KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft says Iranian-backed hacking groups have increasingly attempted to compromise IT services companies this year to steal credentials they could use to breach the systems of downstream clients.
According to security analysts at Microsoft Threat Intelligence Center (MSTIC) and Digital Security Unit (DSU), this activity is part of a wider espionage objective to compromise entities of interest to the Iranian regime.
“This activity is notable because targeting third parties has the potential to exploit more sensitive organizations by taking advantage of trust and access in a supply chain,” Microsoft said.
Also Read: NDA Data Protection: The Importance, Its Meaning And Laws
“Microsoft has observed multiple Iranian threat actors targeting the IT services sector in attacks that aim to steal sign-in credentials belonging to downstream customer networks to enable further attacks.”
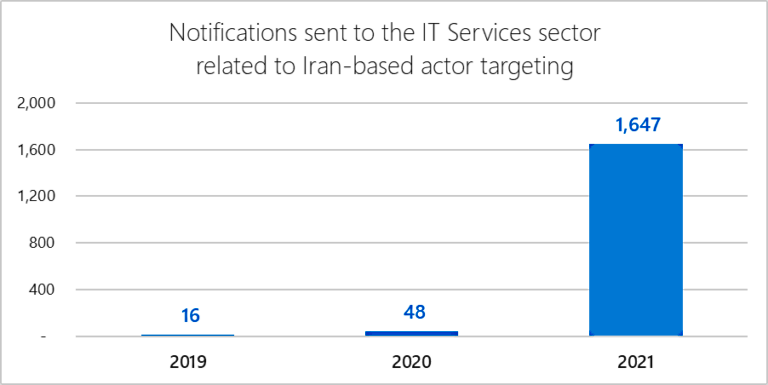
Redmond has sent over 1,600 notifications to alert more than 40 IT companies of hacking attempts coordinated by Iranian APT groups.
This shows a staggering increase compared to 2020 when Microsoft only sent only 48 notifications the whole year.
Most of these attacks are focused on Indian IT services firms, with some of them also targeting several companies based in Israel and the United Arab Emirates.
As Microsoft revealed, two Iranian hacking groups tracked as DEV-0228 and DEV-0056 successfully breached IT companies from Israel and Bahrain in July and September:
Iranian threat actors have been in the spotlight during the last two weeks, with several advisories and reports warning of Iranian activity targeting organizations worldwide.
Also Read: Invasion Of Privacy Elements And Its Legal Laws To Comply
US, UK, and Australian cybersecurity agencies warned Thursday of ongoing exploitation of Microsoft Exchange ProxyShell and Fortinet vulnerabilities linked to an Iranian-sponsored hacking group and ransomware attacks.
One day earlier, the Microsoft Threat Intelligence Center (MSTIC) revealed that six Iranian hacking groups have started deploying ransomware and exfiltrating data from victims’ systems starting in September 2020.
The FBI also warned in a TLP:AMBER private industry notification (PIN) of an Iranian threat actor attempting to buy stolen info associated with US and worldwide organizations from clear and dark web sources that could be used to breach their systems again.