KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft warned customers today to patch two Active Directory domain service privilege escalation security flaws that, when combined, allow attackers to easily takeover Windows domains.
The company released security updates to address the two security vulnerabilities (tracked as CVE-2021-42287 and CVE-2021-42278 and reported by Andrew Bartlett of Catalyst IT) during the November 2021 Patch Tuesday.
Redmond’s warning to immediately patch the two bugs — both allowing attackers to impersonate domain controllers — comes after a proof-of-concept (PoC) tool that can leverage these vulnerabilities was shared on Twitter and GitHub on December 11.
Also Read: The necessity of a data protection plan for businesses in Singapore
“When combining these two vulnerabilities, an attacker can create a straightforward path to a Domain Admin user in an Active Directory environment that hasn’t applied these new updates,” Microsoft explains in an advisory published today.
“This escalation attack allows attackers to easily elevate their privilege to that of a Domain Admin once they compromise a regular user in the domain.
“As always, we strongly advise deploying the latest patches on the domain controllers as soon as possible.”
Windows admins are urged to update devices exposed to attacks using the steps and information detailed in the following knowledgebase articles: KB5008102, KB5008380, KB5008602.
Researchers who tested the PoC stated that they were able to easily use the tool to escalate privileges from standard Active Directory user to a Domain Admin in default configurations.
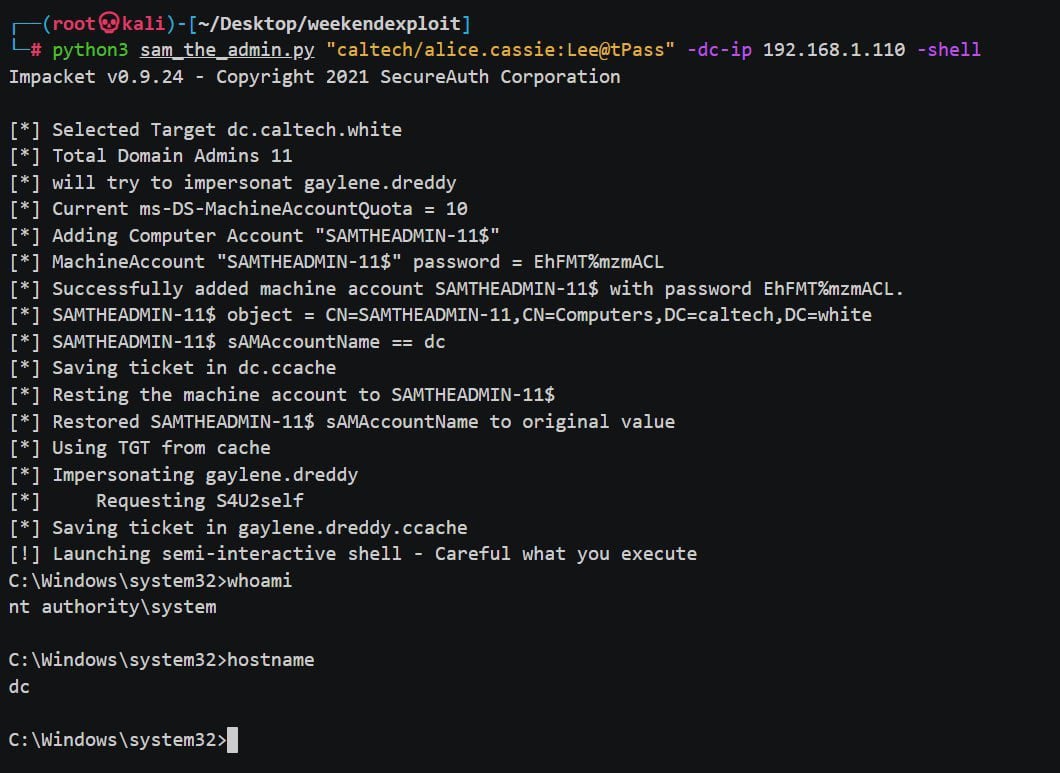
Microsoft has also shared detailed guidance on detecting signs of exploitation in your environment and identifying potentially compromised servers using Defender for Identity advanced hunting query that looks for abnormal device name changes.
Also Read: Tools for penetration testing to choose from
The step-by-step guide requires defenders to:
IdentityDirectoryEvents | where Timestamp > ago(1d) | where ActionType == "SAM Account Name changed" | extend FROMSAM = parse_json(AdditionalFields)['FROM SAM Account Name'] | extend TOSAM = parse_json(AdditionalFields)['TO SAM Account Name'] | where (FROMSAM has "$" and TOSAM !has "$") or TOSAM in ("DC1", "DC2", "DC3", "DC4") // DC Names in the org | project Timestamp, Application, ActionType, TargetDeviceName, FROMSAM, TOSAM, ReportId, AdditionalFields“Our research team continues its effort in creating more ways to detect these vulnerabilities, either with queries or out-of-the-box detections,” Microsoft added.