KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft warned customers today that it will finally disable basic authentication in random tenants worldwide to improve Exchange Online security starting October 1, 2022.
Today’s announcement follows multiple reminders and warnings the company has issued over the last three years, the first published in September 2019.
The company again asked customers to toggle off basic auth in September 2021 and May 2022 after seeing that many of them were yet to move their clients and apps to Modern Authentication.
“Since our first announcement nearly three years ago, we’ve seen millions of users move away from basic auth, and we’ve disabled it in millions of tenants to proactively protect them. We’re not done yet though, and unfortunately usage isn’t yet at zero. Despite that, we will start to turn off basic auth for several protocols for tenants not previously disabled,” the Exchange Team said today.
Also Read: The Financial Cost of Ransomware Attack
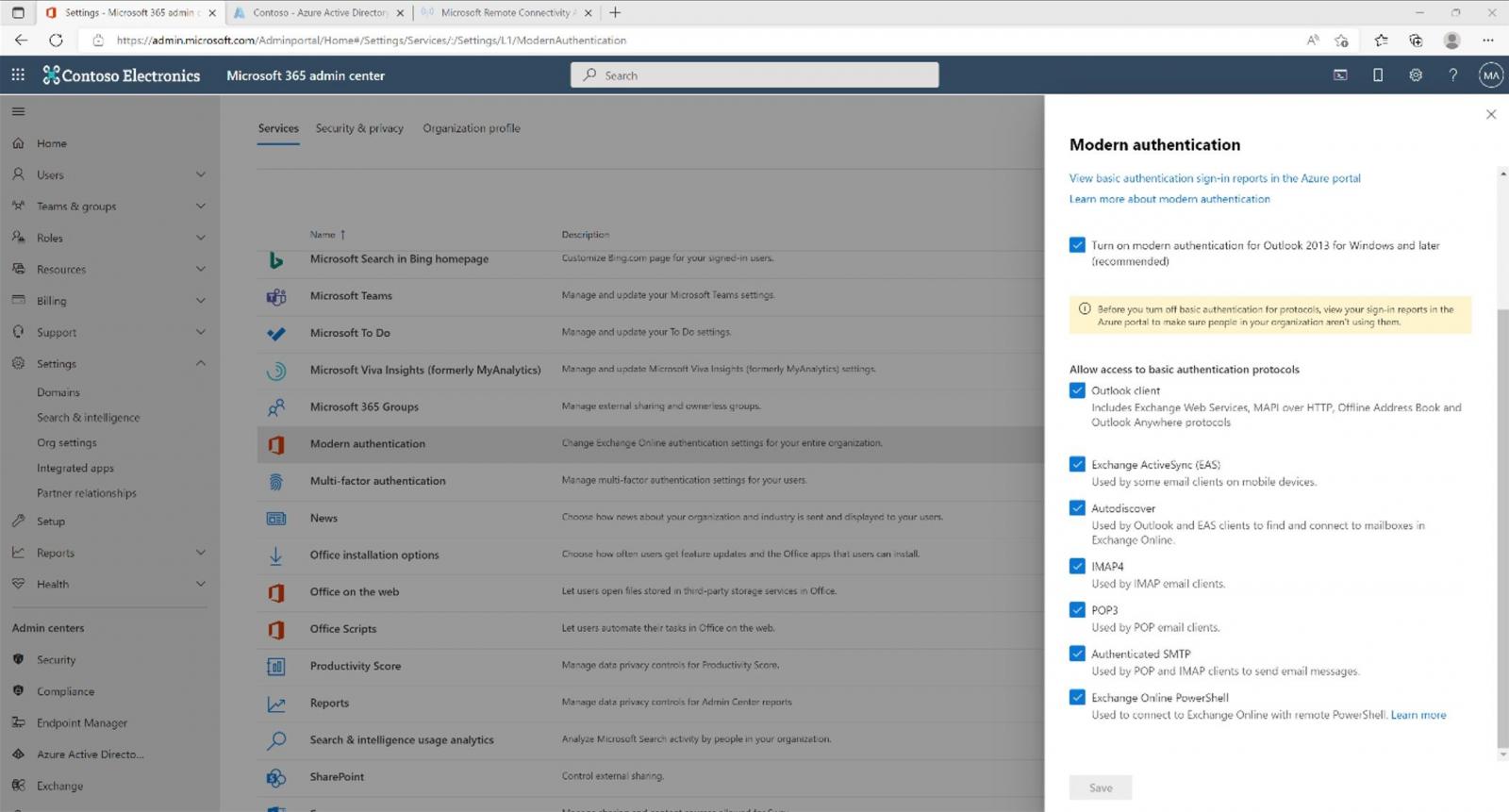
“Starting October 1st, we will start to randomly select tenants and disable basic authentication access for MAPI, RPC, Offline Address Book (OAB), Exchange Web Services (EWS), POP, IMAP, Exchange ActiveSync (EAS), and Remote PowerShell.”
Redmond says a message announcing this move will be posted to the Windows Message Center seven days before the rollout begins. Each tenant will be notified via the Service Health Dashboard notifications when basic auth is disabled.
On tenants where this authentication scheme will be disabled, customers will still be able to re-enable it once per protocol using the self-service diagnostic until the end of December 2022. However, the protocols “will be disabled for basic auth use permanently” during the first week of January 2023, with no way of using basic auth again.
Until now, Microsoft says it has already disabled basic auth in millions of tenants that weren’t using it and is also toggling off unused protocols within tenants still using it to protect them from attacks exploiting this insecure auth scheme.
“This effort has taken three years from initial communication until now, and even that has not been enough time to ensure that all customers know about this change and take all necessary steps. IT and change can be hard, and the pandemic changed priorities for many of us, but everyone wants the same thing: better security for their users and data,” Microsoft added.
Also Read: Lessons from PDPC Incident and Undertaking: August 2021 Cases
Basic authentication (aka legacy authentication or proxy authentication) is an HTTP-based auth scheme applications use for sending credentials in plain text to servers, endpoints, or various online services.
Unfortunately, this allows threat actors to steal credentials in man-in-the-middle attacks over TLS or guess them in password spray attacks. They can steal clear text credentials from apps using basic auth via several tactics, including social engineering and info-stealing malware.
Modern Authentication (an umbrella term for multiple authentication and authorization methods) uses OAuth access tokens that can’t be re-used to authenticate on other resources besides the ones they were issued for.
To make things even worse, basic auth makes it quite complicated to enable multi-factor authentication (MFA), which means that it will often not be used at all. Toggling on Modern Auth makes enabling MFA much less complicated, thus allowing for better Exchange Online security.
While there are many reasons behind switching to Modern Auth in Exchange Online, a Guardicore report added another to the list in September 2021.
It further highlighted the importance of this move, showing how hundreds of thousands of Windows domain credentials were leaked in plain text to external domains by misconfigured email clients using basic auth.
“Our own research found that more than 99 percent of password spray attacks leverage the presence of Basic Authentication,” Microsoft 365 General Manager Seth Patton added.
“The same study found that over 97 percent of credential stuffing attacks also use legacy authentication. Customers that have disabled Basic Authentication have experienced 67 percent fewer compromises than those who still use it.”
You can find more info on preparing for October’s forced basic authentication deprecation and the best way to disable basic auth beforehand in the blog post The Exchange Team published today.