KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft is tracking an ongoing Office 365 phishing campaign that makes use of several methods to evade automated analysis in attacks against enterprise targets.
“We’re tracking an active credential phishing attack targeting enterprises that uses multiple sophisticated methods for defense evasion and social engineering,” Microsoft said.
“The campaign uses timely lures relevant to remote work, like password updates, conferencing info, helpdesk tickets, etc.”
One of the evasion tactics utilized in this credential theft attack is the use of redirector URLs with the capability to detect incoming connections from sandbox environments commonly used by security researchers to gain more info about the attack.
Also Read: Limiting Location Data Exposure: 8 Best Practices
Once such a connection is detected, the redirector will switch from sending the potential victims to a phishing landing page to redirecting any automated analysis attempts to legitimate sites.
This allows the phishers to make sure that their phishing pages will only be visited by real users, thus drastically lowering the chance of getting their attacks blocked and increasing the odds of real people being lured to their phishing sites.
The phishing emails used in this campaign are also heavily obfuscated to make sure that secure email gateways will not be able to detect the malicious messages and automatically block them before they land in the targets’ inboxes.
.jpg)
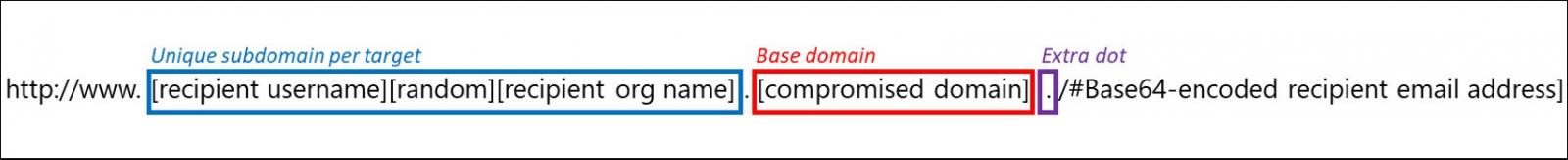
This campaign is also generating custom subdomains to use with redirector sites for each of the targets as a method to make the phishing URLs more believable in the eyes of the targets and thus boost the attacks’ success rate.
These subdomains are created using several formats but they will almost always contain the target’s username and their organization’s domain name.
“This unique subdomain is added to a set of base domains, typically compromised sites,” Microsoft explained. “Notably, the phishing URLs have an extra dot after the TLD, followed by the Base64-encoded email address of the recipient.”
“The unique subdomains also mean huge volumes of phishing URLs in this campaign, an attempt at evading detection.”
Display name patterns like “Password Update”, “Exchange protection”, “Helpdesk-#”, “SharePoint”, and “Projects_communications” are also used as a social engineering lure to increase the likeliness that the targets will give in and click the phishing URLs embedded within each email.
Earlier this month another Office 365 phishing campaign was detected while inverting images used as backgrounds for landing pages to avoid getting flagged as malicious by web crawling engines used to spot phishing sites.
The phishing kit designed to use that novel tactic automatically reverts the backgrounds using Cascading Style Sheets (CSS) to revert to the original backgrounds of the Office 365 login pages they’re trying to mimic.
Also Read: 10 Practical Benefits of Managed IT Services
This way, phishing targets that get redirected to one of these landing pages will see the original background instead of the inverted image backgrounds that the web crawlers get served with.
Previous phishing campaigns targeting Office 365 users also used innovative tactics such as abusing Google Ads to circumvent secure email gateways, using cloud services such as Google Cloud Services, Microsoft Azure, Microsoft Dynamics, and IBM Cloud to host phishing landing pages, as well as testing the stolen login in real-time.