KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft seized today dozens of malicious sites used by the Nickel China-based hacking group to target organizations in the US and 28 other countries worldwide.
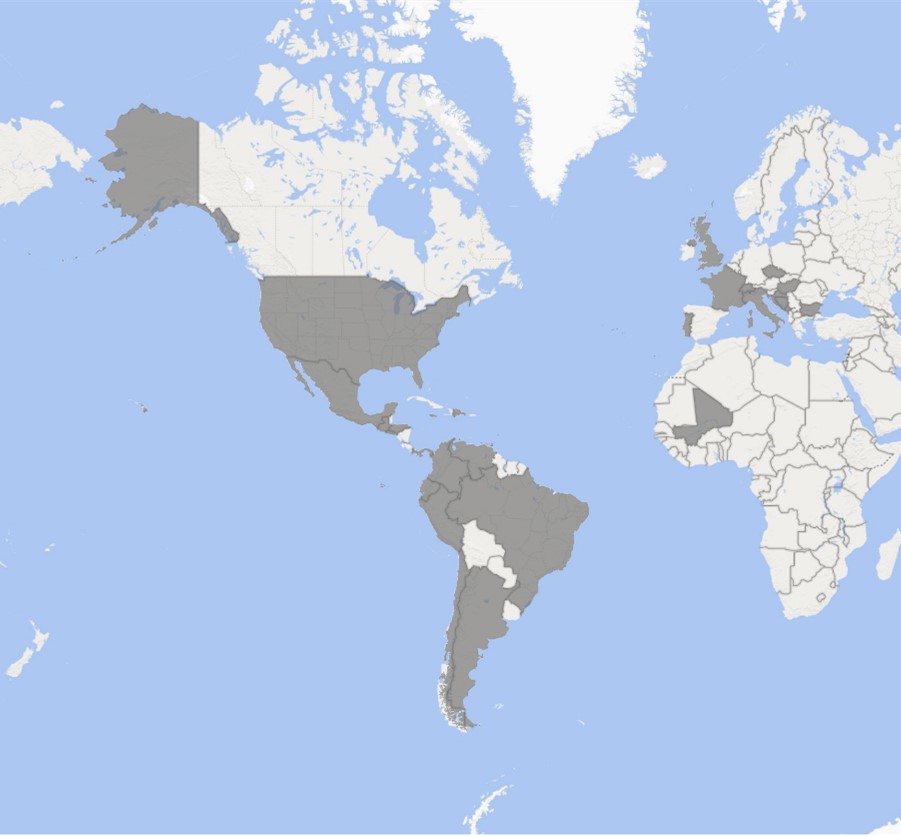
In their attacks, the Nickel threat actor (also tracked as KE3CHANG, APT15, Vixen Panda, Royal APT, and Playful Dragon) compromised the servers of government organizations, diplomatic entities, and non-governmental organizations (NGOs) across 29 countries, mainly from Europe and Latin America.
“Nickel has targeted organizations in both the private and public sectors, including diplomatic organizations and ministries of foreign affairs in North America, Central America, South America, the Caribbean, Europe and Africa,” said Tom Burt, Corporate Vice President for Customer Security & Trust at Microsoft.
Also Read: Compliance With Singapore Privacy Obligations; Made Easier!
“We believe these attacks were largely being used for intelligence gathering from government agencies, think tanks, and human rights organizations.”
Microsoft was able to take down Nickel’s infrastructure after the US District Court for the Eastern District of Virginia granted an order following a complaint filed on December 2 (the list of seized domains is available here).
According to the court’s order (which also contains the list of seized sites), the domains were redirected “to secure servers by changing the authoritative name servers to NS104a.microsoftintemetsafety.net and NS104b.microsoftintemetsafety.net.”
Microsoft’s Digital Crimes Unit (DCU) first spotted the threat group behind these malicious domains in 2016. Mandiant tracks them as Ke3chang and says they’ve been active since at least 2010.
Since 2019, it was observed targeting government entities across Latin America and Europe by Microsoft’s Threat Intelligence Center (MSTIC) and Digital Security Unit (DSU).
Nickel’s end goal is to deploy malware on compromised servers which enables its operators to monitor their victims’ activity, as well as collect data and exfiltrate it to servers under their control.
These Chinese-backed hackers use compromised third-party VPN (virtual private network) suppliers, credentials stolen in spear-phishing campaigns, and exploits targeting unpatched on-premises Exchange Server and SharePoint servers to hack into their targets’ networks.
More info on the hacking group’s malicious activity and indicators of compromise including domains used in their attacks can be found here.
“To date, in 24 lawsuits – five against nation-state actors – we’ve taken down more than 10,000 malicious websites used by cybercriminals and nearly 600 sites used by nation-state actors,” Burt added.
Also Read: Got A Notice of Data Breach? Don’t Panic!
“We have also successfully blocked the registration of 600,000 sites to get ahead of criminal actors that planned to use them maliciously in the future.”
In March 2020, the company took control of the U.S.-based infrastructure the Necurs spam botnet used to distribute malware payloads and infect millions of computers.
According to Microsoft, before being taken down, Necurs sent roughly 3.8 million spam messages to more than 40.6 million targets over just 58 days.
Redmond also sued the North Korean-linked Thallium cyber-espionage group in December 2019 and seized 50 domains part of the hacking group’s malicious domain infrastructure.
Microsoft’s Digital Crimes Unit also disrupted the Iran-backed APT35 (aka Charming Kitten, Phosphorus, or Ajax Security Team) threat actor in December 2019 after taking over servers used in its cyber attacks.
Previously, Microsoft filed 15 similar cases against the Russian-backed group Strontium (aka Fancy Bear or APT28) in August 2018, which led to the seizure of 91 malicious domains.