KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft has released a Linux version of the very popular Sysmon system monitoring utility for Windows, allowing Linux administrators to monitor devices for malicious activity.
For those not familiar with Sysmon (aka System Monitor), it is a Sysinternals tool that monitors a system for malicious activity and then logs any detected behavior into system log files.
Sysmon’s versatility comes from the ability to create custom configuration files that administrators can use to monitor for specific system events that may indicate malicious activity is occurring on the system.
Also Read: What You Need to Know About Singapore’s Data Sharing Arrangements
Today, Microsoft’s Mark Russinovich and a cofounder of the Sysinternals utility suite, announced that Microsoft had released Sysmon for Linux as an open-source project on GitHub.
Unlike Sysmon for Windows, Linux users will be required to compile the program themselves and ensure that they have all the required dependencies, with instructions provided on the project’s GitHub page.
It is important to note that to compile Sysmon, you must first also install the SysinternalsEBPF project.
Once Sysmon is compiled, you can see a help file by typing sudo ./sysmon -h, as shown in the screenshot below.
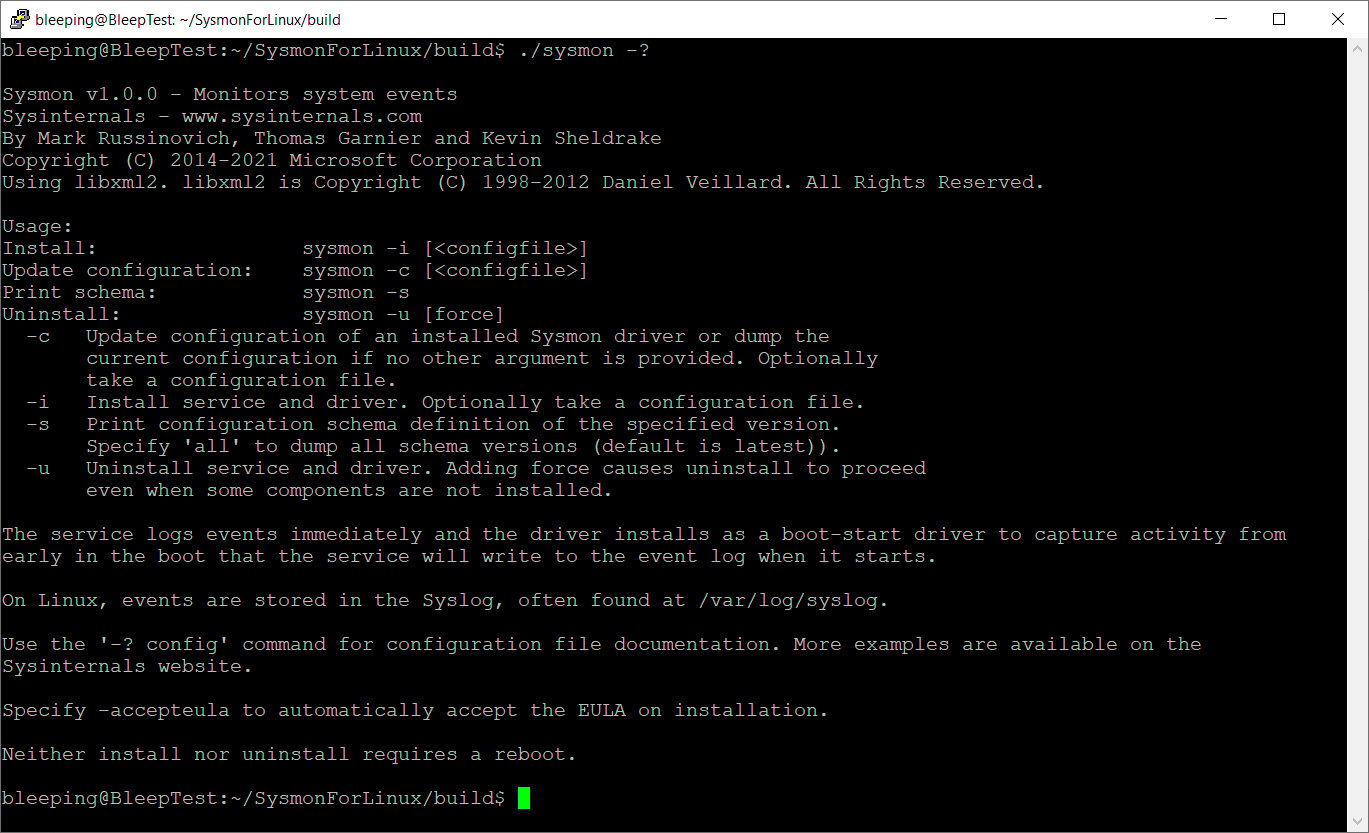
To use the program, you first need to accept the end-user license agreement with the following command:
sudo ./sysmon -accepteulaThen you can launch Sysmon with or without a configuration file using one of the following commands:
Without configuration file:
sudo ./sysmon -i
With configuration file:
sudo ./sysmon -i CONFIG_FILETo create your own Sysmon configuration file, you would need to use ./sysmon -s command to view the current version’s configuration schema and see what directives are available.
