KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft has improved password spray detection in Azure Active Directory (Azure AD) by doubling the number of compromised accounts it detects using a new machine learning (ML) system.
“This new machine learning detection yields a 100 percent increase in recall, meaning it detects twice the number of compromised accounts of the previous algorithm,” said Alex Weinert, Director of Identity Security at Microsoft.
“It does this while maintaining the previous algorithm’s amazing 98 percent precision—meaning if this algorithm says an account fell to password spray, it’s almost certain that it did.”
Microsoft built a heuristic engine focused on detecting password spray attack, which helped the company to spot and alert tenants of hundreds of thousands of attacks each month (350,000 in April 2018).
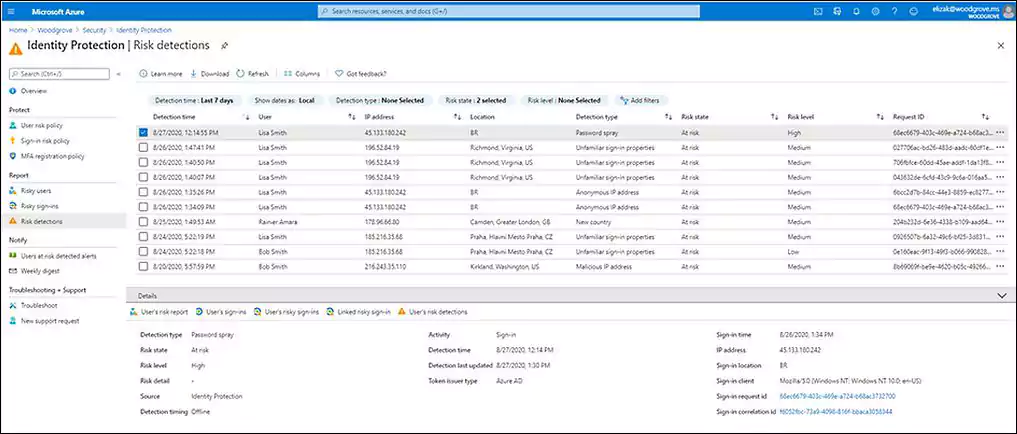
This detection engine provides Azure AD customers with access to the Identity Protection feature (via an Azure AD Premium P2 license) notifications when a passwords spray attack is detected.
Also Read: Basic Info On How Long To Keep Accounting Records In Singapore?
Now, the company has improved the credential compromise detection engine for Azure AD Identity Protection customers with a new machine learning system that uses known attack patterns and additional data to boost attack detection efficiency.
The data used by the new ML mode used to boost credential compromise detection capabilities includes but it’s not limited to various account behavior deviation signals such as unfamiliar sign-in properties and IP reputation.
“This new password spray detection is a great example of how we use intelligence gained across Microsoft’s identity systems to continuously expand and improve our protections—which you can use to automate processes in Azure AD Conditional Access, in Azure Sentinel, or through the APIs for anything you can imagine,” Weinert added.
Threat actors launch password spray attacks via large botnets to trying to brute-force the accounts of one or more organizations by matching the usernames with a shortlist of common (usually weak) passwords, allowing them to hide failed attempts using different IP addresses.
This also enables them to defeat automated defenses designed to block multiple failed login attempts such as malicious IP blocking and password lockout.
Azure AD Password Protection was launched in April 2019 (in public preview since September 2019) to reduce the risks behind password spray attacks by blocking users from choosing easy to guess passwords, drastically reducing the success rate of such attacks to about 1% says Weinert.
“Each color tracks a different password hash for login attempts with incorrect passwords in Azure Active Directory (Azure AD). Looking across millions of tenants, we can see the pattern of a password spray attack,” Weinert explained.
Also Read: Deemed Consent PDPA: How Do Businesses Comply?
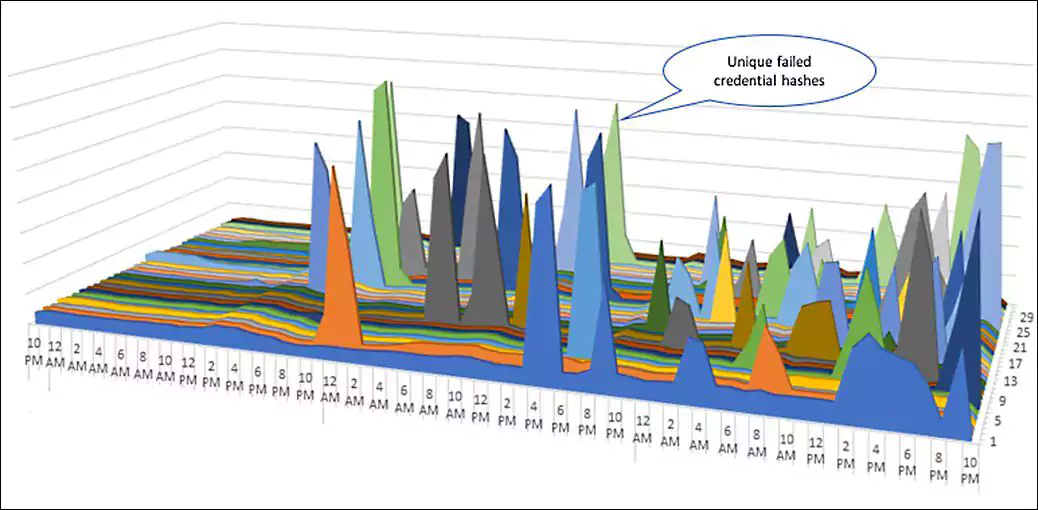
“Normally the graph would be flat and evenly dispersed as you see on the left side. The huge elevation of a single hash failing across many accounts indicates a single password being attempted against hundreds of thousands of usernames from many tenants—a password spray attack in progress.”
To get started with Azure AD Password Protection, you have to sign into Azure Portal as a global administrator, navigate to Azure Active Directory > Authentication methods, where you can manage Password protection.
Customers with access to Azure AD Identity Protection can access the new risk detection reports in the portal and using the APIs for Identity Protection.