KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft has discovered new malware used by the Nobelium hacking group to deploy additional payloads and steal sensitive info from Active Directory Federation Services (AD FS) servers.
Nobelium, the threat actor behind last year’s SolarWinds supply-chain attack that led to the compromise of several US federal agencies, is the hacking division of the Russian Foreign Intelligence Service (SVR), commonly known as APT29, The Dukes, or Cozy Bear.
In April, the United States government formally accused the SVR division of carrying out “the broad-scope cyber espionage campaign.”
Cybersecurity firm Volexity also linked the attacks to APT29 operators based on tactics observed in previous incidents going back to 2018.
Also Read: What You Need to Know About Singapore’s Data Sharing Arrangements
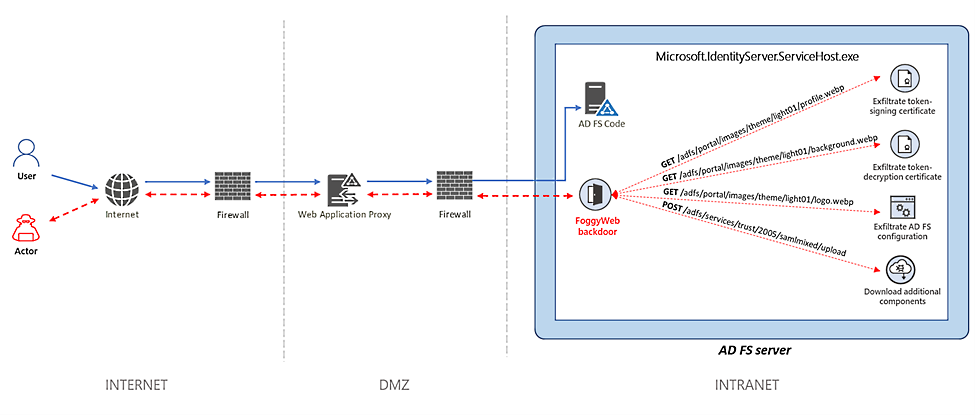
The malware, dubbed by Microsoft Threat Intelligence Center (MSTIC) researchers FoggyWeb, is a “passive and highly targeted” backdoor that abuses the Security Assertion Markup Language (SAML) token.
It is designed to help the attackers remotely exfiltrate sensitive information from compromised AD FS servers by configuring HTTP listeners for actor-defined URIs to intercept GET/POST requests sent to the AD FS server matching the custom URI patterns.
“NOBELIUM uses FoggyWeb to remotely exfiltrate the configuration database of compromised AD FS servers, decrypted token-signing certificate, and token-decryption certificate, as well as to download and execute additional components,” Microsoft said.
Also Read: PDPA Compliance for HR Managers in Singapore: A Must
“It can also receive additional malicious components from a command-and-control (C2) server and execute them on the compromised server.”
FoggyWeb works as a persistent backdoor that allows abuse of SAML tokens and configures HTTP listeners for actor-defined URIs to intercept GET/POST requests sent to the AD FS server that match the custom URI patterns.
The Russian state hackers have been observed using the FoggyWeb backdoor in the wild since April 2021.
Microsoft has already alerted notified customers that were targeted or compromised using this backdoor.
Organizations that believe they might’ve been breached or compromised are advised to:
In May, Microsoft researchers also revealed four other malware families used by Nobelium in their attacks: a downloader known as ‘BoomBox,’ an HTML attachment named ‘EnvyScout,’ a shellcode downloader and launcher named ‘VaporRage,’ and a loader known as ‘NativeZone,’
They detailed three more Nobelium malware strains used for layered persistence in March: a command-and-control backdoor dubbed ‘GoldMax,’ a persistence tool and malware dropper named ‘Sibot,” and an HTTP tracer tool tracked as ‘GoldFinder.’