KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





The Data Protection Provisions of the Personal Data Protection Act (PDPA) include 11 major obligations that organisations must follow while collecting, using, or disclosing personal data. In order to meet these obligations, organisations must design and execute policies and practises essential for the organisation to comply with the PDPA. These policies and practices should eventually be visible through the Data Protection Management Program of organisations (DPMP).
Organizations are advised to complete a Data Protection Impact Assessment (DPIA), which comes in 6 phases, in order to decide on the policies and procedures to be implemented in accordance with the these 11 obligations under the PDPA. It entails identifying, assessing, and managing personal data protection threats based on the organization’s functions, needs, and operations.
With this, understanding the DPIA’s 6 phases would position any organisation to assess whether it’s handling of personal data complies with the PDPA or data protection best practises, allowing them to structure the necessary technological or organisational steps to protect individuals from data protection risks.
Also Read: Completed DPIA Example: 7 Simple Helpful Steps To Create
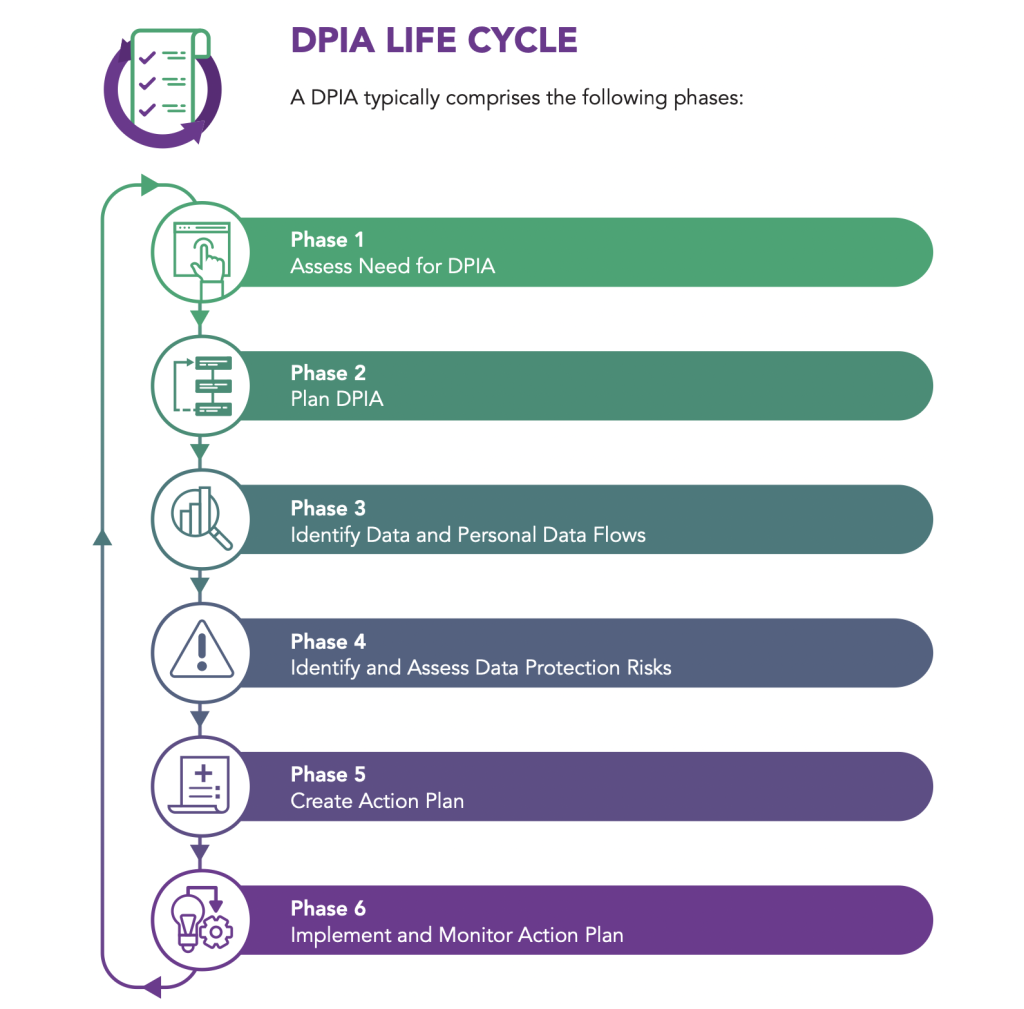
Organizations should evaluate the following elements before conducting a DPIA to decide whether a DPIA is required. To begin, the DPIA lead and DPO must assess if a DPIA is necessary by determining whether the project incorporates personal data (i.e. the collection, use, transfer, disclosure, or storage of personal data). If the project does not involve personal data, a DPIA is not necessary.
