KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







While Microsoft announced earlier this year that it would block VBA macros on downloaded documents by default, Redmond said on Thursday that it will roll back this change based on “feedback” until further notice.
The company has also failed to explain the reason behind this decision and is yet to publicly inform customers that VBA macros embedded in malicious Office documents will no longer be blocked automatically in Access, Excel, PowerPoint, Visio, and Word.
“Based on feedback, we’re rolling back this change from Current Channel,” the company notified admins in the Microsoft 365 message center (under MC393185 or MC322553) on Thursday.
“We appreciate the feedback we’ve received so far, and we’re working to make improvements in this experience. We’ll provide another update when we’re ready to release again to Current Channel. Thank you.”
The change began rolling out in Version 2203, starting with Current Channel (Preview) in early April 2022, with general availability to be reached in June 2022, as BleepingComputer previously reported.
Also Read: A Look at the Risk Assessment Form Singapore Government Requires
This was a welcome and highly expected change, given that VBA macros are a popular method to push a wide range of malware strains (including Emotet, TrickBot, Qbot, and Dridex) via phishing attacks with malicious Office document attachments.
With VBA macros blocked by default, everyone was expecting attacks that delivered malware (such as information-stealing trojans and malicious tools used by ransomware groups) to be automatically thwarted.
On systems where VBA macros aut0blocking is enabled, customers see a “SECURITY RISK: Microsoft has blocked macros from running because the source of this file is untrusted” security alert.
If clicked, the warning sends users to an article containing information about the security risks behind threat actors’ use of Office macros and instructions on enabling these macros if absolutely necessary.
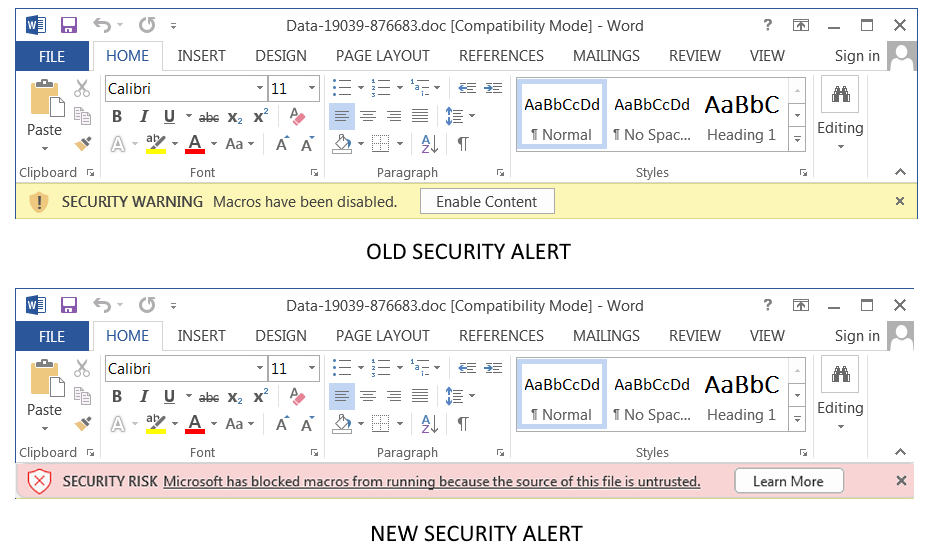
Microsoft’s customers were the first to notice that Microsoft rolled back this change in the Current Channel on Wednesday, with the old ‘Enable Editing’ or ‘Enable Content’ buttons shown at the top of downloaded Office documents with embedded macros.
“Is it just me or have Microsoft rolled this change back on the Current Channel?” one Microsoft Office user asked in the comments of Microsoft’s February blog post announcing that VBA macros will be disabled.
“It feels like something has undone this new default behaviour very recently… maybe Microsoft Defender is overruling the block?”
“Based on feedback received, a rollback has started. An update about the rollback is in progress,” replied Angela Robertson, a Principal GPM for Identity and Security on the Microsoft 365 Office team.
Also Read: CCTV Law Singapore Edition: Know Your Rights and Responsibilities
“I apologize for any inconvenience of the rollback starting before the update about the change was made available.”
Another customer complained about Microsoft’s “lack of communication” after announcing this change and asked the company to share more info on this rollback “elsewhere.”
“Your standard SMB and even mid-sized businesses are going to implode if this gets fully implemented in it’s current form,” the customer said.
“You seem to be catering to enterprises now that have very large teams of people to manage your products, and that’s simply not the case for most of the user base. It needs to be simplified before it’s released, and moreso, it needs to be effectively communicated.”
“Rolling back a recently implemented change in default behaviour without at least announcing the rollback is about to happen is very poor product management,” another added.
While Microsoft has not shared the negative feedback that led to the rollback of this change, users have reported that they are unable to find the Unblock button to remove the Mark-of-the-Web from downloaded files, making it impossible to enable macros.
Other admins felt that the decision was a problem for end-users who would find it burdensome to unblock files that they download every day, if not multiple times per day.
Update July 0, 03:57 EST: In response to our questions as to why they are rolling back this change, a spokesperson told us Microsoft “doesn’t have anything more to share.”