KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft has released Sysmon 13 with a new security feature that detects if a process has been tampered using process hollowing or process herpaderping techniques.
To evade detection by security software, threat actors inject malicious code into a legitimate Windows process. This tactic allows the malware to execute, but in Task Manager, it appears as a standard Windows process running in the background.
Process hollowing is when malware launches a legitimate process in a suspended state and replaces legitimate code in the process with malicious code. This malicious code is then executed by the process, with whatever permissions are assigned to the process.
Process herpaderping is a more advanced technique where malware modifies its image on the disk to look like legitimate software after the malware is loaded. When security software scans the on-disk file, it will see a harmless file while the malicious code runs in memory.
Numerous malware infections use process tampering techniques to evade detection, including the Mailto/defray777 ransomware, TrickBot, and BazarBackdoor.
Also Read: Website Ownership Laws: Your Rights And What These Protect
To enable the process tampering detection feature, administrators need to add the ‘ProcessTampering’ configuration option to a configuration file. Sysmon will just monitor basic events such as process creation and file time changes without a configuration file.
This new directive has been added to the Sysmon 4.50 schema, which can be viewed by running the sysmon -s command.
For a very basic setup that will enable process tampering detection, you can use the configuration file below:
<Sysmon schemaversion="4.50">
<EventFiltering>
<RuleGroup name="" groupRelation="or">
<ProcessTampering onmatch="exclude">
</ProcessTampering>
</RuleGroup>
</EventFiltering>
</Sysmon>
To start Sysmon and direct it to use the above configuration file, you would execute the sysmon -i and pass the configuration file’s name. In our example, the configuration file’s name is sysmon.conf, so we would use the following command.
sysmon -i sysmon.confOnce started, Sysmon will install its driver and begin collecting data quietly in the background.
All Sysmon events will be logged to ‘Applications and Services Logs/Microsoft/Windows/Sysmon/Operational‘ in the Event Viewer.
With the ProcessTampering feature enabled, when process hollowing or process herpaderping is detected, Sysmon will generate an ‘Event 25 – Process Tampering’ entry in Event Viewer. For example, when testing this feature using this process hollowing test, you can see in the event below that svchost.exe was affected.
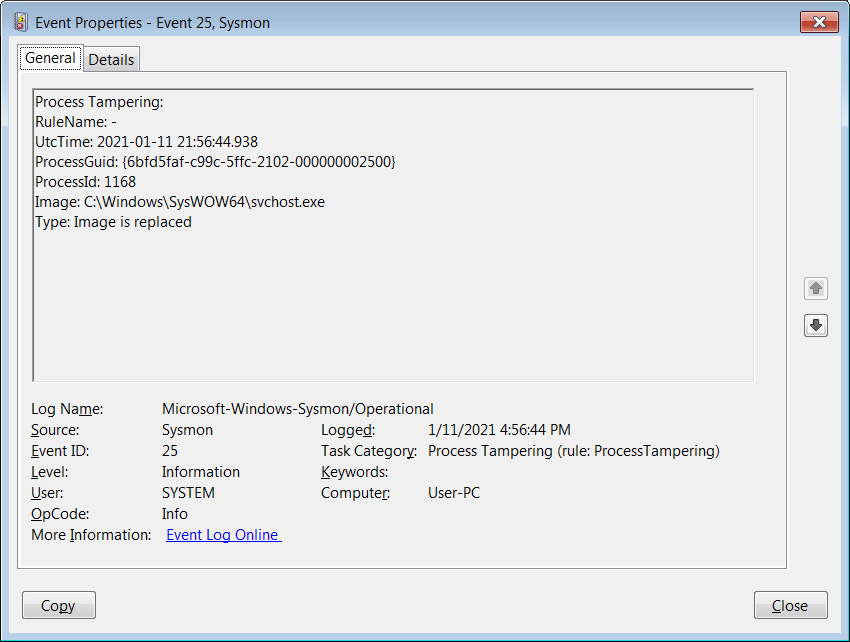
BleepingComputer noticed frequent detections for harmless executables related to Chrome, Opera, Firefox, Fiddler, Microsoft Edge, and various Setup programs when testing this feature.
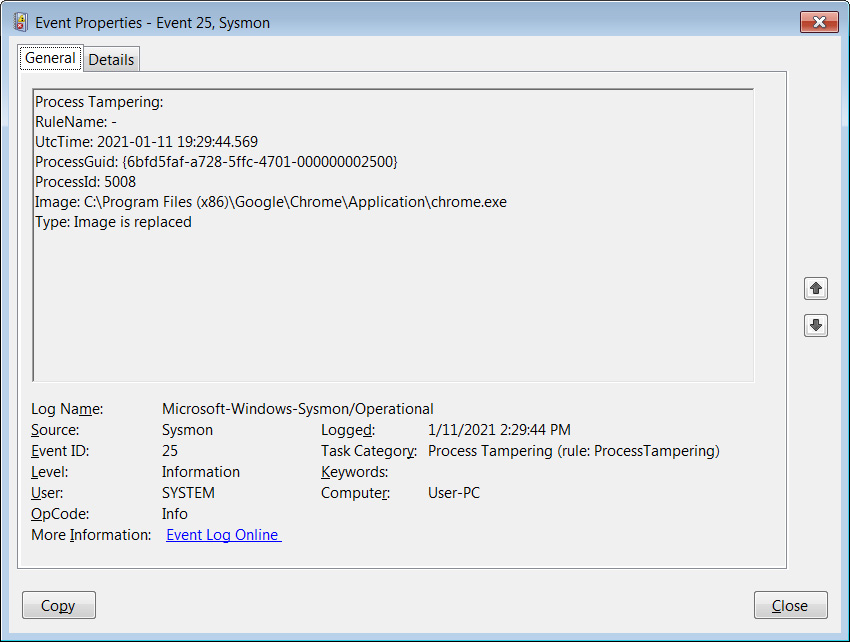
Unfortunately, other tests conducted by BleepingComputer using the latest TrickBot and BazarLoader could not trigger events.
For those who want to learn more about Sysmon, it is strongly recommended that you read the documentation on Sysinternals’ site and play around with the various configuration options.
There is no better way to learn how to use this program then by creating configuration files and see what events are written to the event log.
Users can obtain more information about the various directives used in Sysmon by entering the sysmon.exe -s all command.
Also Read: Best Privacy Certification: 3 Simple Steps On How To Achieve
If you want to use a premade Sysmon config file designed to monitor malicious traffic and threats, you can use SwiftOnSecurity’s Sysmon configuration file.