a Data Protection Officer (DPO) can help, as it is the officer responsible for the general posture of an organisation’s cybersecurity. With a DPO, organisations can ensure that policies will be set in place and employees will be well aware of the danger of email phishing.
Also Read: Breach of PDPA Singapore: 5 Things Your Organisation Should Know