KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft has revealed the true scale of Russian-backed cyberattacks against Ukraine since the invasion, with hundreds of attempts from multiple Russian hacking groups targeting the country’s infrastructure and Ukrainian citizens.
These attacks also include the use of destructive malware designed to take down critical systems and disrupt civilians’ access to critical life services and reliable information.
“Starting just before the invasion, we have seen at least six separate Russia-aligned nation-state actors launch more than 237 operations against Ukraine – including destructive attacks that are ongoing and threaten civilian welfare,” said Tom Burt, Microsoft’s corporate vice president for customer security and trust.
“The destructive attacks have also been accompanied by broad espionage and intelligence activities. [..] We have also observed limited espionage attack activity involving other NATO member states, and some disinformation activity.”
The Microsoft Threat Intelligence Center (MSTIC) observed [PDF] threat groups linked to the GRU, SVR, and FSB Russian intelligence services (including APT28, Sandworm, Gamaredon, EnergeticBear, Turla, DEV-0586, and UNC2452/2652) pre-positioning for conflict and intensifying their attacks against Ukraine and its allies starting with March 2021.
Also Read: The FREE Guide To The 9 Obligations Of PDPA
Microsoft also noticed a direct link between cyberattacks and military operations, with the timing between hacking attempts and breaches closely matching that of missile strikes and sieges coordinated by the Russian military.
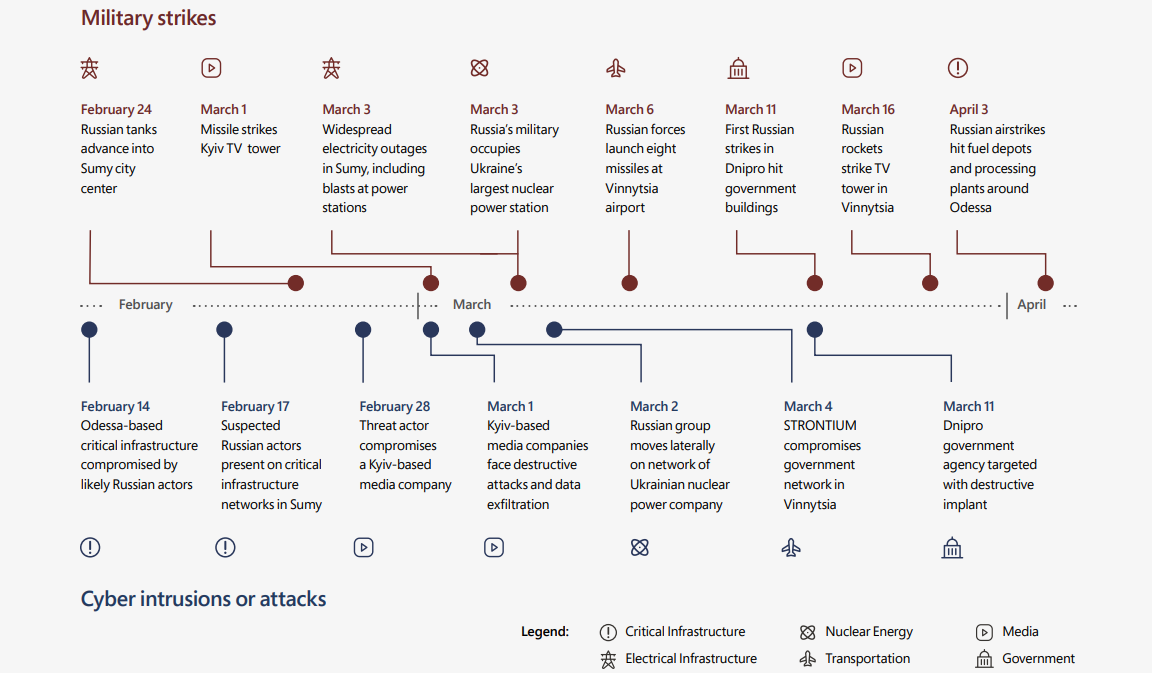
Among the destructive attacks it observed (almost 40 between February 23 and April 8) against dozens of organizations in Ukraine, Microsoft says 32% directly targeted Ukrainian government organizations, and over 40% were aimed at critical infrastructure organizations.
