KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Before we dive into the definition, let’s make this clear first: When organizations do not collect, use, and disclose personal data, the Data Protection Impact Assessments (DPIA) will not be necessary for them. But if they do, they are encouraged to complete a DPIA when determining which policies and practices to implement to comply with the PDPA.
A DPIA involves identifying, assessing, and mitigating personal data protection risks based on the functions, needs, and operations of the organization. Thus, an organization will be better equipped to determine if its use of personal data complies with the PDPA or data protection best practices and adopt suitable technical or organizational safeguards to protect individuals from data protection risks.
Data Protection Impact Assessments can be undertaken on both systems (e.g., public-facing websites, cloud storage platforms, and Customer Relationship Management (CRM) systems) and processes (e.g., undergoing a health screening and receiving the medical report, purchasing an item from an online portal, and receiving it from a courier).
A DPIA’s critical tasks include the following:
1. Identifying the personal data handled by the system or process, as well as the reasons for collecting the personal data;
2. Identifying the flow of personal data via the system or process;
3. Identifying data protection risks by an analysis of the personal data handled and its data flow in comparison to PDPA regulations or best practices in data protection;
4. Mitigating identified risks through system or process design changes or the implementation of new organizational policies; and
5. Verifying that identified risks are effectively addressed prior to the system or process being installed or put into practice.
Data protection concerns are best handled when a system or process is (i) new and in the design phase or (ii) undergoing significant changes. Adding adjustments to address data protection concerns after a process or system’s design has been finalized or deployed will almost certainly result in higher cost and effort. When to do a DPIA includes the following instances:
1. Developing a new system that will handle personal data (e.g., new website that collects personal data)
2. Developing a new process, whether automated or manual, which requires the management of personal data (e.g., receptionist collecting personal data from visitors)
3. Modification of existing systems or procedures that manage personal data (e.g., redesign of the customer registration process)
4. Organizational changes that affect the department that handles personal data (e.g., mergers and acquisitions, restructuring)
5. Collection of new forms of personal data (e.g., collecting additional information about existing customers)
Data protection impact assessments should be completed individually for each system or process that handles personal data (including the linking or sharing of personal data with other parties).
Additionally, a DPIA should be completed for several projects that share a common goal, scope, and context. For example, a retailer intending to digitize the collecting of customer data across all its locations may execute a single DPIA exercise covering the processing of consumers’ personal data across all locations.
Also Read: Guarding against common types of data breaches in Singapore

An effective DPIA should involve relevant stakeholders from across the organization’s functions (e.g., the project manager, the organization’s Data Protection Officer, and the IT department), as well as relevant external parties (e.g., subject matter experts) in order to identify, assess, and mitigate data protection risks. The DPIA lead should ideally be the Project Manager or the Organization’s Data Protection Officer (DPO).
A Data Protection Officer (DPO) oversees data protection responsibilities and ensures that organizations comply with the Personal Data Protection Act (PDPA). Every Organization’s DPO should be able to curb any instances of cyber threats and instances of data breaches as it is the officer responsible for maintaining the positive posture of an organization’s cybersecurity. Depending on the engagement agreement, the assessment may be conducted either before the organization appoints a DPO or after the appointment.
At Privacy Ninja, for instance, this assessment is performed as and when needed by our clients for new activities or a change in activities regarding personal data. This is usually discussed before clients engage our outsourced DPO service. If you are unsure about your current PDPA compliance posture, don’t hesitate to ask us about this type of assessment.
Remember that A DPO is also the person responsible for developing and enforcing the Organization’s data protection policy and may seek assistance or guidance from other DPOs through DPO networks or organizations.
The DPIA of the PDPC follows a straightforward six-step approach for reviewing data security policies and identifying concerns.
Prior to getting started, Organizations must determine the initial necessity for a DPIA. Following that, the Organization should prepare a DPIA by defining factors such as scope, frameworks, stakeholders, and timing. After designing a plan, diagram the flow of pertinent personal data associated with the audited project or policy.
