KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






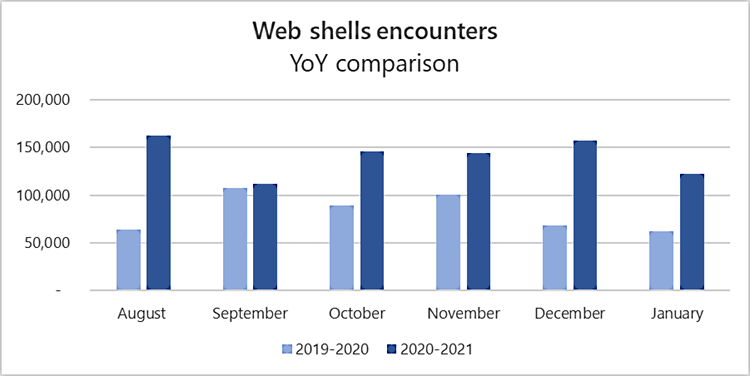
Microsoft says that the number of monthly web shell attacks has almost doubled since last year, with an average of 140,000 such malicious tools being found on compromised servers every month.
Web shells are tools (scripts or programs) that threat actors deploy on hacked servers to gain and/or maintain access, as well as to remotely execute arbitrary code or commands, to move laterally within the network, or to deliver additional malicious payloads.
They can be deployed in a large variety of forms, from app plugins and PHP or ASP code snippets injected within web apps to programs designed to provide web shell features and Perl, Python, Ruby, and Unix shell scripts.
“The latest Microsoft 365 Defender data shows that this trend not only continued, it accelerated: every month from August 2020 to January 2021, we registered an average of 140,000 encounters of these threats on servers,” Microsoft said.
In comparison, the Microsoft Defender Advanced Threat Protection (ATP) team said in a report published last year that it was detecting an average of 77,000 web shells each month, based on data collected from roughly 46,000 distinct devices.
Also Read: Data Centre Regulations Singapore: Does It Help To Progress?
Microsoft also provided some tips on how to harden servers against attacks attempting to download and install a web shell.
The list of preventive measures that should prevent web shell attacks include:
The U.S. National Security Agency (NSA) also warned of threat actors escalating their attacks on vulnerable web servers to deploy web shell backdoors in a joint report issued with the Australian Signals Directorate (ASD) in April 2020.
“Malicious cyber actors have increasingly leveraged web shells to gain or maintain access on victim networks,” the NSA said.
Also Read: Computer Misuse Act Singapore: The Truth And Its Offenses
The NSA has a dedicated GitHub repository with tools that organizations and admins can use to detect and block web shell threats including: