KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft now allows enterprise admins to re-enable the MSIX ms-appinstaller protocol handler disabled after Emotet abused it to deliver malicious Windows App Installer packages.
App Installer (also known as AppX Installer) allows users to install Windows applications directly from a web server using an MSIX package or App Installer file without first downloading the installers to their computer.
Microsoft disabled the ms-appinstaller scheme in response to reports of ongoing Emotet attacks exploiting a zero-day Windows AppX Installer spoofing vulnerability, forcing users to download the app packages to their device before installing them using App Installer.
“We recognize that this feature is critical for many enterprise organizations. We are taking the time to conduct thorough testing to ensure that re-enabling the protocol can be done in a secure manner,” Microsoft Program Manager Dian Hartono said when announcing the protocol’s shutdown.
“We are looking into introducing a Group Policy that would allow IT administrators to re-enable the protocol and control usage of it within their organizations.”
Also Read: March 2022 PDPC Incidents and Undertaking
According to an update from Hartono, Microsoft has finally managed to get a handle on the issue, and it now allows admins to toggle the protocol handler back on by installing the latest App Installer version (1.17.10751.0) and enabling a group policy.
On systems where the App Installer update cannot be deployed using the Internet-based installer, Microsoft also provides an offline version on the Microsoft Download Center (download link).
The App Installer feature will be re-enabled after downloading and deploying the Desktop App Installer policy and selecting “Enable App Installer ms-appinstaller protocol.”
You can do this through the Group Policy Editor by going to Computer Configuration > Administrative Templates > Windows Components > Desktop App Installer.
“You will need both the latest App Installer app and the Desktop App Installer policy to enabled in order to use the ms-appinstaller protocol for MSIX,” Hartono added.
Emotet started using malicious Windows AppX Installer packages camouflaged as Adobe PDF software for infecting Windows devices in phishing campaigns from early December 2021.
The botnet’s phishing emails used stolen reply-chain emails instructing the recipients to open PDFs related to previous conversations.
However, instead of opening the PDF, the embedded links were redirecting the recipients to that would launch the Windows App Installer and asking them to install a malicious “Adobe PDF Component.”
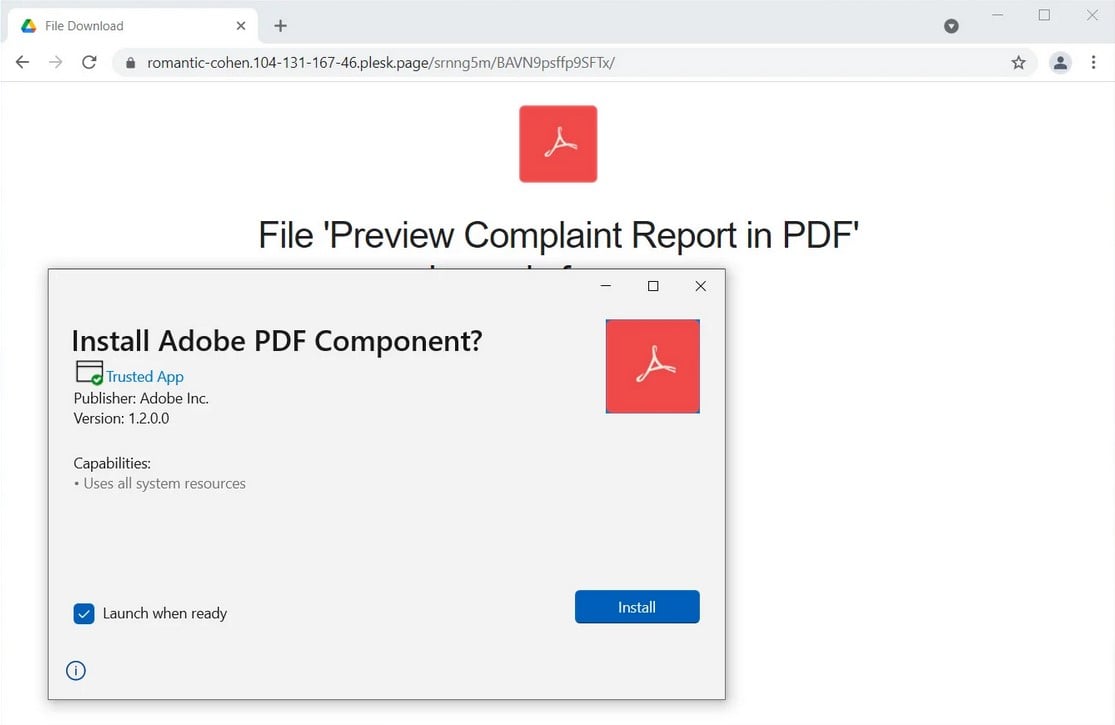
Although looking just like a legitimate Adobe app, App Installer downloaded and installed a malicious appxbundle hosted on Microsoft Azure after the targets clicked the Install button.
Also Read: CSA Cyber Trust and Cyber Essentials Marks: Why they matter
You can find more details, including the way Emotet abused the Windows App Installer vulnerability, in our previous report regarding the December campaign.
The same spoofing flaw was also exploited to distribute the BazarLoader malware using malicious packages hosted on Microsoft Azure via *.web.core.windows.net URLs.
“We have investigated reports of a spoofing vulnerability in AppX installer that affects Microsoft Windows,” Microsoft explained.
“Microsoft is aware of attacks that attempt to exploit this vulnerability by using specially crafted packages that include the malware family known as Emotet/Trickbot/Bazaloader.”