KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft Sentinel now comes with support for continuous GitHub threat monitoring, which helps keep track of potentially malicious events after ingesting GitHub enterprise repository logs.
Microsoft Sentinel (previously known as Azure Sentinel) is Redmond’s cloud-native SIEM (Security Information and Event Management) platform.
It uses artificial intelligence (AI) to analyze vast volumes of data, hunting for potential threat actor activity across enterprise environments.
“Today, together with Microsoft Sentinel, you can connect your enterprise-licensed GitHub repository environment to the Microsoft Sentinel workspace and ingest the GitHub audit log – tracking events such as new repository creation or deletion, counting the number of repository clones, and more,” Microsoft explained.
Also Read: 7 Principles of Personal Data Processing
“It is highly important to track the different activities in the company’s GitHub repository, to identify suspicious events, and to have the ability to investigate anomalies in the environment.”
The Microsoft Sentinel GitHub threat monitoring only works with GitHub enterprise licenses, and it comes with analytics rules to trigger alerts on suspicious events and one workbook for visualizing data.
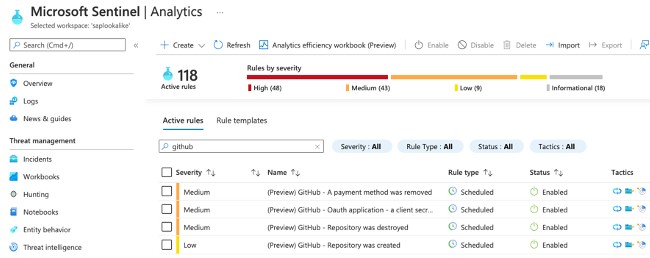
Alerts that will show up on the Microsoft Sentinel dashboard triggered by the new analytics rules include:
Using the workbook, security teams can also keep track of members being added and removed from a GitHub repo, newly added repositories, and how many times each repo was forked or cloned.
Also Read: 10 Simple and Useful Tips On Agreement Drafting Services
You can find detailed instructions on connecting enterprise-licensed GitHub repository to your Microsoft Sentinel workspace in this Tech Community blog post.
In December, Microsoft added an Apache Log4j Vulnerability Detection solution in public preview to help customers detect and investigate signals linked to the exploitation of Log4Shell vulnerabilities.
Microsoft Sentinel now also supports mapping analytics rules to MITRE ATT&CK techniques which helps narrow down search results.
In August, Microsoft updated its SIEM platform with new detections for possible ransomware attacks using the Fusion machine learning model.