If it is found that the project will involve personal data, the threshold questions listed below can be utilised to determine the necessity for a DPIA:
If the answer is “yes” to any of these questions, a DPIA should be performed; if the answer is “no” to all of the questions, the DPIA lead should reassess when there is a change in risks connected with the project’s management of personal data.
Once the decision to conduct a DPIA has been reached, the DPIA lead should begin planning the DPIA in cooperation with the DPO. Throughout the DPIA, the DPO should also advise the DPIA lead.
The DPIA lead should cover the following areas while developing the essential activities or steps required to undertake the DPIA:
To identify and map personal data involved in the project, the DPIA lead would need to gather and examine project documents to determine how personal data is acquired, utilised, or disclosed as part of the project.
Documentation examples include the project plan, contracts with third parties, assessment reports, and system functional requirements. To ensure completeness and correctness, the DPIA lead should consult with the project team and appropriate departments or functions. On-site project inspections involving ground staff should be undertaken whenever practicable.
The DPIA lead can then:
Once the DPIA lead has recorded how personal data is handled, the DPIA lead can proceed to identify and assess personal data protection risks by:
Because projects differ in terms of type (e.g., systems, digital or manual processes) and project stage (e.g., new projects, current projects undergoing major modifications), there is no one-size-fits-all strategy for identifying, assessing, and mitigating data protection risks. DPIA leads would need to assess data protection risks while taking into account the organization’s specific circumstances. They may also need to retrace earlier steps or activities completed in earlier phases to obtain more information or clarify certain data handling processes at various stages of the project.

During this phase, the DPIA lead would need to propose how the identified data protection concerns should be addressed. The DPIA lead should also designate the action owner(s) accountable for the implementation of specific suggestions (such as technical or organisational measures), monitoring of implementation outcomes, and implementation dates in the form of an action plan. As a best practise, the action plan should include a point of contact for responding to questions about the DPIA process or implementing the action plan.
The risk assessment (in Phase 4), as well as the organization’s specific circumstances, should guide an organization’s approach to formulating an action plan (e.g. operational or resource constraints and other legal or regulatory requirements). This would have an impact on how the identified data protection risks would be addressed (e.g., removing the source of risk, spreading the risk with another party via risk financing and contracts, taking the risk based on an informed decision), as well as the timeline for implementing proposed solutions in the action plan.
Instead of implementing all of the recommendations at once, data protection risks could be prioritised depending on their likelihood and effect levels. Nonetheless, all proposals and arguments should be documented for future reference.
The DPIA lead is now ready to describe the entire DPIA process (including how the DPIA was scoped, planned, and carried out, as well as the findings and the action plan) in a DPIA report. The DPO of the organisation should assess this report to ensure that the proposed action plan is consistent with the organization’s rules and includes proper data protection practises. After the DPO has read the report, the DPIA lead should submit it to the Project Steering Committee for approval to implement the action plan.
Once accepted, the action owners can begin implementing the action plan. The project owner should additionally evaluate the action plan’s outcomes to ensure that identified personal data protection risks are addressed as intended, and personal data risks are managed responsibly.
When the risks connected with the project’s handling of personal data change, the existing DPIA (particularly the action plan outcomes) must be evaluated and amended as appropriate to meet any new gaps or risks to persons’ personal data. Here are some examples of when dangers can change:
Conducting a DPIA ensures that the policies and procedures to be implemented comply with the obligations stated in the PDPA. With this, organisations in Singapore should see to it that whenever there are changes in the policies implemented or changes in general to the functions and services of the organisation, a DPIA must be first conducted to ensure that any possible loopholes or vulnerabilities are covered and acknowledged.
Conducting a DPIA also highlights the importance of having a Data Protection Officer (DPO), as it facilitates the phases of the DPIA and ensures that the policies made responds to the needs of the organisation. Aside from the fact that it is mandated, having a DPO plays an integral part in having a healthy posture of your organisation’s cybersecurity.
In the process of conducting a DPIA, a DPO can ensure that the path forward is for faithful compliance with the PDPA and avoidance of liabilities such as a financial penalty that the PDPC can impose in case of breach.
Also Read: Data Protection Impact Assessments: 5 Elements You Should Know