KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





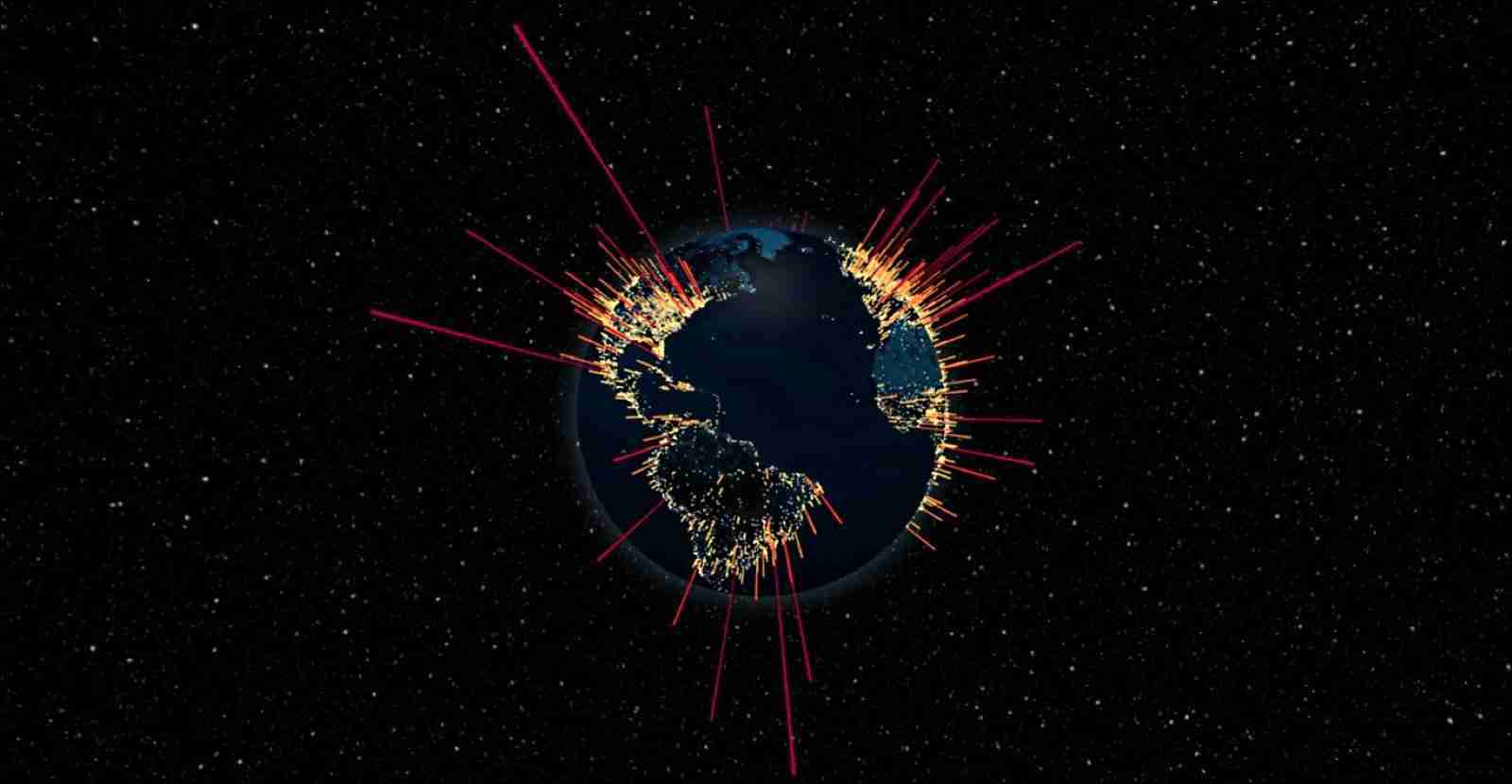
The FBI warns US companies that thousands of organizations around the world, from various industry sectors, have been threatened with DDoS attacks within six days unless they pay a Bitcoin ransom.
The threat actors behind this large and ongoing ransom DDoS (RDDoS or RDoS) campaign that started on August 12, 20220, are posing as well-known hacking groups such as Fancy Bear, Cozy Bear, Lazarus Group, and Armada Collective in the ransom notes delivered to the targeted companies.
In the MU-000132-DD Flash Alert seen by BleepingComputer and distributed to US companies last week, the US domestic intelligence service also adds that the criminal gang is currently targeting organizations from the retail, financial, travel, and e-commerce industry verticals.
While the FBI didn’t give any hints on the regions targeted, Israelian cyber-security firm Radware who also issued an alert about these attacks earlier today says that it received attack reports from entities in North America, APAC (Asia-Pacific ), and EMEA (Europe, the Middle East, and Africa).
The ransoms asked by the group range between 10 BTC (roughly $113,000) and 20 BTC (about $226,000) to be paid to unique Bitcoin addresses for each victim, according to Radware.
The ransom notes also say that the DDoS attacks will go up to 2Tbps if the companies fail to come up with the money and pay the ransoms, with the ransom fee to grow in increments of 10 BTC for each missed deadline once the attacks start.
US cloud security firm Akamai said in a separate report that the ransom letters are similar to those sent during an RDoS campaign from November 2019, as well as to one from 2017 per the FBI’s alert.
If you report this to media and try to get some free publicity by using our name, instead of paying, attack will start permanently and will last for a long time. (sic)” – Armada Collective
“…your websites and other connected services will be unavailable for everyone. Please also note that this will severely damage your reputation among your customers. […] We will completely destroy your reputation and make sure your services will remain offline until you pay. (sic)” – Fancy Bear
The FBI says that multiple organizations hit by this RDoS campaign have reported small-sized demo attacks after receiving the ransom notes but, in most cases, they were not followed by DDoS activity after the six-day deadline expired.
Despite this, several organizations did report having their operations impacted by attacks that couldn’t be mitigated.
Akamai said that these demo “attacks peak at almost 200 Gb/sec, utilizing ARMS, DNS Flood, GRE Protocol Flood, SNMP Flood, SYN Flood, and WSDiscovery Flood attacks as their main vectors.”
Also read: 10 Tips For Drafting Key Terms In A Service Agreement
The FBI recommended US companies that received such ransom notes from the criminal gang behind this ongoing RDoS campaign not to pay the criminals’ ransom.
Giving in to their demands will directly fund their future operations as the FBI said and will also encourage them to target other potential victims.
Targeted companies are also urged to report any RDoS attacks affecting them to their local FBI field office to provide information that could help prevent attacks against other targets, as well as to potentially identify and hold the attackers accountable for their actions.
The FBI recommends US organizations to use DDoS mitigation services to identify and block such attacks automatically before their networks are affected.
They are also advised to work with their Internet service provider (ISP) to make it easier to monitor network traffic and block it in the event of an ongoing DDoS attack.
Also read: How To Make A PDPC Complaint: With Its Importance And Impact