KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft will soon begin disabling Excel 4.0 XLM macros by default in Microsoft 365 tenants to protect customers from malicious documents.
Excel 4.0 macros, or XLM macros, were first added to Excel in 1992 and allowed users to enter various commands into cells that are then executed to perform a task.
Also Read: The DNC Registry Singapore: 5 Things You Must Know
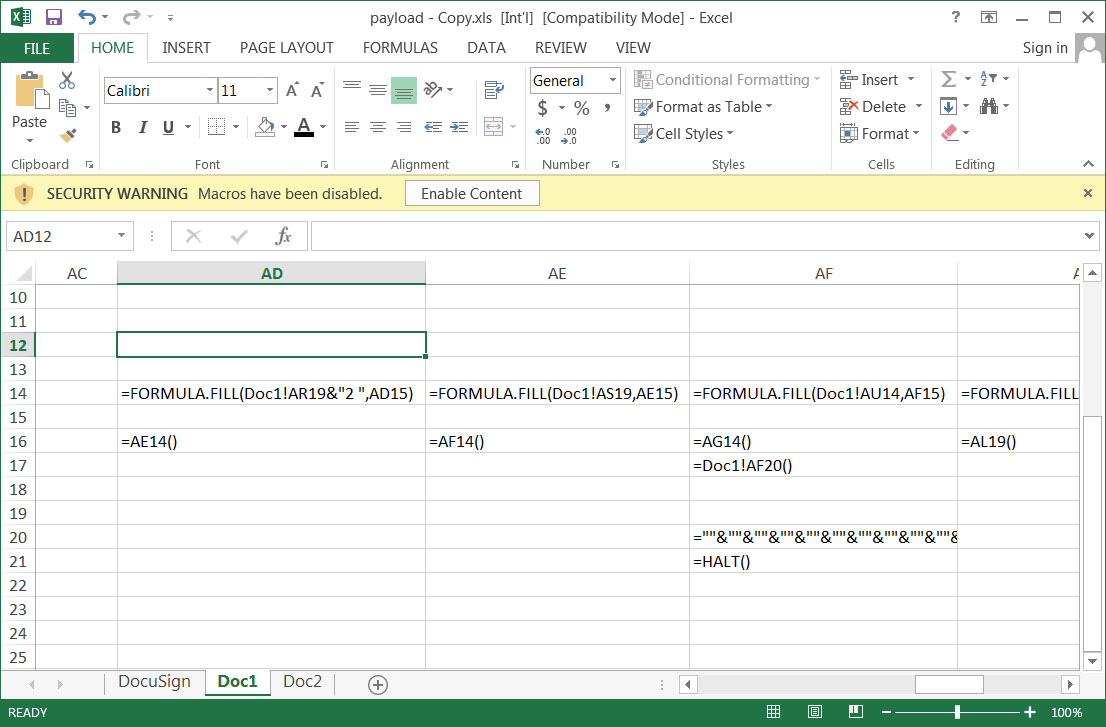
While VBA macros were introduced in Excel 5.0, threat actors continue to XLM macros twenty years later in malicious documents that download malware or perform other unwanted behavior.
Malicious campaigns utilizing Excel 4.0 XLM macros include ones for malware, such as TrickBot, Qbot, Dridex, Zloader, and many more.
Due to their continued abuse, Microsoft has been recommending users switch from and disable Excel 4.0 XLM macros for years in favor of VBA macros. This recommendation is because VBA macros support the Antimalware Scan Interface (AMSI), which can be used by security software to scan macros for malicious behavior.
To disable Excel 4.0 macros, Windows admins can use group policies to disable the feature, and users can disable it via the Excel Trust Center using the Enable XLM macros when VBA macros are enabledsetting.
