KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






A completed DPIA example is a key component of a ‘Privacy by design’ approach to a project or other personal data processing activity. ‘Privacy by design’ is an essential tool in building trust and minimizing privacy risks.
A DPIA is a structured approach to identifying the privacy risks associated with the processing of personal data and for implementing appropriate controls to manage those risks. The process comprises the following six distinct steps and a parallel stream of consultation:
Key benefits of conducting a DPIA are:
A completed DPIA example should be done for any initiative that involves the processing of personal data or any other activity that could impact the privacy of individuals. Examples are:
A completed DPIA example should be done for new initiatives or for changes to existing systems or processes. It may also be a recommended outcome from a formal investigation into an information security incident or weakness at the organisation.
The first step in conducting a completed DPIA example is a screening process to decide whether the detailed work in the subsequent steps will be required. A completed DPIA example must be done for all research projects that may impact the privacy of individuals and/or involve the use of personal data.
Ideally, a DPIA should be undertaken in the early stages of an initiative. The earlier a completed DPIA example is done, the easier it is likely to be to address any privacy risks identified.
The organisation’s Data Protection Officer has overall accountability for ensuring that completed a DPIA example is done for high risk personal data processing initiatives.
Responsibility for ensuring that a specific completed DPIA example is done lies with the individual responsible for the initiative, such as:
The individual or team responsible for the initiative should retain the master copy of the completed DPIA example for audit purposes and to be able to demonstrate compliance with legislative requirements should a query be raised. The Data Protection Officer or Information Governance Unit may request copies of DPIAs for monitoring and reporting purposes.
There are templates available online showing how you can record your DPIA process and outcome. Understandably, it might get confusing if you are unsure what relevant questions to ask pertaining to your organisation’s data protection compliance. This is where your Data Protection Officer can step in to help you.
At Privacy Ninja, for instance, part of our outsourced Data Protection Officer Service already covers the DPIA as a “ready to use anytime” template within our DPMP documentation. We perform this together with our client on every new activity they have that collects or processes new personal data after being onboarded as our DPO-As-A-Service client.
Start to fill out the template at the beginning of any major project involving the use of personal data, or if you are making a significant change to an existing process. Integrate the final outcomes back into your project plan.
Also read: DPIA Completed Example

Explain broadly what the project aims to achieve and what type of processing it involves. You may find it helpful to refer to or link to other documents, such as a project proposal. Summarize why you identified the need for a DPIA.
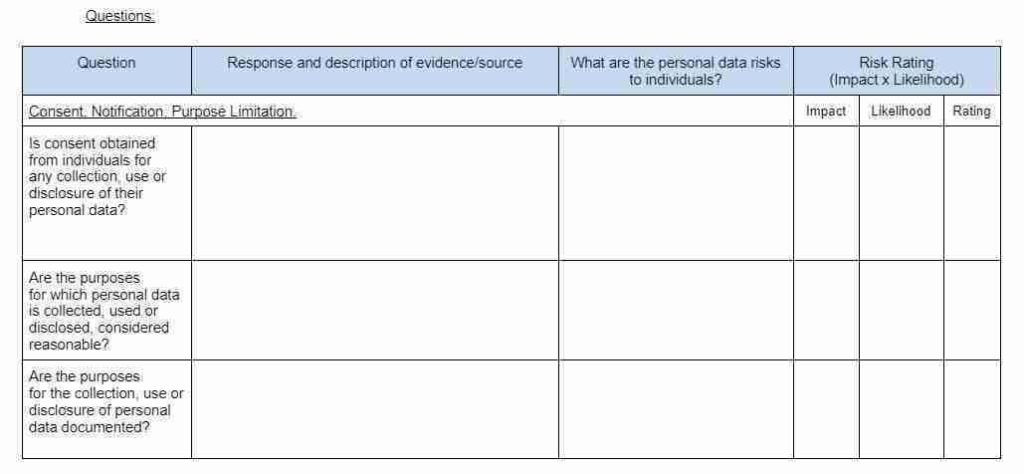
Describe the nature of the process: How will you collect, use, store and delete personal data? What is the source of the data? Will you be sharing data with anyone? You might find it useful to refer to a flow diagram or another way of describing data flows. What types of processing identified as “likely high risk” are involved?
