KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft says that the end goal of the SolarWinds supply chain compromise was to pivot to the victims’ cloud assets after deploying the Sunburst/Solorigate backdoor on their local networks.
No new tactics, techniques, and procedures (TTPs) were shared in a blog post published on Monday to provide Microsoft 365 Defender users with threat hunting techniques for investigating Sunburst attacks.
However, Microsoft also shared another important bit of information: the end goal of the SolarWinds hackers’ attacks, something that was only hinted at previously.
As the Microsoft 365 Defender Team explains, after infiltrating a target’s network with the help of the Sunburst backdoor, the attackers’ goal is to gain access to the victims’ cloud assets.
“With this initial widespread foothold, the attackers can then pick and choose the specific organizations they want to continue operating within (while others remain an option at any point as long as the backdoor is installed and undetected),” Microsoft explains.
Also Read: A Look at the Risk Assessment Form Singapore Government Requires
“Based on our investigations, the next stages of the attack involve on-premises activity with the goal of off-premises access to cloud resources [..].”
Microsoft’s previous articles on the SolarWinds supply chain attack and National Security Agency (NSA) guidance also hinted at the fact that the attackers’ ultimate goal was to generate SAML (Security Assertion Markup Language) tokens to forge authentication tokens allowing access to cloud resources.
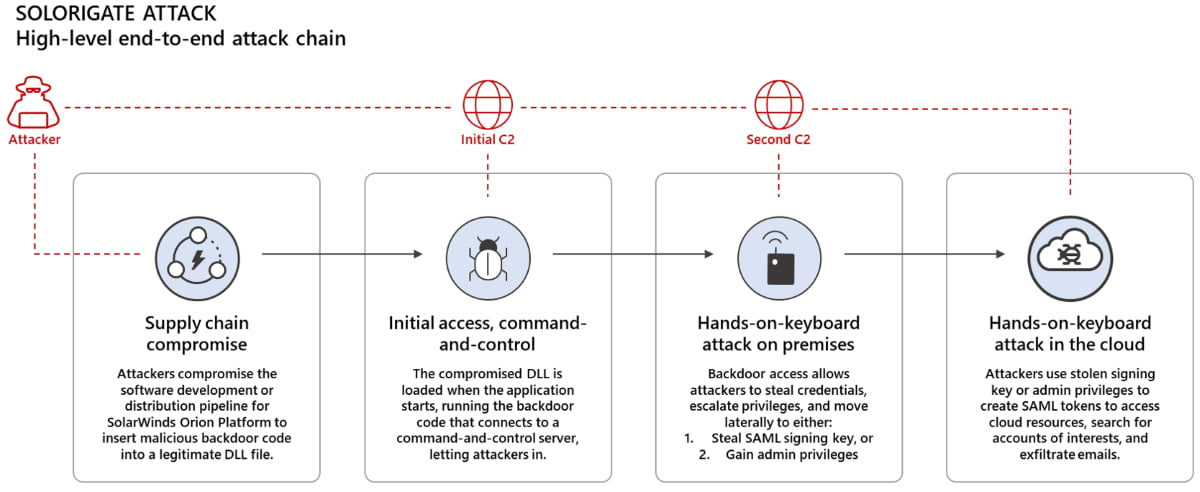
The threat actors behind the SolarWinds hack first had to compromise the SolarWinds Orion Platform build system and abuse it to deliver a backdoor injected as a legitimate DLL via the software update system.
Once the DLL is loaded after the application is started, the backdoor would reach out to its command-and-control server and allow the threat actors to infiltrate the network.
Next, they elevate privileges and move laterally through the victim’s network with the end goal of gaining admin privileges or stealing the (private) SAML signing key.
Once this happens, they forge trusted SAML tokens which allow them to access cloud assets and exfiltrate emails from accounts of interest.
Microsoft also detailed the step by step procedure used by the attackers to gain access to their victims’ cloud assets:
In its guidance highlighting SolarWinds hackers’ TTPs for pivoting to cloud resources, the NSA also shared mitigation measures against unauthorized cloud access which require making it difficult for threat actors to gain access to on-premise identity and federation services.
The NSA recommends enforcing multi-factor authentication, removing unnecessary apps with credentials, disabling legacy authentication, and using a FIPS-validate Hardware Security Module (HSM) to secure the private keys.
Search local and cloud logs for signs of suspicious tokens, as well as detecting indicators of compromise (IOCs) and auth mechanism abuse attempts can also be used by the tenant and the cloud service provider to spot attacks.
Also Read: How to Send Mass Email Without Showing Addresses: 2 Great Workarounds
Last week, the FBI also shared a TLP:WHITE private industry notification [PDF] with info on how system administrators and security professionals can determine if APT actors have exploited SolarWinds vulnerabilities on their systems.
DHS-CISA and cybersecurity firm Crowdstrike have also released free malicious activity detection tools to search for SAML token usage anomalies in audit logs and enumerate Azure tenant assigned privileges.