KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






A handy tip was shared online this week, showing how you can use PowerShell to monitor changes to the Windows Registry over time.
As Windows updates, application installs, setting changes, and malware constantly makes changes to the Windows registry, this mode would allow you to quickly spot what was changed, allowing you to diagnose issues, remove malicious entries, and see what settings have been changed.
This week, popular security and technology Twitter account SwiftOnSecurity, tweeted how they would love to see a Windows Registry Editor mode that would display all registry entries that were not created by default.
In response to Swift’s tweet, Microsoft’s Principal Security Architect in Azure Security, Lee Holmes, tweeted an example of how you could do something similar in PowerShell.
Also Read: Top 3 Simple Data Backup Singapore and Recovery Methods
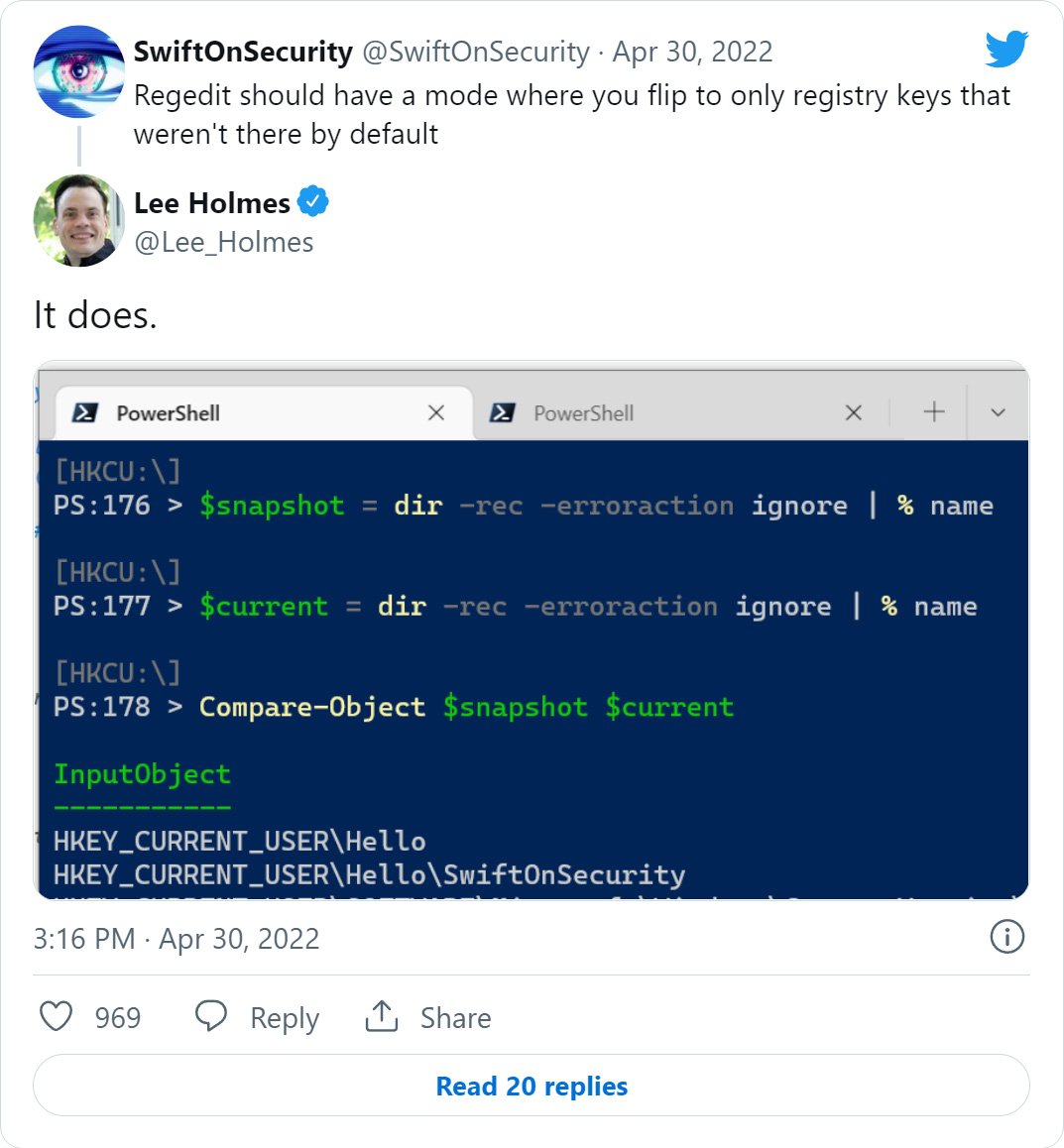
Holmes’ example shows how you can use PowerShell to list all existing Windows Registry keys and store them in a $snapshot variable. Then, at a later point in time, you create a snapshot of the current Registry keys and store them in the $current variable.
The example then compares the contents of these variables to determine what Registry keys were added since you took the first snapshot.
While this is not precisely what Swift was looking for, it points us in the right direction on how you can monitor Registry changes starting with a new install of Windows, or at least a point of time in your existing Windows installation.
Furthermore, as Holmes’ example uses variables that will be removed when a device reboots, it is better to store your Registry snapshots in files to compare them later, which we describe how to do below.