Describe the scope of the process: what is the nature of the data, and does it include special category or criminal offence data? How much data will you be collecting and using? How often? How long will you keep it? How many individuals are affected? What geographical area does it cover?
Describe the context of the process: What is the nature of your relationship with the individuals? How much control will they have? Would they expect you to use their data in this way? Do they include children or other vulnerable groups? Are there prior concerns over this type of processing or security flaws?
Is it novel in any way? What is the current state of technology in this area? Are there any current issues of public concern that you should factor in? Are you signed up to any approved code of conduct or certification scheme (once any have been approved)?
Describe the purposes of the process: What do you want to achieve? What is the intended effect on individuals? What are the benefits of the processing for you, and more broadly?
Consider how to consult with relevant stakeholders: Describe when and how you will seek individuals’ views – or justify why it’s not appropriate to do so. Who else do you need to involve within your organisation? Do you need to ask your processors to assist? Do you plan to consult information security experts, or any other experts?
Identify controls to mitigate the risks and record them in the DPIA template. The aim is to identify sufficient controls to eliminate each of the risks identified in Step Three, or to reduce them to a level which is acceptable to the organisation. For some identified risks, no controls may be required because the likelihood is so low and/or the impact so small that the risks are acceptable to the organisation.
Controls may take many forms, such as:
Once a control is identified, the expected result of its implementation should be recorded i.e. whether it is likely to:
Proposed controls should then be approved by an appropriate individual. Normally this should be the information asset owner or their nominated delagate, but it could also be:
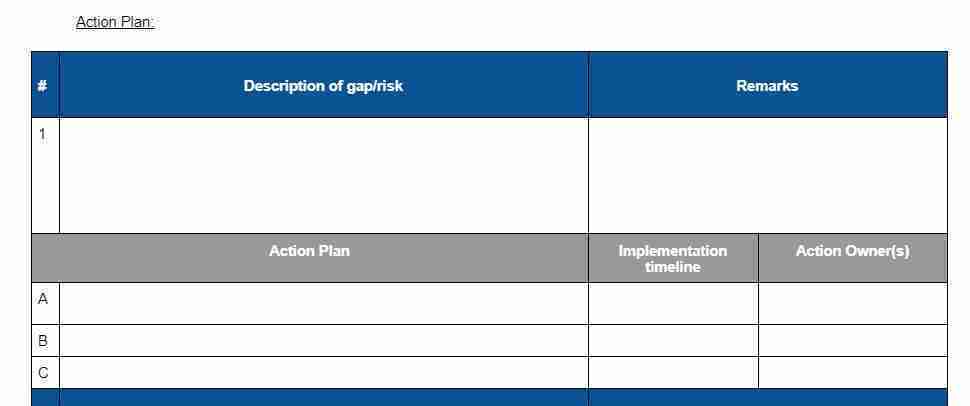
Allocate the controls to appropriate individuals and record an agreed deadline for implementation.
In the case of a company initiative, the implementation of many of the controls will fall within the scope of the initiative and should be managed in the same way as any other project task. However, the implementation of some controls will be beyond the scope of the project (such as a change to the organisation’s policy) so related tasks should be assigned through the organisation’s normal management processes and added to the list of project dependencies.
Where initiatives are being run informally, or as ‘business as usual’ activities, the organisation’s normal management processes should be used to identify who will implement the controls and agree an appropriate deadline. In all cases, a named individual and deadline for completion should be assigned and recorded.
In the absence of formal project management documentation, the DPIA should be used to record when controls are implemented.
After the controls have been implemented, reassess the risks and record the outcome in the DPIA template. The risks then need to be accepted by an appropriate individual. Normally this should be the information asset owner or their nominated delegate, but it could also be:
The individual who signs off the risks should have a clear understanding of the initiative, particularly the privacy risks and how the controls address them. If any risk has not been reduced to an acceptable level after implementation of the controls identified in Step Four, additional controls will need to be identified and Step Five and Step Six will need to be repeated.
Consultation serves many purposes throughout the DPIA process, such as:
Key stakeholders are likely to include:
In cases where the impact of a risk identified at Step Three is assessed to be either severe or major and likelihood is assessed to be either likely or very likely, the organisation’s Data Protection Officer must be consulted. If any risk remains at this level after the implementation of controls, the University may be required to consult the Information Commissioner’s Office.
Also read: What you need to know about appointing a Data Protection Officer in Singapore