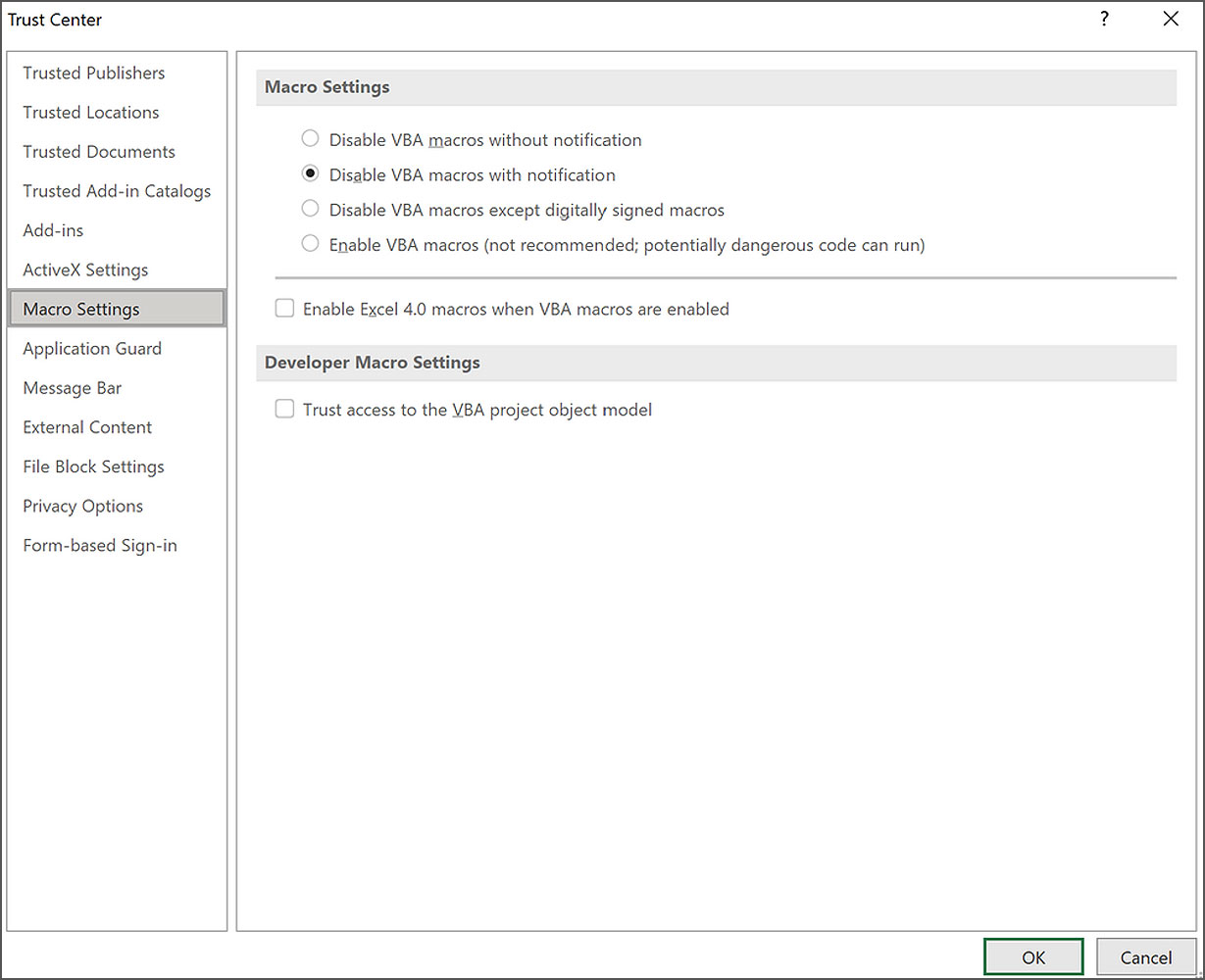
Instead of waiting for organizations to disable XLM macros on their own, Microsoft announced yesterday that they would be disabling Excel 4.0 macros by default starting in October in preview builds and then moving onto the current channel in November.
Also Read: How To Comply With PDPA: A Checklist For Businesses
“We are introducing a change to the Excel Trust Center Macro settings to provide a more secure experience for users by default. This new default behavior will disable Excel 4.0 macros,” explained an advisory in the Microsoft 365 message center.
Microsoft will begin disabling Excel 4.0 macros in all tenants using this rollout schedule:
Microsoft will not be making any changes for users who have manually configured this setting or configured it via group policies.
When the change rolls out, the Enable XLM macros when VBA macros are enabled setting will be unchecked by default, which disables XLM macros.
Microsoft states that users who wish to enable XLM macros after this rollout has finished can do so in the Excel Trust Center.
H/T Omri Segev Moyal