KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!



Directory listing is a web server function that displays the directory contents when there is no index file in a specific website directory. It is dangerous to leave this function turned on for the web server because it leads to information disclosure.
For example, when a user requests www.acunetix.com without specifying a file (such as index.html, index.php, or default.asp), the web server processes this request, returns the index file for that directory, and the browser displays the website. However, if the index file did not exist and if directory listing was turned on, the web server would return the contents of the directory instead.
Many webmasters follow security through obscurity. They assume that if there are no links to files in a directory, nobody can access them. This is not true. Many web vulnerability scanners such as Acunetix easily discover such directories and all files if directory listing is turned on. This means that black hat hackers can also find such files easily. This is why directory listing should never be turned on, especially in the case of dynamic websites and web applications, including WordPress sites.
Even if directory listing is disabled on a web server, attackers might discover and exploit web server vulnerabilities that let them perform directory browsing. For example, there was an old Apache Tomcat vulnerability, where improper handling of null bytes (%00) and backslash (\) made it prone to directory listing attacks.
Attackers might also discover directory indexes using cached or historical data contained in online databases. For example, Google’s cache database might contain historical data for a target, which previously had directory listing enabled. Such data allows the attacker to gain the information needed without having to exploit vulnerabilities.
A user makes a website request to www.vulnweb.com/admin/. The response from the server includes the directory content of the directory admin, as seen in the below screenshot.
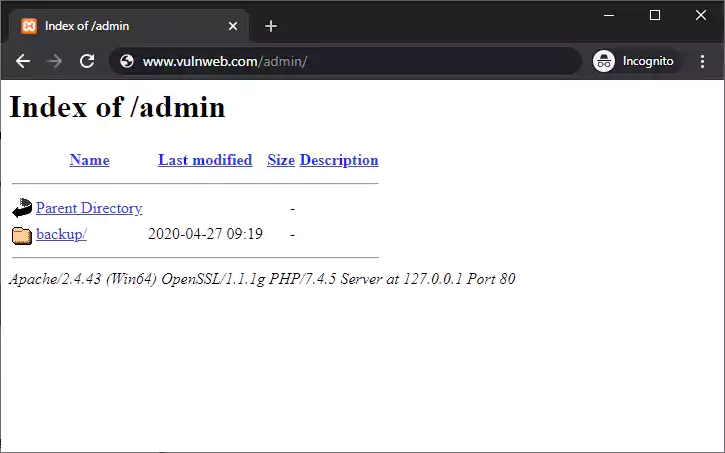
From the above directory listing, you can see that in the admin directory there is a sub-directory called backup, which might include enough information for an attacker to craft an attack.
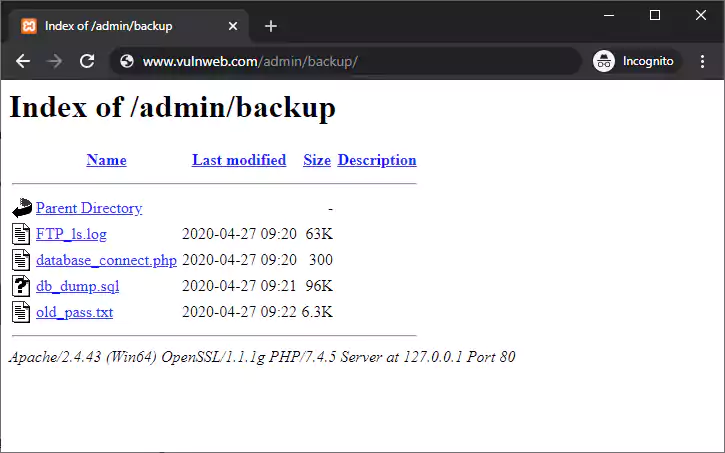
The attacker can display the whole list of files in the backup directory. This directory includes sensitive files such as password files, database files, FTP logs, and PHP scripts. It is obvious that this information was not intended for public view.
Misconfiguration of the web server has led to file list disclosure and the data is publicly available. Moreover, files like these, such as FTP logs, might contain other sensitive information such as usernames, IP addresses, and the complete directory structure of the web hosting operating system.
Also read: What Is Governance Structure: Fundamentals for Gov’t Success
To disable directory listing, you must change your web server configuration. Here is how you can do it for the most popular web servers:
You can disable directory listing by setting the Options directive in the Apache httpd.conf file by adding the following line:
<Directory /your/website/directory>Options -Indexes</Directory>
You can also add this directive in your .htaccess files but make sure to turn off directory listing for your entire site, not just for selected directories.
Directory indexing is disabled by default in nginx so you do not need to configure anything.
However, if it was turned on before, you can turn it off by opening the nginx.conf configuration file and changing autoindex on to autoindex off.
Also read: 4 Easy Steps To Create Privacy Management Plan For Business