KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft said today that Russian intelligence agencies have stepped up cyberattacks against governments of countries that have allied themselves with Ukraine after Russia’s invasion.
Since the start of the war, threat actors linked to several Russian intelligence services (including the GRU, SVR, and FSB) have attempted to breach entities in dozens of countries worldwide, prioritizing governments, according to Microsoft Threat Intelligence Center (MSTIC) analysts.
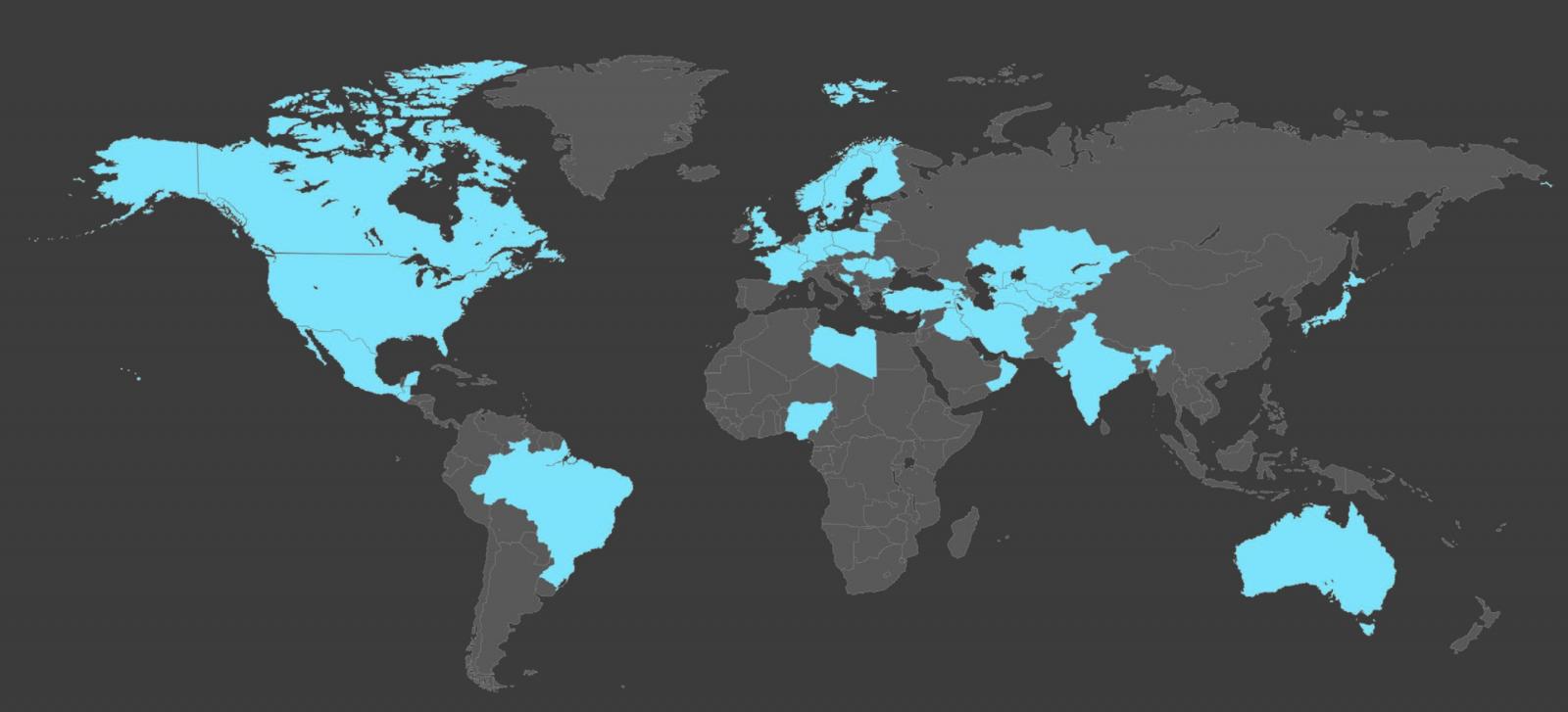
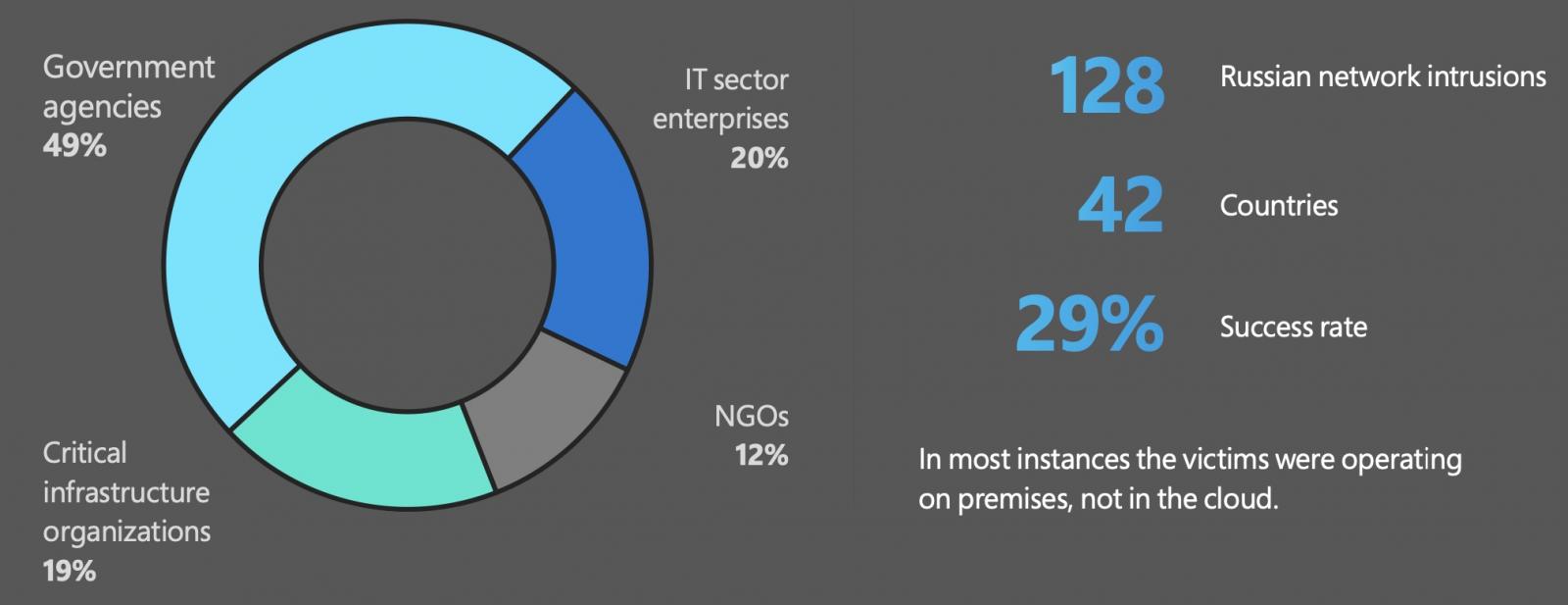
“MSTIC has detected Russian network intrusion efforts on 128 targets in 42 countries outside Ukraine,” said Microsoft’s President and Vice-Chair Brad Smith.
Also Read: Free PDPA Singapore Checklist 2020
“These represent a range of strategic espionage targets likely to be involved in direct or indirect support of Ukraine’s defense, 49 percent of which have been government agencies.”
The vast majority of these attacks are, as expected, primarily focused on obtaining sensitive information from government agencies in countries currently playing crucial roles in NATO’s and the West’s response to Russia’s war.
Non-governmental organizations (NGOs) were also targeted in another 12 percent of attacks, likely because of their involvement in supporting Ukrainian refugees and civilians as humanitarian groups or their role as think tanks focused on foreign policy.
The rest of the attacks mainly targeted organizations in critical economic or defense industry sectors, as well as energy or IT companies.
“While these targets are spread around the globe, 63 percent of this observed activity has involved NATO members,” Smith added (full report as PDF).
“Based on MSTIC’s observations, Russian cyber espionage efforts have focused on targets in the United States more than any other country, with American targets representing 12 percent of the global total outside Ukraine.”
Microsoft further revealed that, since Russia invaded Ukraine, Russian-backed threat actors have succeeded in 29% of their attacks. In a quarter of these intrusions, they were also able to exfiltrate stolen data.