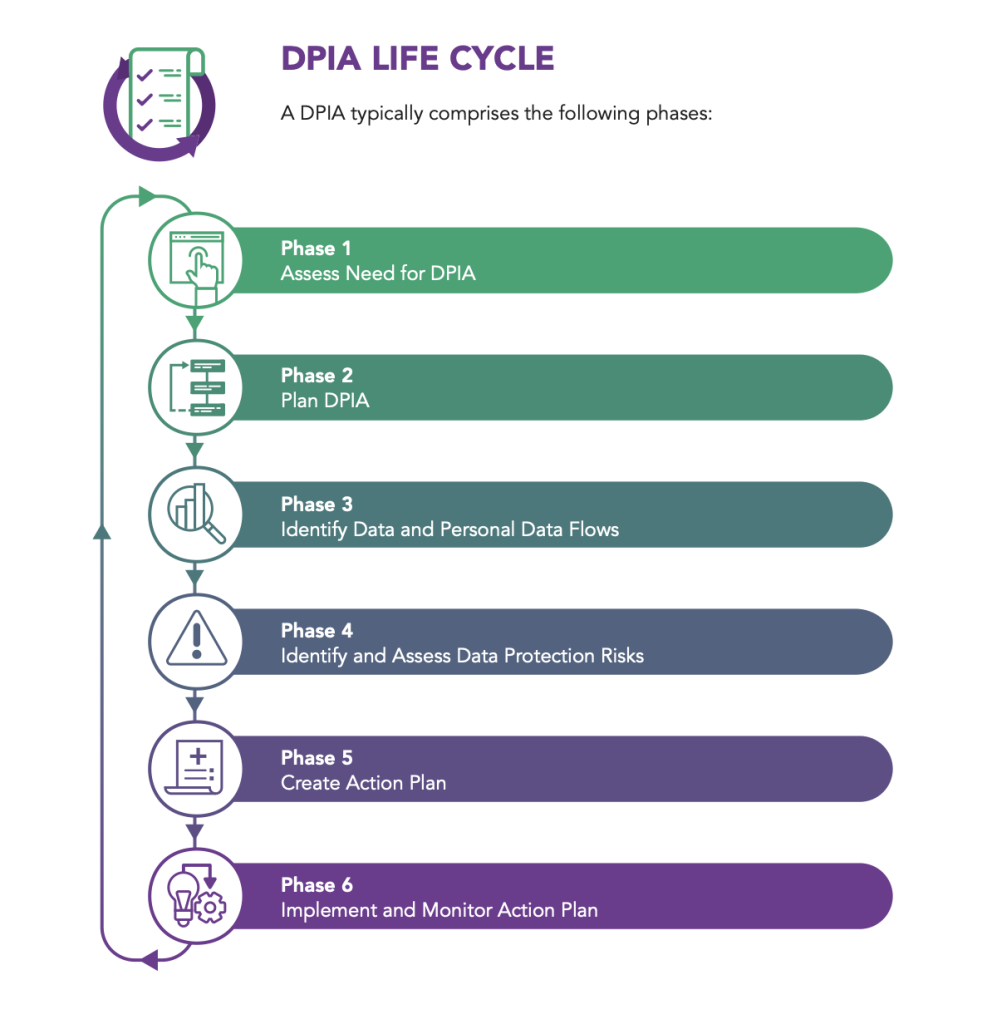
Data protection risks should then be discovered by comparing the project to PDPA criteria and conducting additional specialized evaluations of potential gaps, particularly if there are any new changes to their business structure, whether strategic, operational, or structural. Finally, businesses can use the insights gleaned to create and implement an action plan, followed by an evaluation of the results.
There is no one-size-fits-all solution for every organization, but by adhering to DPIA and tailoring data protection strategies to their specific needs, businesses can ensure PDPA compliance—while customers can rest assured that their personal data is secure.
Also Read: Completed DPIA Example: 7 Simple Helpful Steps to Create