To learn more about creating a Sysmon configuration file, you can consult the official documentation or use SwiftOnSecurity’s template as an example.
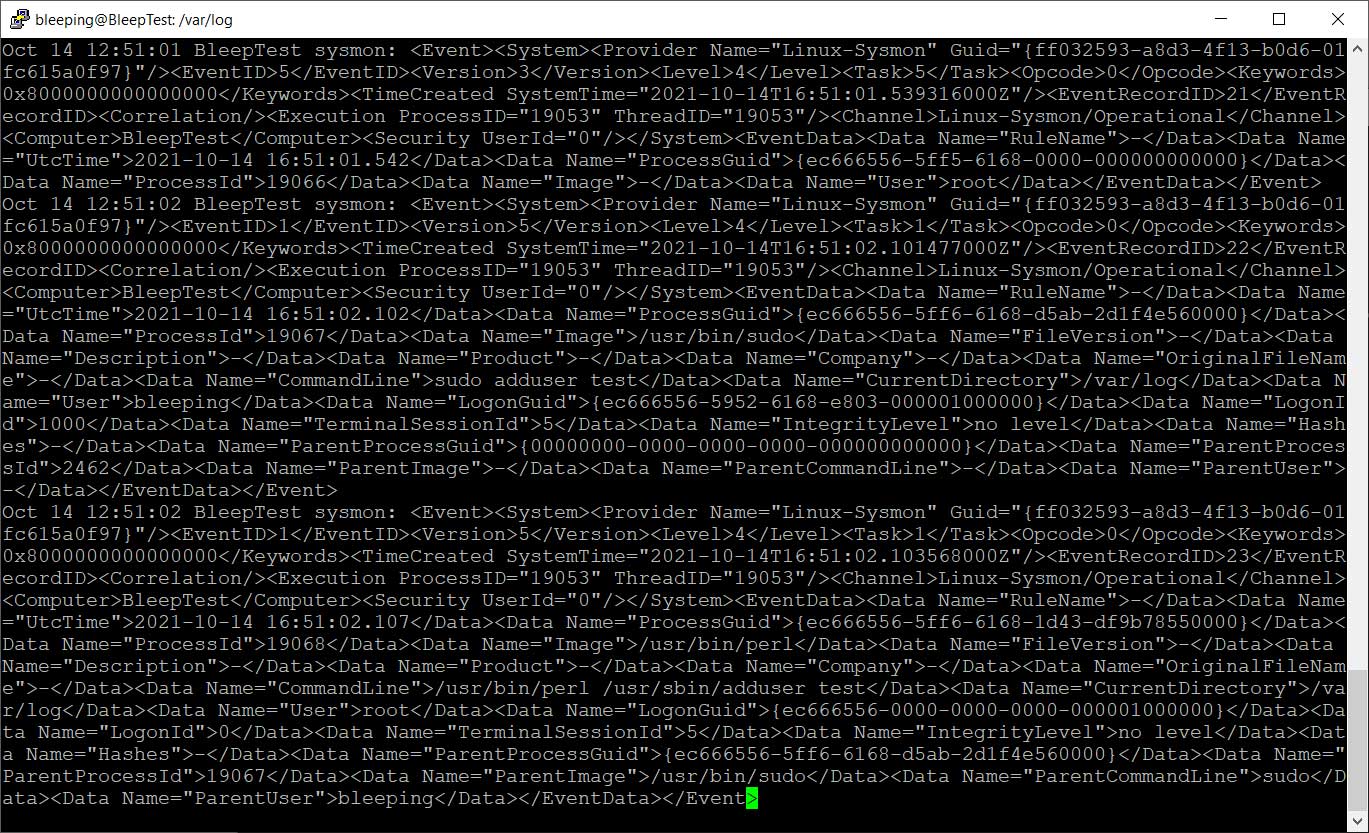
Once started, Sysmon will begin logging events to the /var/log/syslog file. If you did not specify a configuration file to restrict what is logged, you will find that your syslog file quickly grows as new processes are launched and terminated.
For example, in the screenshot below, you can see an event showing the ‘adduser’ command terminating after I used it to create a new user.
To make it easier to filter the logs for specific events, you can use the sysmonLogView utility to show the events you are looking for.
Also Read: PDPA Compliance for HR Managers in Singapore: A Must
The current events IDs that Sysmon for Linux is capable of logging are listed below:
As you can see, many of these events do not apply to Linux, such as the Registry or WMI events, so you will need to adjust your configuration accordingly.
Sysmon is a powerful tool widely used in Windows environments as part of an organization’s security toolbox.
With its addition to Linux, a whole new segment of system administrators can utilize it to provide free system monitoring for malicious activity.