Using Holmes’ example, BleepingComputer played around with other ways of saving Windows Registry snapshots and found that modifying Holmes’ example to save snapshots to a file provides the greatest versatility.
By using files, you can create snapshots at various points in time to be compared with later snapshots. With files, you can also compare them to Registry snapshots created on other devices.
Also Read: What is Pseudonymisation: 5 Techniques and Its Best Practices
To start, you need to create a base snapshot of the current HKLM and HKCU Registry keys that you will compare to future snapshots. Ideally, but not necessary, you would generate these base snapshots right after you install Windows.
To create the base Windows Registry snapshots, you would execute the following PowerShell commands in a Windows PowerShell (Admin) prompt to make sure you can access all of the registry keys:
dir -rec -erroraction ignore HKLM:\ | % name > Base-HKLM.txt
dir -rec -erroraction ignore HKCU:\ | % name > Base-HKCU.txt
These commands will make the Base-HKLM.txt and Base-HKCU.txt snapshot files in the current folder.
In BleepingComputer’s tests on freshly installed versions of Windows 11 and Windows 10, these snapshots have the following sizes:
Windows 11 Registry snapshots:
| HKEY_LOCAL_MACHINE (HKLM): | 82 MB |
| HKEY_CURRENT_USER (HKCU): | 2.4 MB |
Windows 10 Registry snapshots:
| HKEY_LOCAL_MACHINE (HKLM): | 81 MB |
| HKEY_CURRENT_USER (HKCU): | 1.45 MB |
Once you have created your base snapshots, you can now install programs or use your computer as usual.
After some time, if you wish to compare the current Windows registry with your base snapshots, you can create new snapshots using these commands in an admin PowerShell prompt:
dir -rec -erroraction ignore HKLM:\ | % name > Current-HKLM-$(get-date -f yyyy-MM-dd).txt
dir -rec -erroraction ignore HKCU:\ | % name > Current-HKCU-$(get-date -f yyyy-MM-dd).txt
Note: the above commands will insert the date into the Current snapshot filenames so you can determine when the snapshot was created.
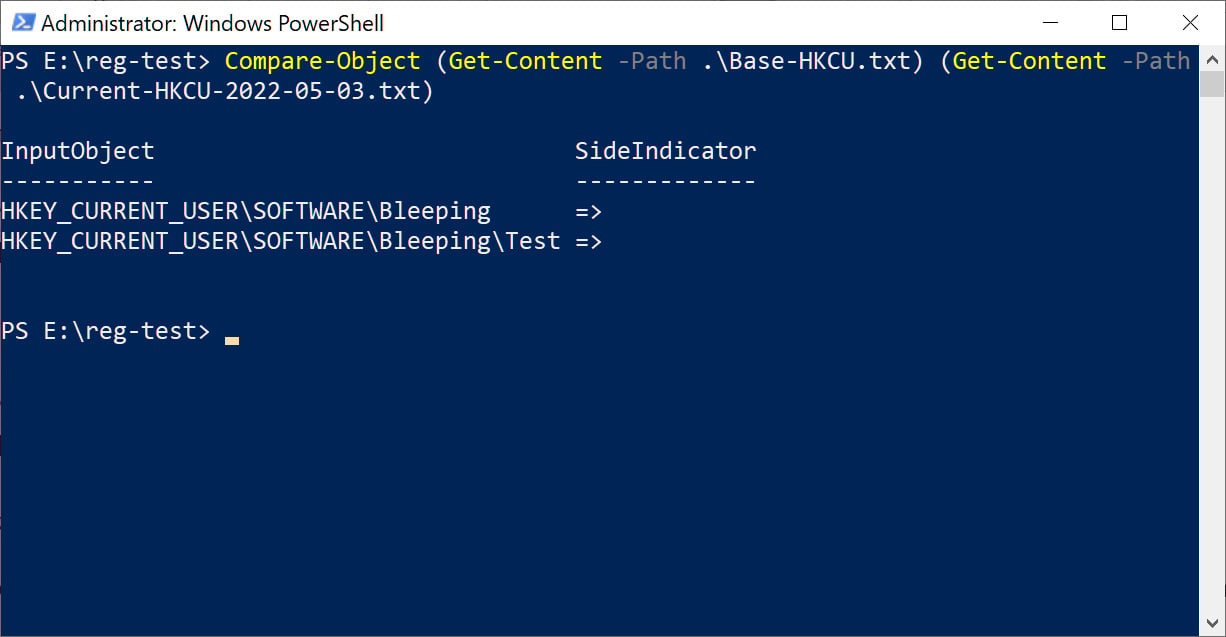
Now that you have both base snapshots and current snapshots created, you can compare them using the following PowerShell command:
Compare-Object (Get-Content -Path .\Base-HKCU.txt) (Get-Content -Path .\[current_snapshot_file_name])The Compare-Object command will compare the base snapshot with the current snapshot, and display what has been changed, as can be seen below. The SideIndicator column indicates which file contains the change.
It should be noted that this method only compares Windows Registry keys and does not compare its values, which are commonly changed by Windows settings and malware.
Exporting values would also dramatically increase the size of your snapshots and require a more complicated script to compare them properly. For example, the base HKCU snapshot with Registry values on a new Windows 10 install increases from 1.45 MB to 11.6 MB, an 8x times change.
However, comparing the Registry keys is still a helpful tool that admins can automate to better troubleshoot problems on devices they manage.