Also Read: The FREE Guide To The 9 Obligations Of PDPA
In April, Microsoft published another report focused on Russian cyberattacks targeting Ukraine since the invasion.
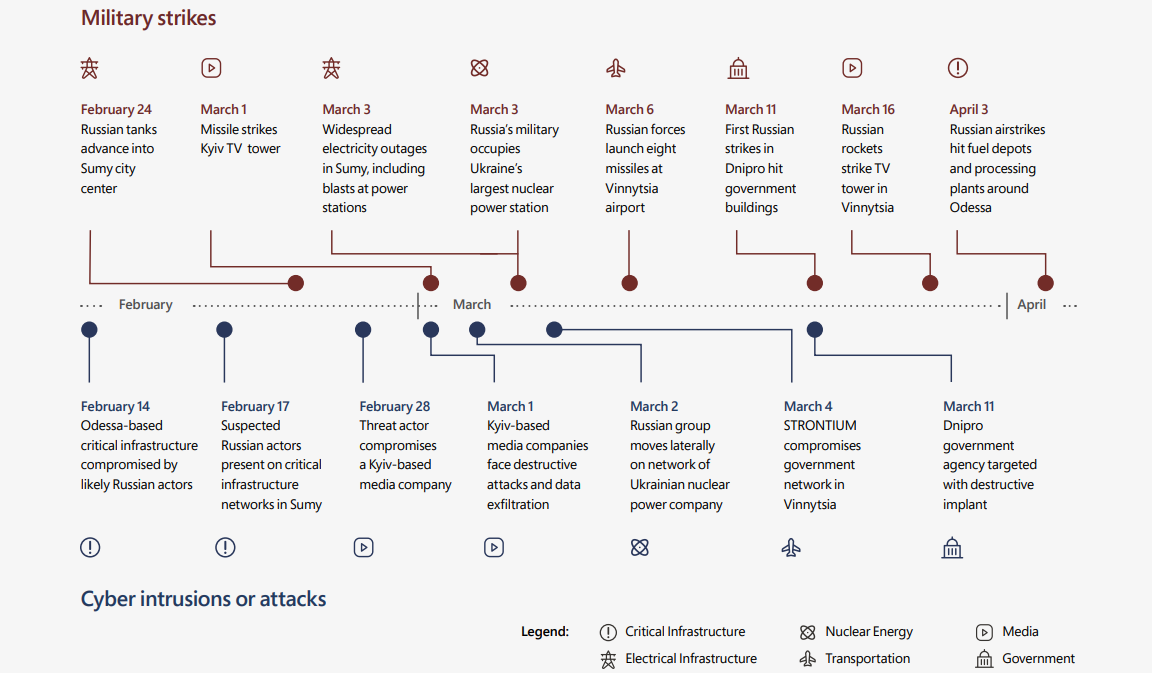
As the company revealed at the time, Russian-backed state hackers were behind hundreds of attempts to target the country’s infrastructure and citizens.
Their attacks also delivered destructive malware designed to take down critical systems and disrupt civilians’ access to reliable information and critical life services.
Among the observer destructive attacks (more than 30 between February 23 and April 8) against dozens of Ukrainian organizations, 32% directly targeted government agencies, while over 40% aimed to breach critical infrastructure.
Microsoft has also noticed direct links between military operations and cyberattacks, with the timing of hacking attempts closely matching that of Russian sieges and missile strikes.
In late March, the Google Threat Analysis Group (TAG) observed phishing attacks coordinated by the COLDRIVER Russian-based threat group against NATO and European military entities.
Another Google TAG report from early March with even more details on malicious activity linked to the Russian war in Ukraine also exposed Russian, Chinese, and Belarus state hackers’ efforts to compromise Ukrainian and European orgs and officials.
“The Russian invasion relies in part on a cyber strategy that includes at least three distinct and sometimes coordinated efforts—destructive cyberattacks within Ukraine, network penetration and espionage outside Ukraine, and cyber influence operations targeting people around the world,” Smith added.
“This war pits Russia, a major cyber-power, not just against an alliance of countries. The cyber defense of Ukraine relies critically on a coalition of countries, companies, and NGOs.”