Microsoft has seen multiple malware families leveraged by Russian threat actors for destructive activity against Ukrainian targets, including WhisperGate/WhisperKill, FoxBlade (aka HermeticWiper), SonicVote (aka HermeticRansom), CaddyWiper, DesertBlade, Industroyer2, Lasainraw (aka IsaacWiper), and FiberLake (aka DoubleZero).
MSTIC has attributed three of them (i.e., FoxBlade, CaddyWiper, and Industroyer2) to Sandworm. Their members are believed to be military hackers part of Unit 74455 of the Russian GRU’s Main Center for Special Technologies (GTsST).
“WhisperGate, FoxBlade, DesertBlade, and CaddyWiper are all malware families that overwrite data and render machines unbootable. FiberLake is a .NET capability being used for data deletion,” the Microsoft Digital Security Unit (DSU) said [PDF].
“SonicVote is a file encryptor sometimes used together with FoxBlade. Industroyer2 specifically targets operational technology to achieve physical effects in industrial production and processes.”
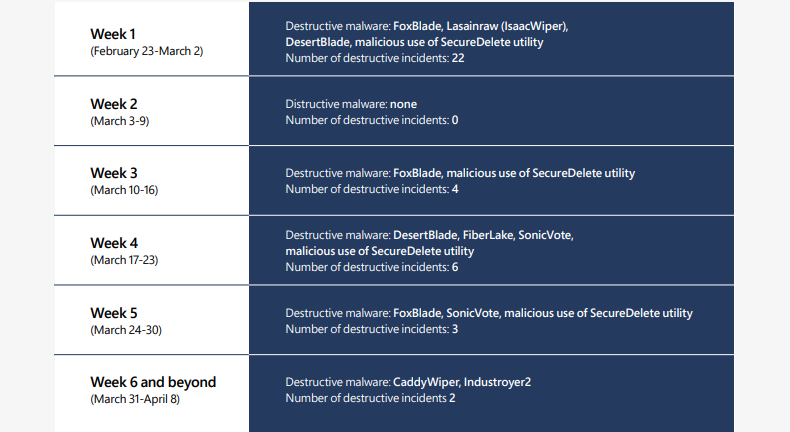
Microsoft has also found that the WhisperGate malware was used in data-wiping attacks against Ukraine in mid-January, before the February invasion, disguised as ransomware.
As Microsoft President and Vice-Chair Brad Smith said, these ongoing attacks with destructive malware against Ukrainian organizations and infrastructure “have been precisely targeted.”
They are part of a “massive wave of hybrid warfare,” as the Ukrainian Security Service (SSU) said, right before Russia’s invasion.
The highly targeted and precisely timed nature of this year’s Russian-backed cyberattacks against Ukraine is in stark contrast with the indiscriminate NotPetya worldwide malware assault that hit countries worldwide (including Ukraine) in 2017 and was also linked to the Russian GRU Sandworm hackers.
Also Read: Overview of the Personal Data Protection Act – SG
“While much of what Microsoft has observed to date suggests threat actors DEV0586 and IRIDIUM are operating with restraint in the execution of destructive attacks by limiting malware deployments to specific target networks,” Microsoft DSU added.
“However, Russia-aligned nation state actors are actively pursuing initial access to government and critical infrastructure organizations worldwide suggesting possible future targeting.”
Today’s report follows one published by the Google Threat Analysis Group (TAG) in late March, revealing phishing attacks coordinated by a Russian-based threat group targeting NATO and European military.
Another Google TAG report from early March about malicious activity linked to the Russian war in Ukraine exposed Russian, Chinese, and Belarus state hackers’ efforts to compromise Ukrainian and European organizations and officials.