KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





A massive malware campaign pushed the Java-based STRRAT remote access trojan (RAT), known for its data theft capabilities and the ability to fake ransomware attacks.
In a series of tweets, the Microsoft Security Intelligence team outlined how this “massive email campaign” spread the fake ransomware payloads using compromised email accounts.
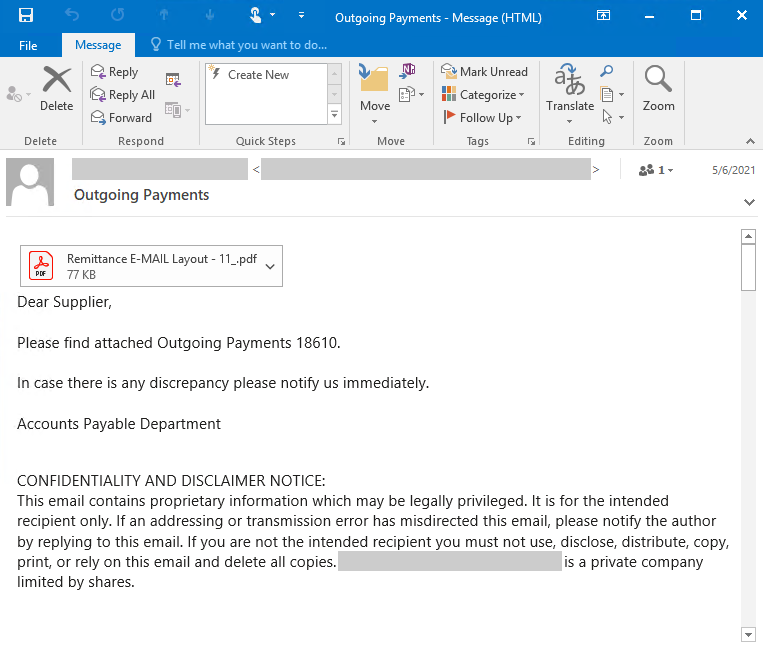
The spam emails lured the recipients into opening what looked like PDF attachments but instead were images that downloaded the RAT malware when clicked.
“The emails contained an image that posed as a PDF attachment but, when opened, connected to a malicious domain to download the STRRAT malware,” Microsoft said.https://www.ad-sandbox.com/static/html/sandbox.html
“This RAT is infamous for its ransomware-like behavior of appending the file name extension .crimson to files without actually encrypting them.”
Also Read: What You Should Know About the Data Protection Obligation Singapore
As the Microsoft Security Intelligence team mentioned in their tweets, the STRRAT malware is designed to fake a ransomware attack while stealing its victims’ data in the background.
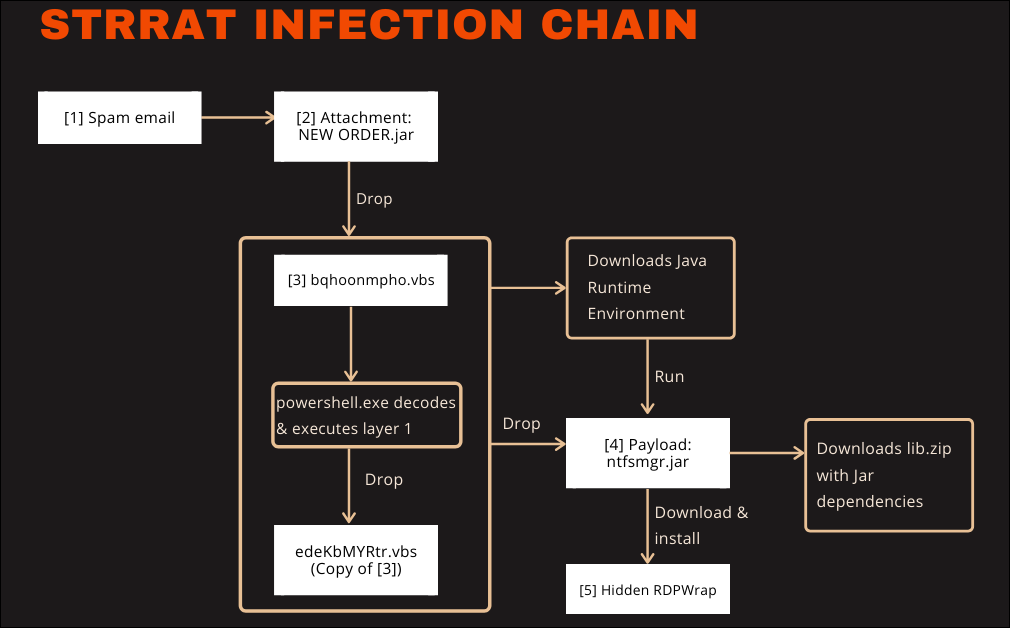
G DATA malware analyst Karsten Hahn said in June 2020 that the malware infects Windows devices via email campaigns pushing malicious JAR (Java ARchive) packages that deliver the finally RAT payload after going through two stages of VBScript scripts.
STRRAT logs keystrokes, allows its operators to run commands remotely and harvests sensitive information including credentials from email clients and browsers including Firefox, Internet Explorer, Chrome, Foxmail, Outlook, and Thunderbird.
It also provides attackers with remote access to the infected machine by installing the open-source RDP Wrapper Library (RDPWrap), enabling Remote Desktop Host support on compromised Windows systems.
However, the thing that makes it stand out from other RATs is the ransomware module that doesn’t encrypt any of the victims’ files but will only append the “.crimson” extension to files.
While this doesn’t block access to the files’ contents, some victims might still get fooled and, potentially, give in to attackers’ ransom demands.
“This might still work for extortion because such files cannot be opened anymore by double-clicking,” Hahn said.
“Windows associates the correct program to open files via their extension. If the extension is removed, the files can be opened as usual.”
As Microsoft found while analyzing last week’s massive STRRAT campaign, the malware developers haven’t stopped improving it, adding more obfuscation and expanding its modular architecture.
Also Read: The Difference Between GDPR And PDPA Under 10 Key Issues
Nonetheless, the RAT’s main functionality remained mostly untouched, as it is still used to steal browser and email client credentials, running remote commands or PowerShell scripts, and logging victims’ keystrokes.