KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Have you ever found it difficult to determine and manage data information? One of the main challenges faced by companies is managing information adequately. This time we’ll discuss the solution to this problem in managing data information using the data life cycle.
Most data life cycle professionals would acknowledge that there is a data life cycle, but it is fair to say that there is no common understanding of what it is. If you Google “Data Life Cycle,” you will not find anything that clearly describes it. But, if data life cycle professionals know that there really is a data life cycle, then it is incumbent on us to try to define it.
This is one attempt to describe the Data Life Cycle. It takes the position that a life cycle consists of phases, and each phase has its own characteristics. Einstein, when he was a teenager, tried to think what it would be like to ride a beam of light. There is no chance that we can emulate Einstein, but perhaps we can put his idea to use. What would happen if we could ride on a piece of data as it moved through the enterprise? What new experiences would the piece of data have? What phases would it pass, though?
What do you think when you hear that word? or you might have a view about data life cycle?
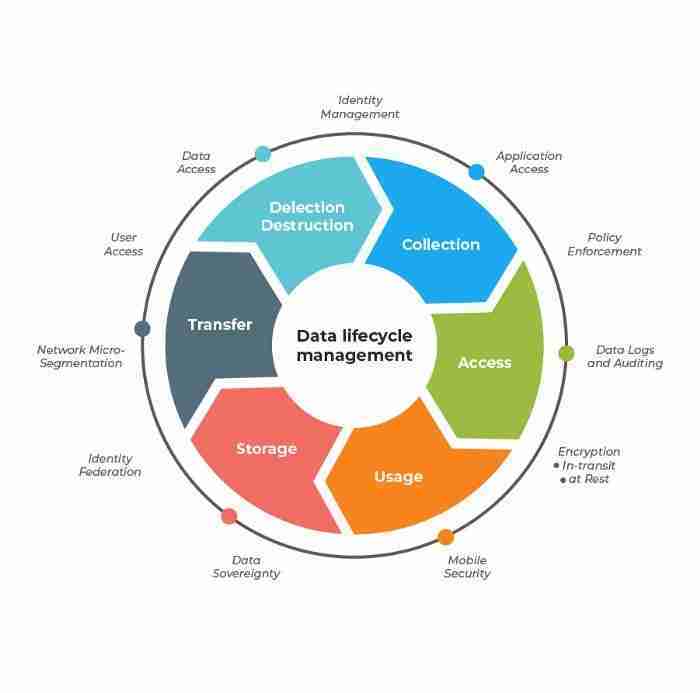
Data Life cycle itself refers to a definition and through structuring the steps that are followed by information within the company to maximize its useful life.
So in this data life cycle, Will require the use of resources that have been offered by information technology for automatic processing. Through them, it is possible to collect data for analysis and trace it to the point of storage or cleaning.
What do you get when you implement data life cycle? What you need to know is that when a Singaporean company implements data life cycle and ensures good handling of the information they produce in their daily operations they have several advantages, which include:
Also read: Digital Transformation – Do Or Die in 2020
The first experience that an item of data must have is to pass within the firewalls of the enterprise. This is Data Capture, which can be defined as the act of creating data values that do not yet exist and have never existed within the enterprise.
There are three main ways that data can be captured, and these are very important:
There may well be other ways, but the three identified above have significant Data Governance challenges. For instance, Data Acquisition often involves contracts that govern how the enterprise is allowed to use the data it obtains in this way.
Once data has been captured, it usually encounters Data Maintenance. This can be defined as the supplying of data to points at which Data Synthesis and Data Usage occur, ideally in a form that is best suited for these purposes.
We will deal with Data Synthesis and Data Usage in a moment. Data Maintenance is about processing the data without deriving any value from it for the enterprise. It often involves tasks such as movement, integration, cleansing, enrichment, changed data capture, and familiar extract-transform-load processes.
Data Maintenance focuses on a broad range of data life cycle activities. Because of this, Data Governance faces many challenges in this area. Perhaps one of the most important is rationalizing how data is supplied to the endpoints for Data Synthesis and Data Usage, e.g., preventing the proliferation of point-to-point transfers.
This is comparatively new and perhaps still not a very common phase in the Data Life Cycle. It can be defined as the creation of data values via inductive logic, using other data as input.
It is the arena of analytics that uses modeling, such as is found in risk modeling, actuarial modeling, and modeling for investment decisions. Derivation by deductive logic is not part of this – that occurs in Data Maintenance. An example of deductive logic is Net Sales = Gross Sales – Taxes. If I know Gross Sales and Taxes, and I know the simple equation just outlined, then I can calculate Net Sales.
Inductive logic requires some expert experience, judgment, and opinion as a part of the logic, e.g., the way in which credit scores are created.
So far, we have seen how our single data value has entered the enterprise via Data Capture and has been moved around the enterprise, perhaps being transformed and enriched in Data Maintenance and possibly being input to Data Synthesis. Next, it reaches a point where it is used in support of the enterprise. This is Data Usage, which can be defined as the application of data as information to tasks that the enterprise needs to run and manage itself.
These would normally be tasks outside the data life cycle itself. However, data is becoming more central to business models in many enterprises. For instance, data may itself be a product or service (or part of a product or service) that the enterprise offers. This, too, is Data Usage, even if it is part of the Data Life Cycle because it is part of the enterprise’s business model.
Data usage has special Data Governance challenges. One of them is whether it is legal to use the data in the ways that business people want. This is referred to as “permitted use of data.” There may be regulatory or contractual constraints on how data may actually be used, and part of the role of Data Governance is to ensure that these constraints are observed.
In being used, it is possible that our single data value may be sent outside of the enterprise. This is Data Publication, which can be defined as the sending of data to a location outside of the enterprise.
An example would be a brokerage that sends monthly statements to its clients. Once data has been sent outside the enterprise, it is de facto impossible to recall it. Data values that are wrong cannot be corrected as they are beyond the reach of the enterprise. Data Governance may be needed to assist in deciding how incorrect data that has been sent out of the enterprise will be dealt with. Unhappily, data breaches also fall under Data Publication.
Our single data value may experience many rounds of usage and publication, but eventually, the end of its life begins to loom large. The first part of this is to archive the data value. Data Archival is the copying of data to an environment where it is stored in case it is needed again in an active production environment and the removal of this data from all active production environments.
A data archive is simply a place where data is stored but where no maintenance, usage, or publication occurs. If necessary, the data can be restored to an environment where one or more of these occur.
We now come to the actual end of life of our single data value. Data Purging is the removal of every copy of a data item from the enterprise.
Ideally, this will be done from an archive. A Data Governance challenge in this phase of the data life cycle is proving that the purge has actually been done properly.

The terms we have used may be disputed. “Life Cycle” is not really accurate because data does not reproduce or recycle itself, which happens in real life cycles. “Data Life History” might be closer to the truth, but it is not a familiar term. “Life History” describes the phases of growth in an organism like a butterfly, but the data is different. Therefore, “Data Life Cycle” might as well be used.
What has been described here are phases with logical dependencies, not the actual data flows. Data flows may go round and round through these phases, e.g., from Data Synthesis back to Data Maintenance and then returning to Data Synthesis and so on in more cycles. A description of these flows is quite different from the Data Life Cycle, though design should be informed by the Data Life Cycle.
Also read: Free Privacy Policy Compliance Review